Most Security Threats to Mobile Devices Come from Unsafe Browsing

Our AI-driven cybersecurity algorithms currently protect over 1 billion devices on end-user networks, where mobile phones make up over 36% of all connected devices. As we monitor malicious activities, we see that the largest security threats to mobile devices are web reputation threats, where users (or applications on their devices) try to access malicious websites.
Using a holistic, multi-layered cybersecurity approach for home networks was very useful during the pandemic, as many people started working from home and put their work devices at a larger risk. Our clients – large telecommunications companies that offer our security services to their end-users – saw us prevent millions of cyber attacks against their end-users every week.
Read Leonardas’ article about work from home security to get valuable tips for safer operations in a hybrid work arrangement.
As the pandemic recedes and people start getting into hybrid work arrangements, our attention turns to the significant number of devices that frequently step out of the protective environment. Mobile phones make up over a third of all connected devices in North America, and thanks to our data, we have a clear view of what preventable threats they are facing as they go online.
We are addressing mobile phone security by making CUJO AI services available on any network with CUJO AI On-The-Move.
Smart Phone Security Threats
Unsafe applications are some of the worst smart phone security issues. Users rarely review app permissions, and only power users think about monitoring app traffic to discover suspicious behavior. Free applications are perhaps the worst offenders because their owners need a source of income and therefore monetize their app user base in various ways, which include pervasive tracking, privacy violations, or even ad fraud. It is also possible for app developers to push new updates that include malicious SDKs, making app security a constant issue for smart phone users.
Nevertheless, our internal security monitoring data shows that unsafe browsing is the largest threat vector for mobile phones today, as close to 60% of threats to mobile device security come from browsing activities. While unsafe applications are an important element in phone security, especially for outdated or rooted devices, providing a safe browsing experience to mobile devices is paramount for good security.
Top Mobile Browsing Threats
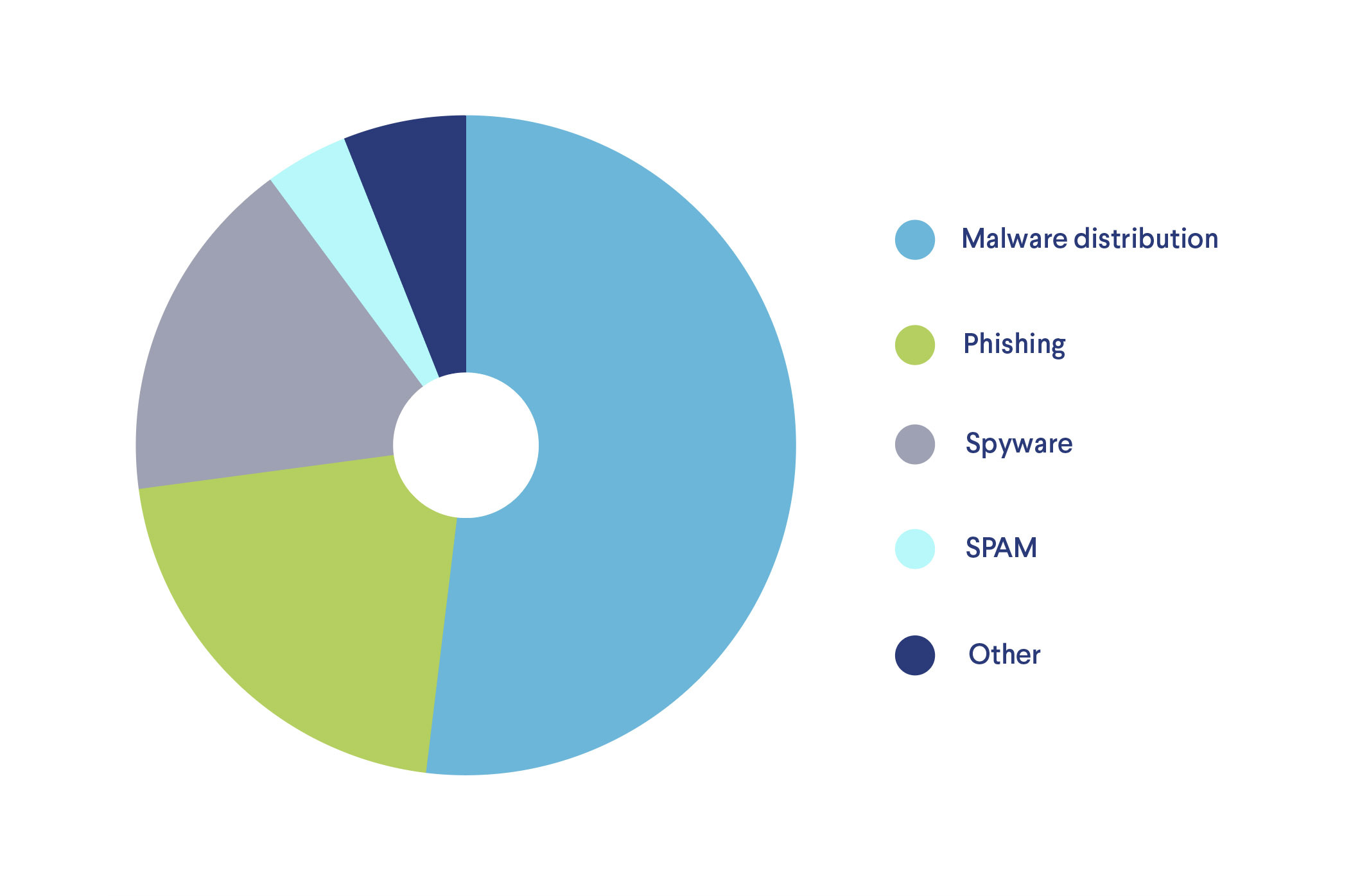
Threats to mobile security from unsafe browsing can be split into dozens of categories. What we see in our 1 billion+ device database is that just a few categories make up the majority of all mobile browsing threats. Some experts consider mobile browsing threats as a higher risk because people tend to use their devices constantly, even on unsafe networks.
Malware Distribution Sites
Most browsing security threats to mobile devices come from malware distribution websites. Our data shows malware sites using various embedded scripts, such as automated downloaders for ransomware, crypto miners, ransomware, and viruses that exploit, damage, or use devices to spread to other machines.
Traditional antivirus software and firewalls are very useful for combating these threats, but mobile users seldom use these protective measures. This is especially worrying in the case of Android users, who could have any of the 7,000+ Android devices in use at the moment, many of them running outdated OS, kernel, or vendor software versions.
Phishing and Social Engineering
Phishing is a practice of impersonating a legitimate authority, person, or organization to fool a user into revealing valuable information, compromising their security and finances. Phishing sites impersonate legitimate organizations, such as banks, tax services, cloud document environments (e.g., Google Docs or Office365), to name a few. Phishing sites incorporate many tactics, such as misspelled URL addresses and visual impersonation. It is one of the fastest-growing online threats due to the rapidly evolving deception tactics it employs, both in the technical and the ‘soft’ side (i.e., social engineering).
Protecting users from phishing sites requires a lot of ingenuity, as they are often very short-lived, while some crop up seasonally (e.g., during the tax season). Much like spam, phishing websites are usually detected and denylisted within days. Still, it is crucial to prevent their threat in that vulnerable window between when they appear and before they are blocklisted. This is where artificial intelligence becomes essential, as it can analyze and identify phishing websites by identifying suspicious content elements and examining a website in milliseconds.
Spyware
Spyware is a range of invasive malicious technologies and software that invade the victim’s privacy, spy on their activities, and leak or sell their information. Spyware is extremely dangerous to employers, as it might lead to unauthorized access to valuable information.
Mitigating the damage spyware can do to a mobile device is twofold. First, spyware usually connects to suspicious servers, which can be blocked by firewall settings. Secondly, once its code is added to malicious software signature databases, anti-malware applications can detect, quarantine, or remove it. Machine learning algorithms supplement these measures by rapidly detecting suspicious behavior that is out of character for a given device.
Spam
Online spam is usually a highly automated practice where links to illicit or malicious websites are spread via email, messaging applications, comment sections, online forums, and social media. Browsing websites from spam messages can open a device to many attack vectors, including phishing, cryptojacking, and malware.
Spam prevention has evolved over the years, and it is now a question of quickly analyzing the website with the help of constant streams of spam lists and automatically preventing devices from accessing them.
Adware
Adware is a set of malicious software and scripts that use unsuspecting victims for ad fraud. The techniques used in adware might range from taking over entire machines or stealing user clicks to redirecting users through ads, running software that injects ads into other websites, and gains money for the malicious actor.
Fighting adware on mobile devices is not always straightforward, as application developers might earn revenue by monetizing free software through ads. Nevertheless, most malicious adware behavior, such as ad redirects or attempts to take over a device, are quickly detected and stopped by our algorithms.
How Threats Changed in Recent Years
Phishing and other browsing threats are becoming harder for humans to detect, especially on mobile devices, which prioritize user experience over functionality. It is becoming harder for mobile users to manually check the security certificates, URLs, and other website attributes. It is also true that malicious actors have become more adept at impersonating legitimate sites.
We also see how attackers are adapting: malicious site owners are also moving towards HTTPS and are getting better at counterfeiting website certificates. That means users cannot be sure a website is legitimate by simply glancing at a certificate or, worse yet, the handy SSL-enabled lock sign in the browser.
Preventing Mobile Browsing Threats
There are some key aspects of basic cybersecurity that can improve the security of mobile devices, such as a good backup and update policy, use of MFA, and cybersecurity software solutions on the device or network level.
Protect yourself: Do not click ads in emails. Avoid clicking links from senders you do not trust. If you are ever contacted by an organization, do not click their links – enter the URL manually instead.
CUJO AI works at the network level to prevent millions of threats every day and reduces the risk from most unsafe browsing activities, and applications. Mobile phones are unique because they move across various networks: from poorly managed public Wi-Fi to private networks with good security protocols, e.g., enterprise work networks or home networks with CUJO AI provided by the ISP.
Preventing threats across different networks requires each of them to have good security and access protocols. We realize that this is highly unlikely, which is why we have developed On-The- Move – a mobile application (or SDK) that provides the same multi-layer cybersecurity that CUJO AI provides across any network.
Now, end-users can not only protect their home network and all of its devices but also to take the same level of protection across networks, both cellular and public or private Wi-Fi. Operators who already use CUJO AI can enhance native applications for mobile users to create an environment that is, on average, orders of magnitudes safer, especially for end-users on Android devices.
How AI Prevents Mobile Device Security Threats
Artificial intelligence (AI) is an evolving set of algorithms we use to identify, detect and prevent threats across the world wide web. It enhances our cybersecurity capabilities against all cyberthreats, including phishing, which had previously been a browsing threat that cybersecurity companies mostly ignored.
AI also creates an additional capability to monitor device activity, as our algorithms can identify devices and then detect when they are acting suspiciously. This makes AI extremely capable of preventing abuse and exploitation of vulnerabilities – even if a piece of malware managed to compromise a mobile device, Sentry prevents them from connecting to malicious servers or participating in botnets. Our system also checks for known threats and uses machine learning to detect inauthentic websites dynamically, closing the gap between when a new threat appears and when its signatures are pushed to virus databases.
AI-driven multi-layer security that CUJO AI provides covers both browsing activities and app connections, mitigating some threats when user-installed malicious applications start their activity.
Want to learn more about cybersecurity, emerging threats, as well as cutting-edge advancements in AI for telecommunications? Subscribe to the CUJO AI Newsletter below and follow us on LinkedIn.



