Latest Botnet Activity and Device Threats – IoT Chronicle, Summer 2021
This is an overview of the current botnet activity, device and web browsing threat landscapes. It is based on real-world data from CUJO AI’s extensive coverage of over 1 billion devices in 40 million networks. Researchers from CUJO AI Labs use anonymized data to detect and track emerging cybersecurity risks, the evolving tactics of malicious actors, as well as the most targeted popular device types.
These are the most prevalent threats we saw in the summer (June-August) 2021. Read our previous IoT Chronicle about IoT security threats.
Most Popular Types of Malicious URLs
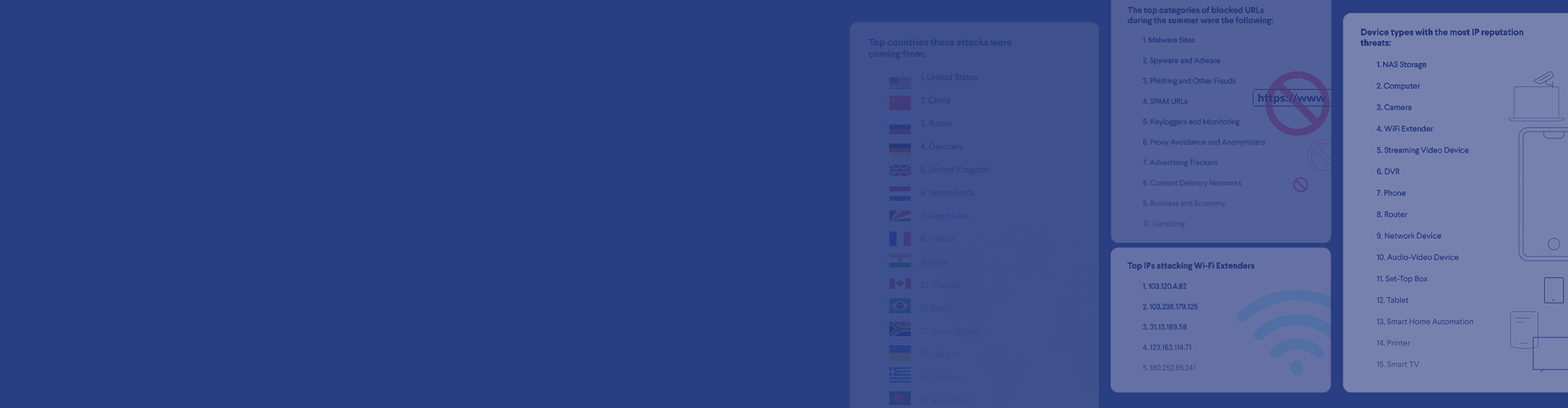
A key model in our multi-layer security solution is the CUJO AI Safe Browsing model, which combines machine learning and other state-of-the-art cybersecurity measures to prevent connections to and from disreputable IP addresses, spam, malware and other malicious websites.  The largest and arguably the most dangerous category of URLs CUJO AI Sentry has blocked in recent months are malware, spyware and adware websites. These two categories of malicious software are quite well known to the general public, yet our data shows that end-users still often try to access URLs of malware, spyware and adware distributors. Phishing threats and fraud are also in the top 3 categories, which is a worrisome sign. CUJO AI’s safe browsing models are trained to detect novel phishing websites, yet their short-lived existence and extreme impact on end-users’ livelihoods is a key problem in today’s cybersecurity.
The largest and arguably the most dangerous category of URLs CUJO AI Sentry has blocked in recent months are malware, spyware and adware websites. These two categories of malicious software are quite well known to the general public, yet our data shows that end-users still often try to access URLs of malware, spyware and adware distributors. Phishing threats and fraud are also in the top 3 categories, which is a worrisome sign. CUJO AI’s safe browsing models are trained to detect novel phishing websites, yet their short-lived existence and extreme impact on end-users’ livelihoods is a key problem in today’s cybersecurity.
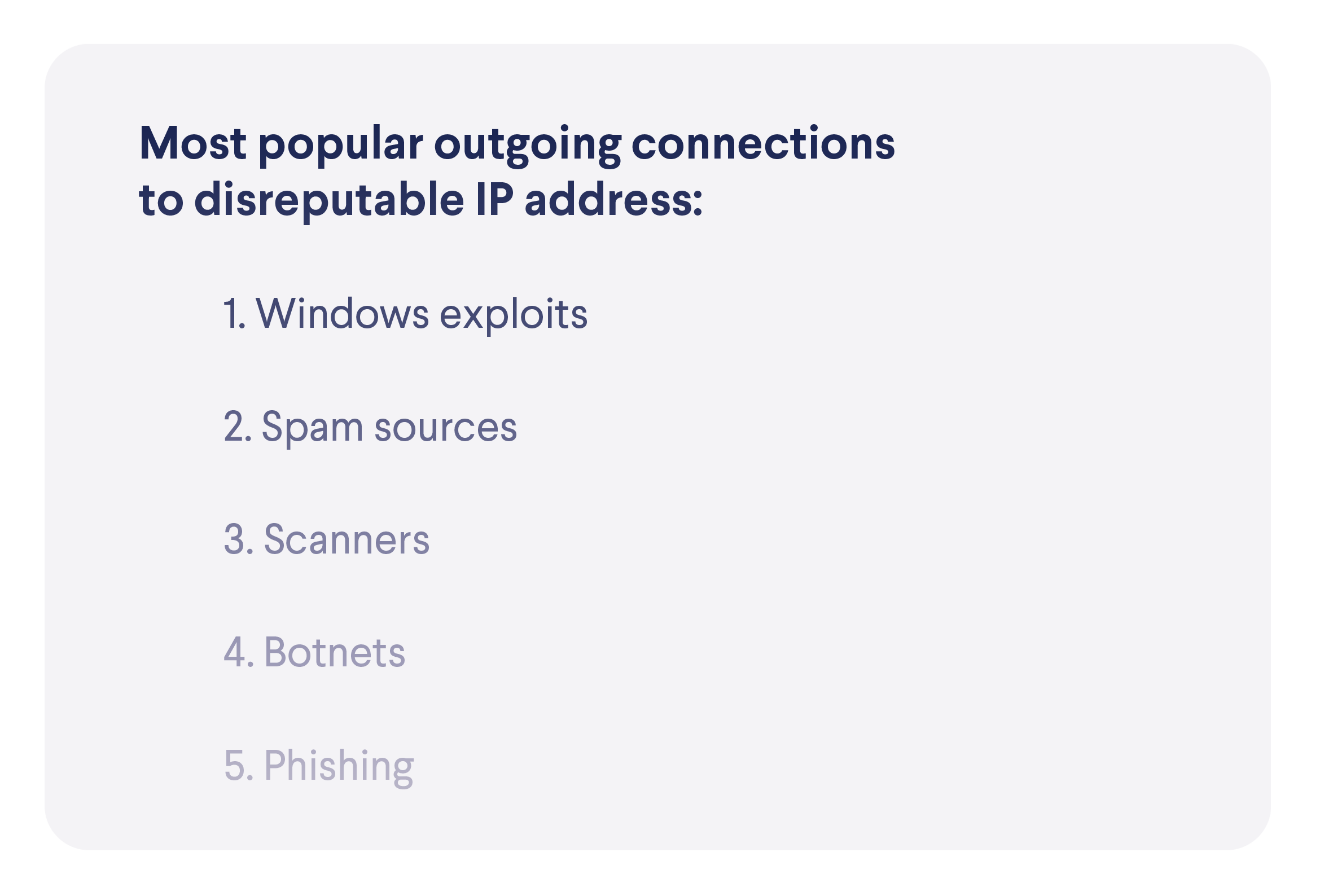
The Most Popular Exploits
Devices Under the Most Threat
We’ve gathered extensive data about which devices are most often targeted from known disreputable IP addresses (some might call these blacklisted IP addresses). Not surprisingly, NAS storage devices, which hold the most valuable data on the network (including backups), are targeted frequently. Almost a quarter of all attempts to connect to these devices from suspicious IP addresses target NAS devices, while the devices themselves make up a very small part of the overall connected device landscape. 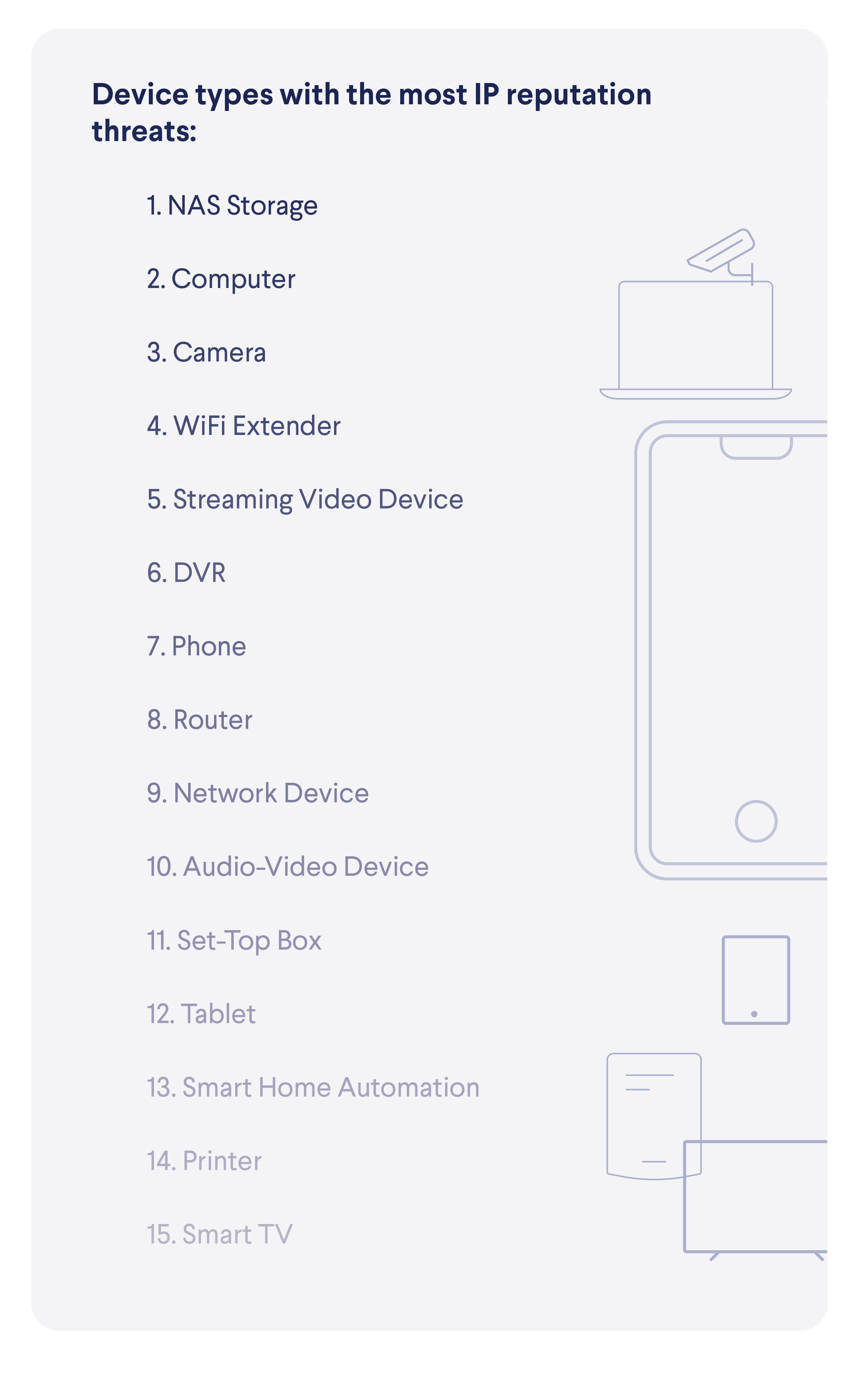 While malicious connections are often directed through proxies to mask their true origins, our data shows that there are several countries from (or through) which most of these connections are attempted. Note that our device base is a bit skewed towards North America, therefore it might not be surprising to see a larger presence of the US as the origin of the connections.
While malicious connections are often directed through proxies to mask their true origins, our data shows that there are several countries from (or through) which most of these connections are attempted. Note that our device base is a bit skewed towards North America, therefore it might not be surprising to see a larger presence of the US as the origin of the connections.  We have also gathered a bit of data about the attacking IP addresses. Here is a top 10 list of the most active ones.
We have also gathered a bit of data about the attacking IP addresses. Here is a top 10 list of the most active ones. 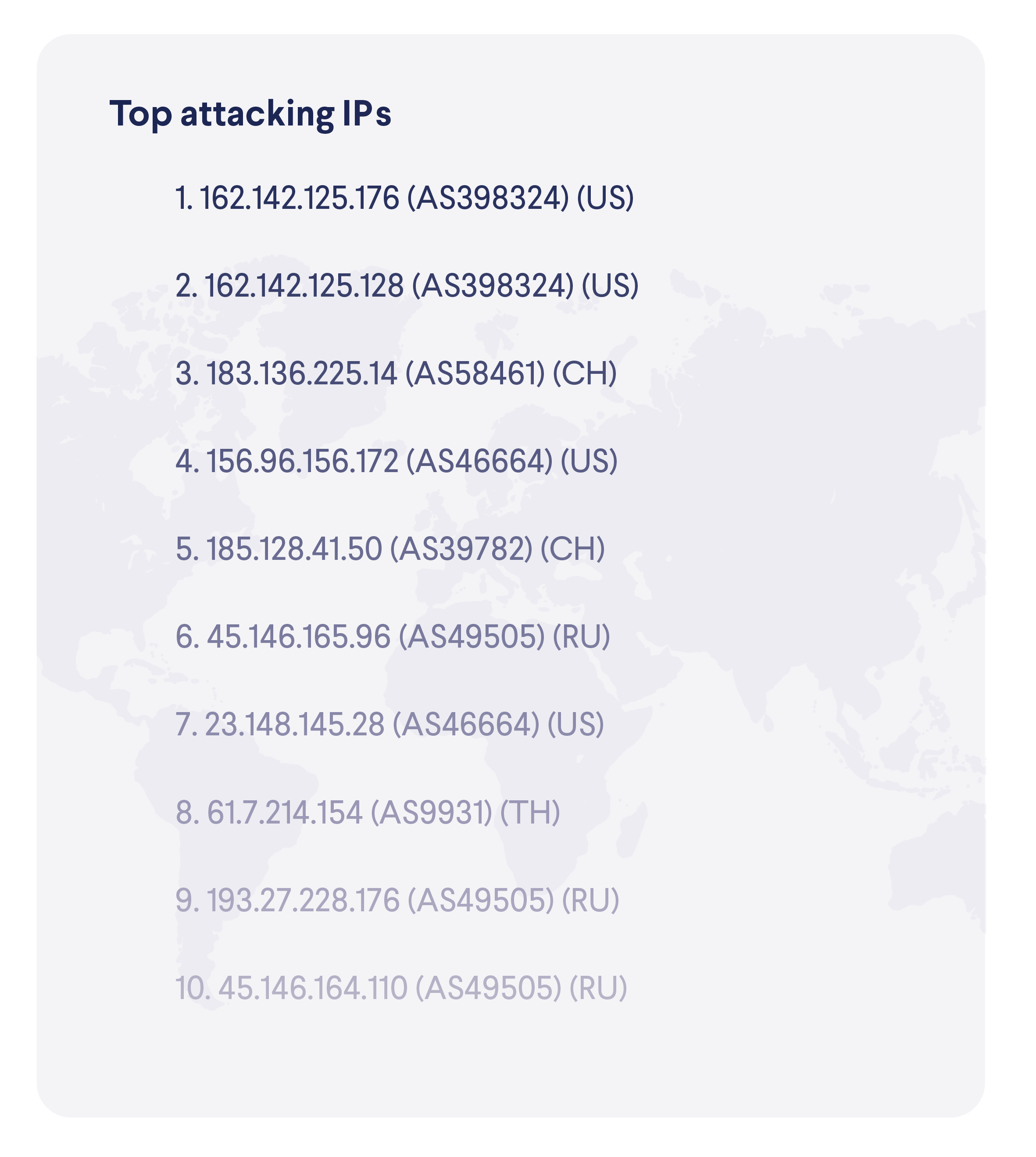 In terms of devices targeted, here are the most active attacker IP addresses.
In terms of devices targeted, here are the most active attacker IP addresses. 
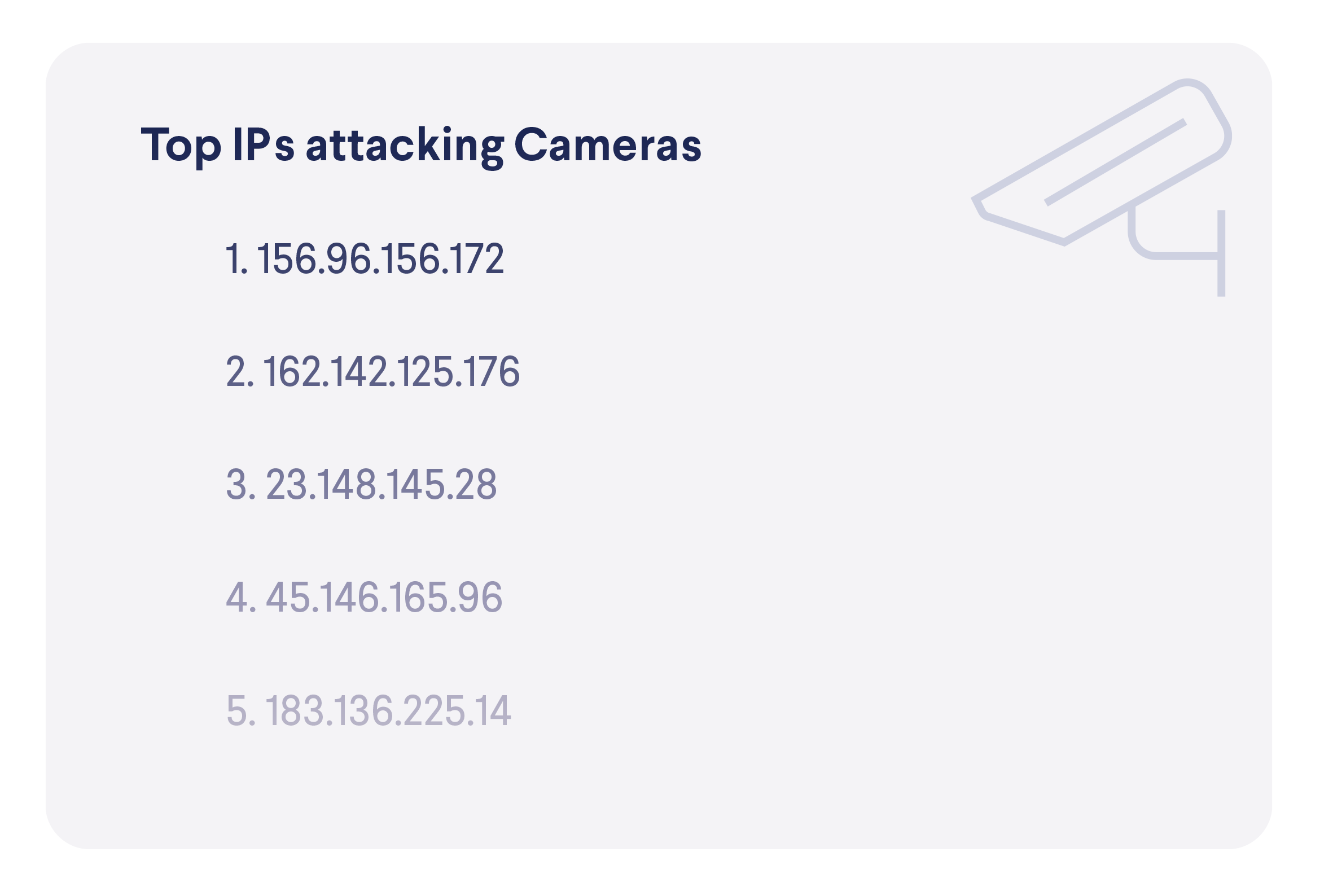
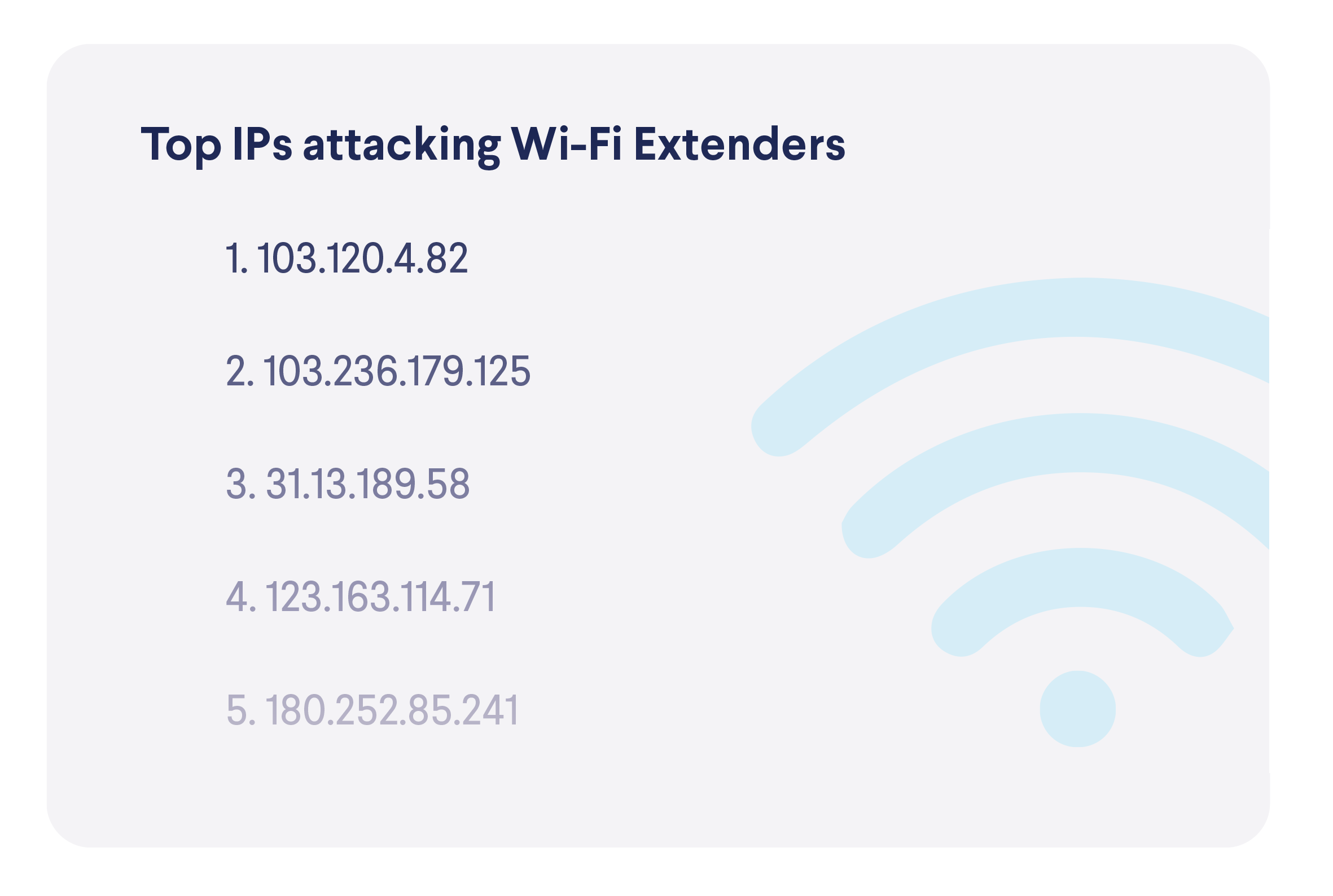
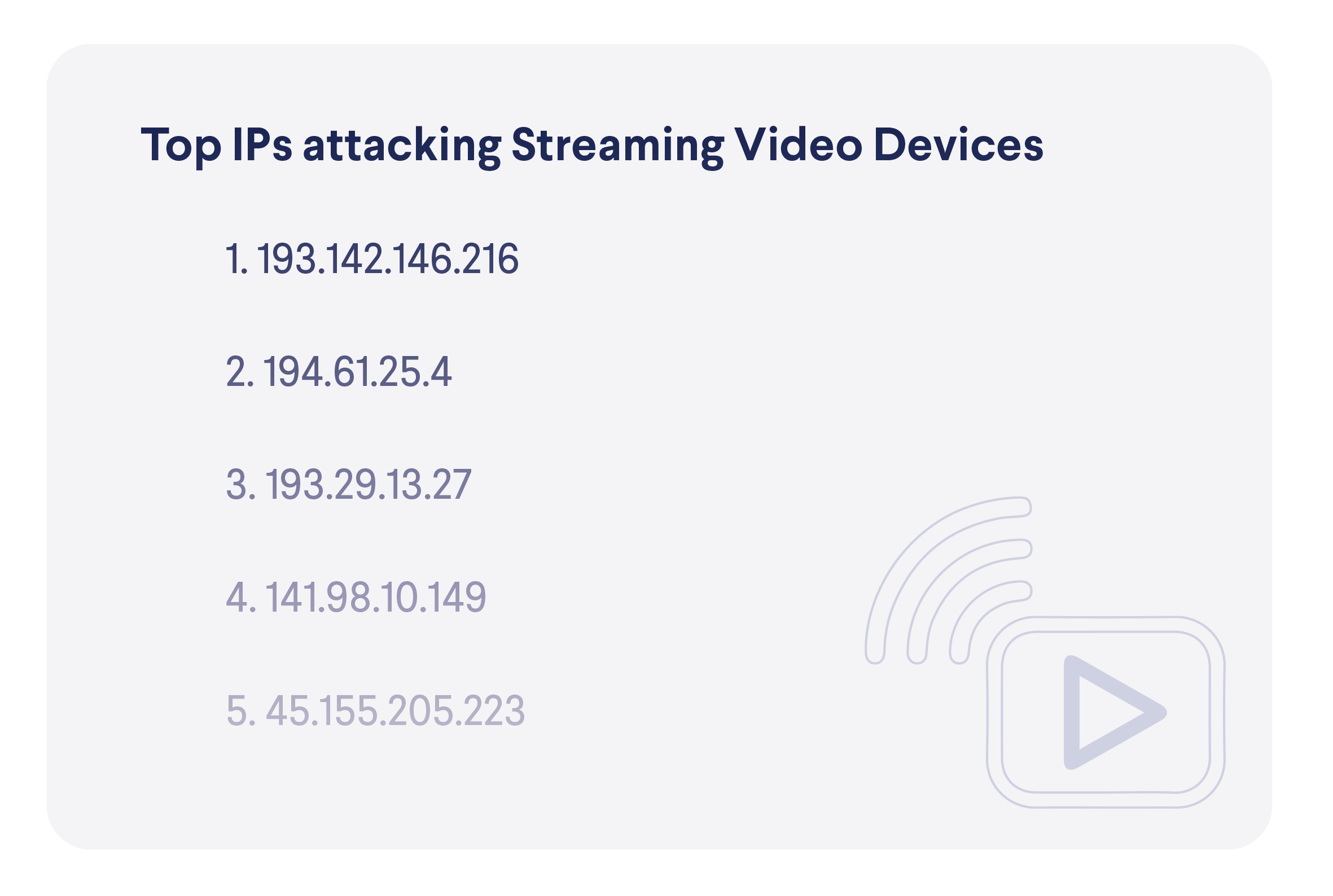
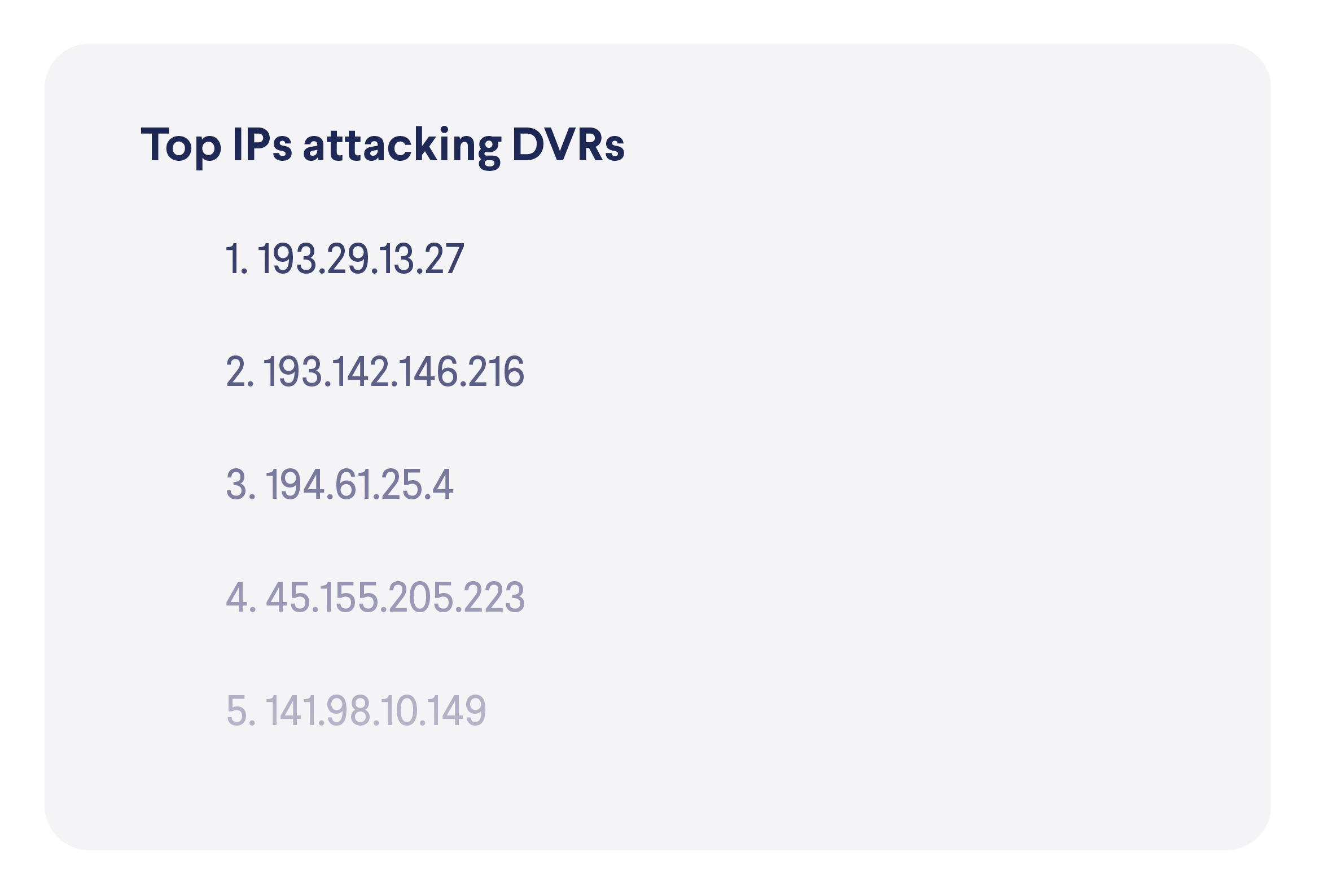 On the other side, there are devices that attempt to connect to blocked IP addresses, which indicates that they might be compromised, infected or that their users were tricked into risky behavior. The top two places in this list should not surprise anyone, as computers and phones are the two most popular device categories, while the high spot of NAS storage devices, again, shows how they are targeted by malicious actors.
On the other side, there are devices that attempt to connect to blocked IP addresses, which indicates that they might be compromised, infected or that their users were tricked into risky behavior. The top two places in this list should not surprise anyone, as computers and phones are the two most popular device categories, while the high spot of NAS storage devices, again, shows how they are targeted by malicious actors. 
IoT Botnets
Our threat research team is actively monitoring various IoT botnet attacks to discover and analyze new botnet families and be prepared against new types of attack techniques. 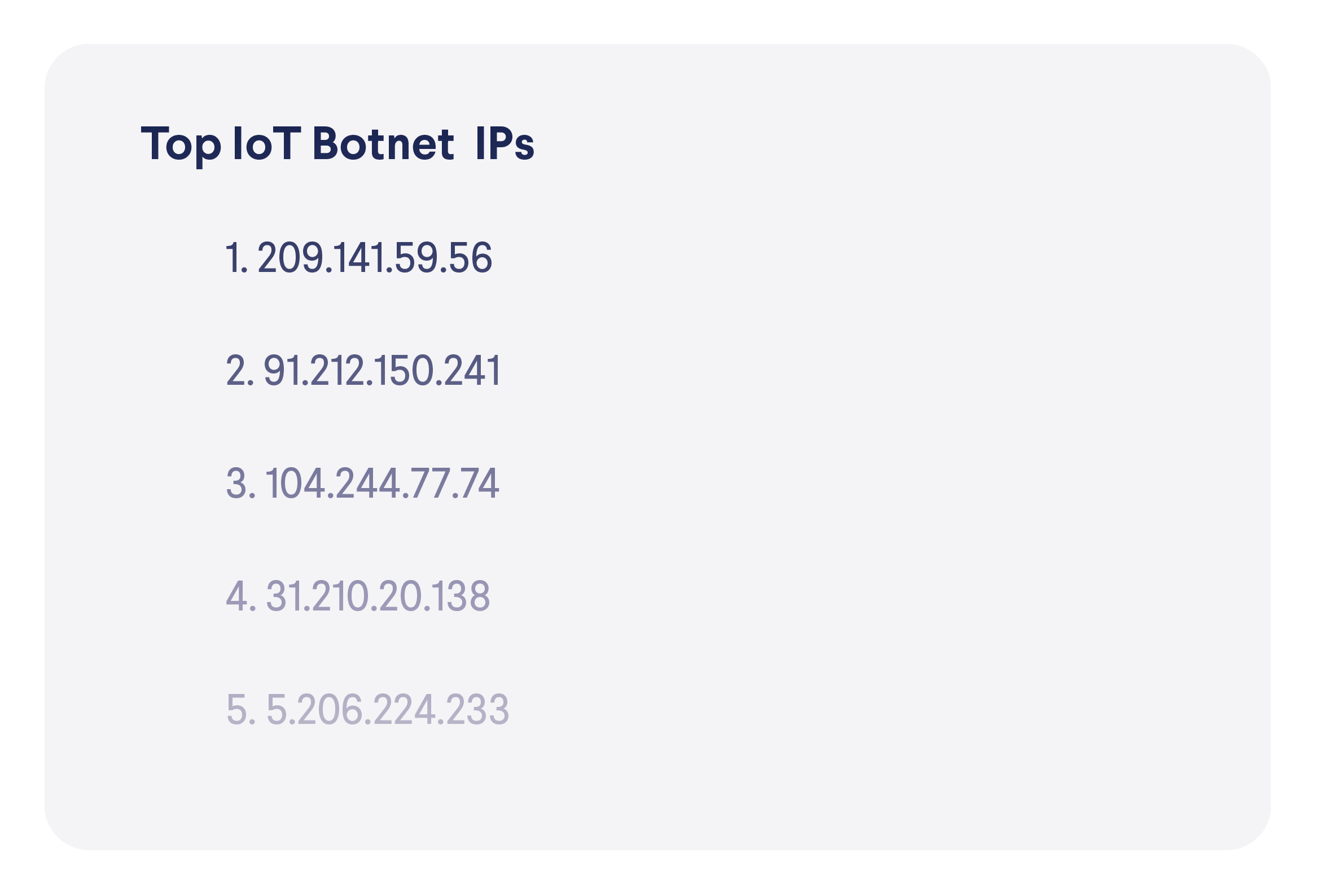 A typical attack follows the same pattern, as we described in our blog post about the genetics of an IoT attack. In most cases, a distribution server is set up and stores a downloader script and the malicious binaries that will be downloaded by the script at a later stage. Usually, there is a set of binaries prepared for various architectures before the attack. The malicious script downloads them one by one and tries to execute them in the hope that the one with the matching architecture will execute properly on the attacked device.
A typical attack follows the same pattern, as we described in our blog post about the genetics of an IoT attack. In most cases, a distribution server is set up and stores a downloader script and the malicious binaries that will be downloaded by the script at a later stage. Usually, there is a set of binaries prepared for various architectures before the attack. The malicious script downloads them one by one and tries to execute them in the hope that the one with the matching architecture will execute properly on the attacked device.
![Downloader script and malicious binaries stored on 91[.]212.150.241](https://cujo.com/wp-content/uploads/2023/08/table-description-automatically-generated.png)
![Figure 2 - Downloader script at 91[.]212.150.241/go.sh](https://cujo.com/wp-content/uploads/2023/08/graphical-user-interface-description-automaticall-4.png)
Malicious binaries of different campaigns are either stored on different IPs or the same IP, but in a different folder or with the filenames changed.
![Malicious files on 209[.]141.59.56](https://cujo.com/wp-content/uploads/2023/08/a-black-and-white-document-description-automatica-1.png)
![Figure 3 - Malicious files on 209[.]141.59.56](https://cujo.com/wp-content/uploads/2023/08/a-black-and-white-document-description-automatica.png)
![Malicious files on 5[.]206.224.233](https://cujo.com/wp-content/uploads/2023/08/table-description-automatically-generated-2.png)
![Malicious files on 5[.]206.224.233](https://cujo.com/wp-content/uploads/2023/08/table-description-automatically-generated-1.png)
The IoT botnet landscape is still dominated by Mirai and Gafgyt variants. In most of the botnet attacks the malicious binaries are based on the leaked code of these families, as in the case of our recent discovery.
Crypto miners attacking Linux machines and IoT devices are popular as well. Over the summer we have seen several H2miner and Dota malware campaigns. Another crypto mining botnet family, Sysrv, was discovered last December and is still active today. It is not only attacking Linux systems, but Windows devices as well. We closely monitored its continuous development over the last few months, and recently released a blog post detailing our findings. Besides typical DDoS and crypto mining botnets, we have also observed ransomware attacks against NAS devices. The most popular family was the eCh0raix ransomware.
Prevalent exploits
Researchers found a new Mirai variant called the Dark IoT botnet, which exploits a recently disclosed vulnerability, impacting Realtek chipset-fitted devices and vendors who use the Realtek SDK. This new vulnerability was revealed by IoT Inspector and was assigned the CVE number of CVE-2021-35395. In a developing trend, the Dark IoT botnet has added the following new exploits to its arsenal:
- Seagate BlackArmor NAS RCE – Undisclosed CVE number
- UDP Geutebruck – CVE-2021-33544
- Azure OMIGOD – CVE-2021-38647
This just goes to show how easy it has become to use the Mirai and Gafgyt skeleton-code with newly created exploits that follow the latest trends and are shared between botnet developers and operators. For more, follow CUJO AI Labs on Twitter.



