Android Set-top Box Lies about Its OS Version, Comes Pre-infected with Malware
Cheap Android set-top boxes are being sold by criminals, which either pre-infect devices with malware or have malicious code delivered via an update. Set-top boxes are quite popular: our device intelligence data shows that they made up over 2.4% of all new connected devices on home networks in 2023-2024.
Recently, a report on Doctor Web focused on the Android.Vo1d malware, which has infected at least 1.3 million devices, while Alex Turing (QI-ANXIN) exposed a set-top box botnet in operation since 2018 on Virus Bulletin. Last year, Linus Tech Tips even published an entire video discouraging consumers from buying these devices.
From the criminal’s point of view, targeting these devices makes sense. A typical set-top box is always connected to a power source and the Internet. Thus, running malware on it has benefits: the code doesn’t need to be optimized, as power use will not alert the owner, while the device can be used as a residential proxy, a bot in a distributed denial of service (DDoS) attack, or allow criminals to hack other devices on your home network, as well as steal passwords or other sensitive information.
Vo1d Disclosure Raises Suspicions
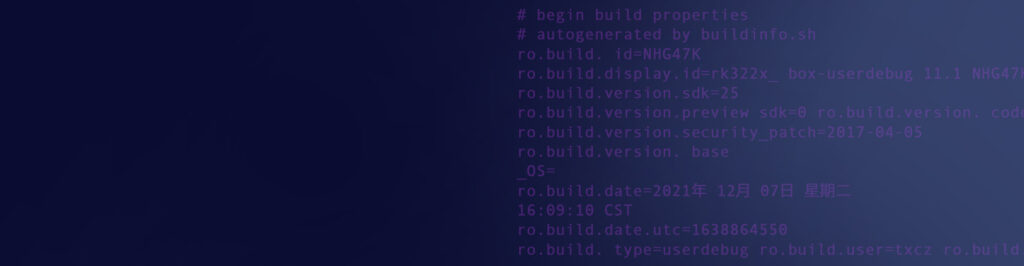
What caught our attention was this table from Doctor Web together with the following sentence:
“For example, the users who contacted us have models that are based on Android 7.1, despite the fact that for some of them the configuration indicates much newer versions, such as Android 10 and Android 12. Unfortunately, it is not uncommon for budget device manufacturers to utilize older OS versions and pass them off as more up-to-date ones to make them more attractive.”
Why is this interesting? First, Build/NHG47K means it is running Android 7.1.2. This suggests someone changed the Android version information in the Android config files but did not even bother to change the build code. What makes things even more interesting is that there is no official Android 10.1 version.
Looking at Android Firmware Dumps
To find out more, I looked for a similar device to purchase.
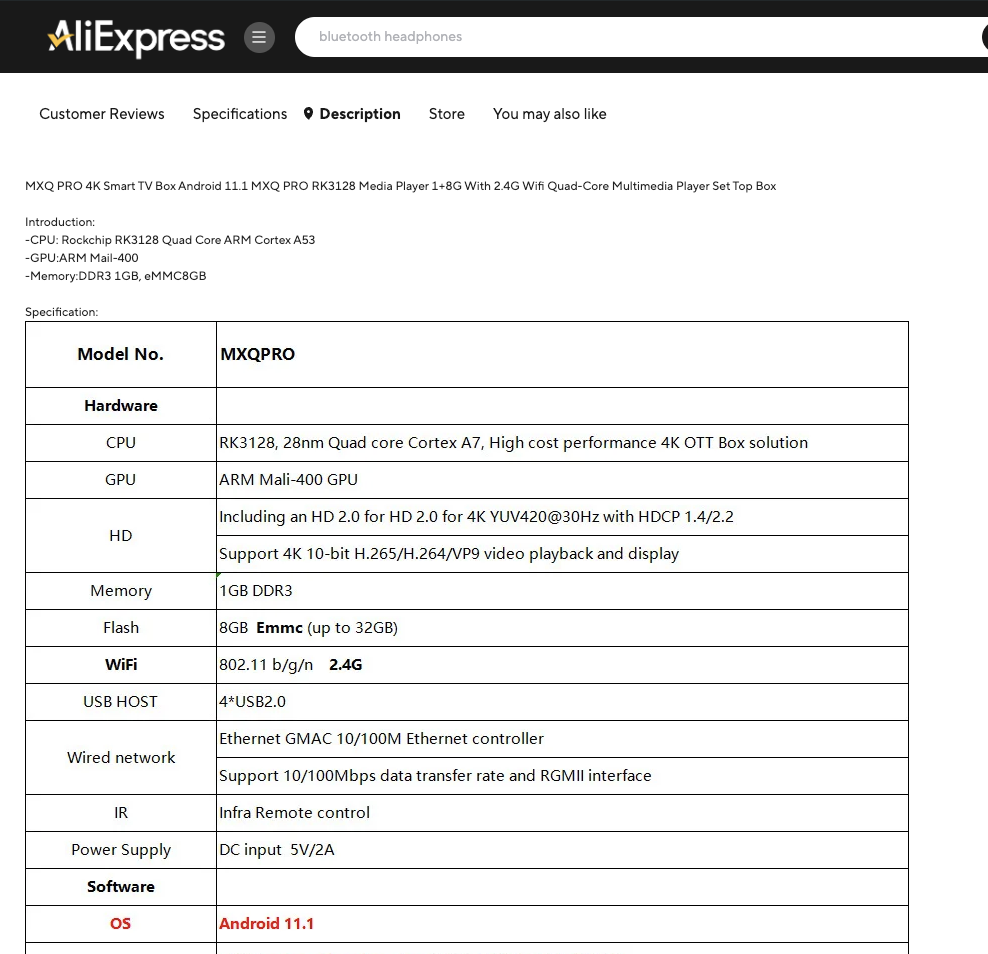
While waiting for the set-top box to arrive, I found dumps of similar firmware online when searching for strings RK3328-BOX_7.1.2 and RK3229_MXQ_5G.
I used unblob to extract the images and look at the build.prop file. This is where I found something sketchy.
Here is a legit build.prop file from an Android 7.1.2 set-top box. The information here is consistent.
# begin build properties
# autogenerated by buildinfo.sh
ro.build.id=NHG47K
ro.build.display.id=rk3328_box-userdebug 7.1.2 NHG47K eng.user.20180319.225151 test-keys
ro.build.version.incremental=eng.user.20180319.225151
ro.build.version.sdk=25
ro.build.version.preview_sdk=0
ro.build.version.codename=REL
ro.build.version.all_codenames=REL
ro.build.version.release=7.1.2
ro.build.version.security_patch=2017-04-05
ro.build.version.base_os=
ro.build.date=2018年 03月 19日 星期一 22:51:51 CST
ro.build.date.utc=1521471111
ro.build.type=userdebug
ro.build.user=user
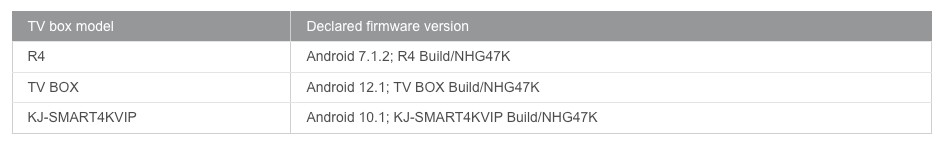
ro.build.host=ubuntuAnd here’s how a different set-top box firmware image looks like.
# begin build properties
# autogenerated by buildinfo.sh
ro.build.id=NHG47K
ro.build.display.id=rk322x_box-userdebug 11.1 NHG47K
ro.build.version.incremental=eng.txcz.20211207.160910
ro.build.version.sdk=25
ro.build.version.preview_sdk=0
ro.build.version.codename=REL
ro.build.version.all_codenames=REL
ro.build.version.release=11.1
ro.build.version.security_patch=2017-04-05
ro.build.version.base_os=
ro.build.date=2021年 12月 07日 星期二 16:09:10 CST
ro.build.date.utc=1638864550
ro.build.type=userdebug
ro.build.user=txcz
ro.build.host=txcz-host2The Android version information is allegedly different (11.1), but the security patch date is the same one from 2017 ¯\_(ツ)_/¯ . As I’ve already mentioned, Android 11.1 was never released, but 11.0 was released in September 2020. By manually checking the files of this “newer” image, I was convinced that it was still running Android 7.1.2.
But let’s not draw conclusions from firmware images downloaded off random Internet websites.
Getting Hands-on with an Android Set-top Box

I believe the following photo is enough to confirm my suspicions.
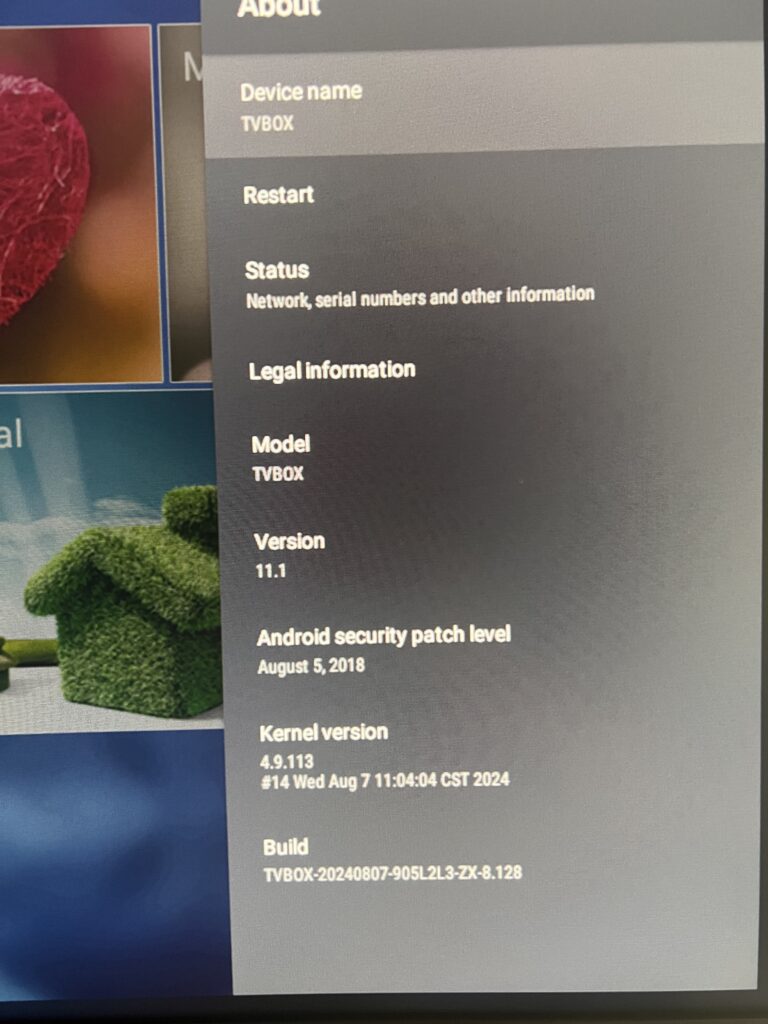
So, I just connected a device with a non-existent Android version (11.1) and six years old security patches. But hey, at least it has a recent build date – I was not expecting that.
Getting Root Access
The next step was to root the device, which was easy – as it was already rooted.
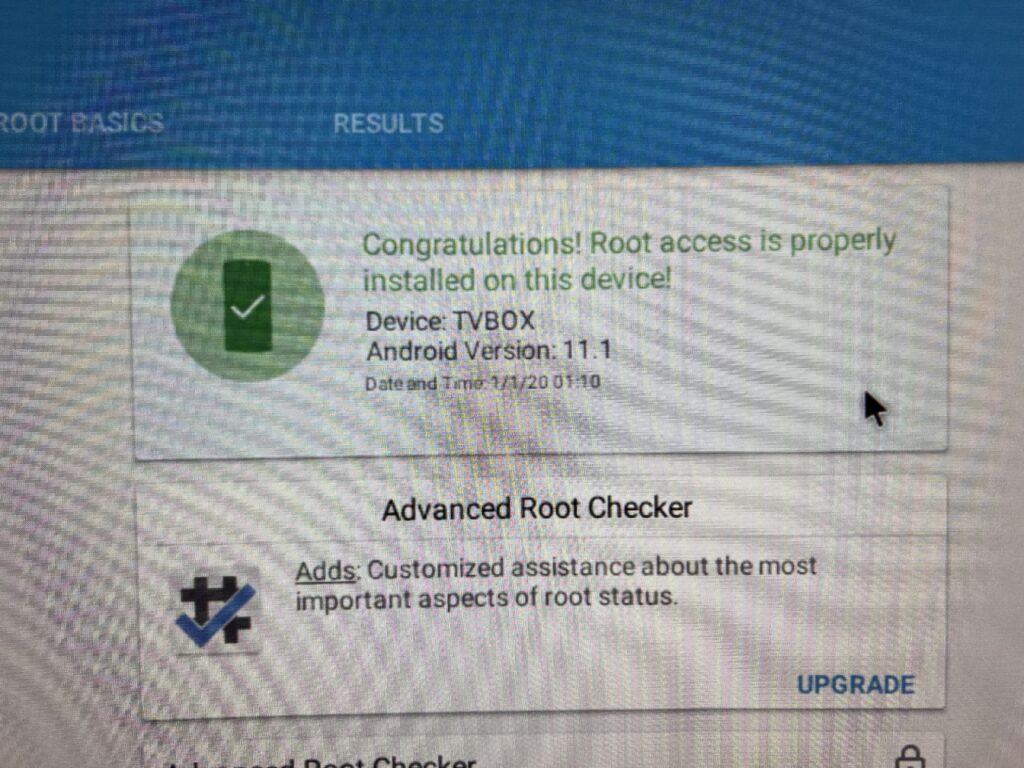
Warning: Rooting an Android device turns off certain security features. Thus, malware has a better chance of taking over the system or accessing confidential information.
My next step was to get a root shell.
Accidentally Bricking the Device
Unfortunately, I did not enable ADB before I installed an app, and the device is now stuck in boot, with the boot to recovery button not working. Perhaps the criminals realized it was bad for business to allow people to install their own firmware on the device.
This is as good a time as any to remember the No 1 rule of hardware hacking – always order three devices, not just one.
Malicious Activity Infrastructure Seems Segregated, Location-based
Threat actors appear to be segregating their set-top box infrastructure by market. For the one highlighted by Doctor Web, our telemetry shows that Western markets are barely affected, with their focus primarily on Asia.
In the case of Bigpanzi, their activity seems concentrated in Brazil. Additionally, there have been reports of malicious actors targeting Western markets by using access to pirated content as the main lure. There are subtle indicators that it could be the same threat actor, or at least some parts of the code are being reused, suggesting a coordinated effort.
![A chart that shows data from August to October 2024 with connections to malicious domains: meiboot[.]com, bitemores[.]com, catmore88[.]com, catmos99[.]com, 6f33933ce4a5c9e1b32fea736a61351a[.]com
The latter domain is the only one active until mid-September, where other domains spike in activity.](https://cujo.com/wp-content/uploads/2024/10/newplot-1.png)
Conclusion
Product descriptions of cheap, no-name devices might lie about their Android version. I was able to order a new device which had 6 year old security patches – and vulnerabilities. What’s even worse, these devices might come pre-infected with malware.
If you are not comfortable with letting a stranger in a black hoodie sit in your living room and use your Wi-Fi, maybe, just maybe, you should not be comfortable with using these devices.

Appendix – Set-top Box PCB Layout


