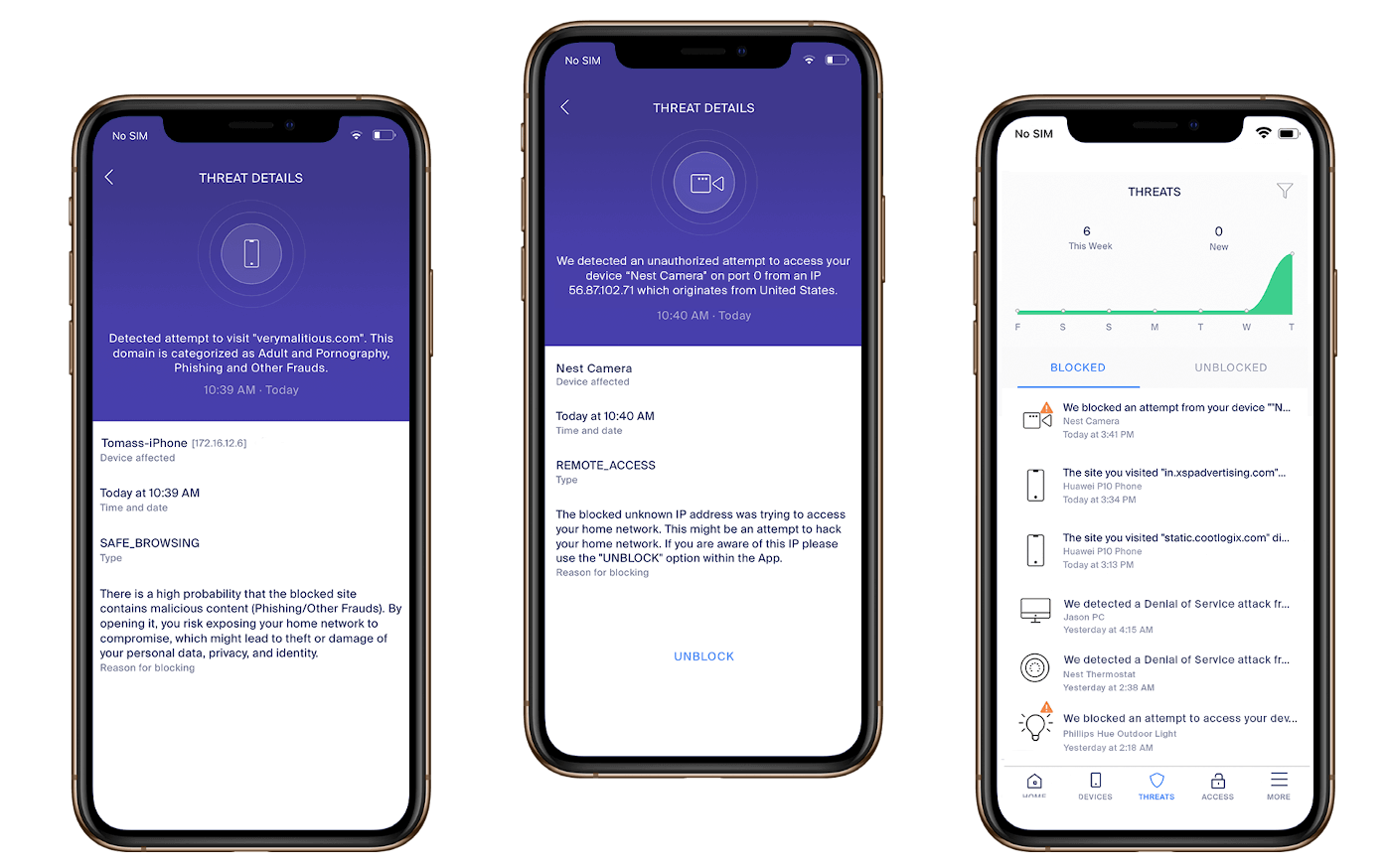
Sentry is a digital security service for consumers and businesses that uses Artificial Intelligence to detect and block threats directed at any device connected to the network, while respecting the privacy of the end-users.
Once deployed on any broadband router, CUJO AI Sentry requires no additional software to secure any and all computers, phones or IoT devices in the home. Sentry can also be deployed on the carrier’s native app to provide full protection to mobile devices outside the home network.