Phishing for Votes in the Upcoming US Election

Foreign interference and disinformation have gotten a lot of attention in US media before the 2024 presidential election. CUJO AI Labs decided to look into the suspicious (phishing) websites that were:
- Active in August and September of this year.
- Related to the US presidential election, candidates, and funding.
Just as we had previously done with several other major events.
Finding Suspicious Websites Targeting the 2024 Election
We used Safe Browsing threat data from CUJO AI Sentry, which protects tens of millions of home networks and stops over 8,000 cybersecurity threats every minute, on average.
Sentry’s Safe Browsing protection engine combines internal and external threat intelligence feeds with our machine learning algorithms to stop consumers from accessing suspicious websites on protected networks. Our real-world deployments across over 56 million home networks help us identify short-lived phishing sites faster, as well as continuously train and improve Sentry.
For this short report, we analyzed suspicious websites detected between the 28th of August and the 28th of September, when the US presidential election campaigns were in full swing. To narrow our focus on the potentially most damaging malicious activities, we filtered our sample for websites that included a financial incentive, e.g., urged visitors to donate to a campaign.
Analyzing Malicious Election Sites
The sample we analyzed had over 30,000, or around 1,000 daily, attempts to visit suspicious election-related sites. Our analysis surfaced a narrow set of suspicious websites. This is expected, as election funding (and fraud) campaigns are primarily conducted through direct calls and SMS messages.

Dangers of fraud associated with elections were also noted when a legitimate get-out-the-vote campaign was recently called out for employing phishing tactics.
We reviewed a set of malicious sites that were detected by CUJO AI Sentry and found that most were not being flagged by anti-malware vendors. At most, we found 5 security vendors flagging a site, almost a month after it had been detected by Sentry. In most cases, sites were flagged by just 1-2 cybersecurity vendors, if at all. This shows that few visitors to these sites were stopped outside of networks protected by CUJO AI.
In most cases, sites were flagged by just 1-2 cybersecurity vendors, if at all. This shows that few visitors to these sites were stopped outside of networks protected by CUJO AI.
Location
The fact that we are talking about the US election did not stop visitors from Europe from attempting to visit the most popular of the sites in the sample. However, attempts to access these sites from Europe were miniscule (fewer than 1%), when compared to US numbers.
Phishing campaigns are often localized, as they target local services, e.g., banking sites. But in today’s global world, there’s really no geographic containment, as expats and tourists in other countries may also fall victim to a fraudulent website. This is why having deployments across North America and Europe allows CUJO AI Sentry to rapidly detect suspicious websites and stop access to them across the entire user base, improving the security for everyone.
Having deployments across North America and Europe allows CUJO AI Sentry to rapidly detect suspicious websites and stop access to them across the entire user base, improving the security for everyone.
Other Findings
Due to the high variance of our sample, we do not want to draw definitive conclusive insights about which candidate’s voters were targeted more often or any prevailing trends or campaigns. This is why the examples we expose here should not be taken as all-encompassing, rather than anecdotal.
Overall, 40% of the sites in our sample were automatically categorized as phishing sites. 79% of all the websites were categorized as malware, with some overlap with the phishing set.
We detected some traffic to payment-related (checkout) pages on some of the sites. Thankfully, end-users did not attempt to visit these sites repeatedly. Of the more interesting finds, we found one candidate’s NFT project being used as a scam target.
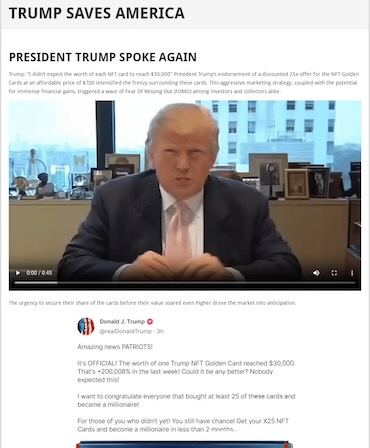
A handful of sites also had no clear connection to the election or politics at all. At least one instance was hosting pornographic content during our analysis. It might be a spam tactic, where spammers automatically register domains that include popular keywords. On the other hand, the phishing campaigns might already be over and gone from the web. This, again, highlights the need for real-time browsing threat detection.
Since our algorithms also analyze websites to detect instances of cloning, we sometimes come across edge cases. In this instance, we detected a possible staging website for a state’s election website. While this is a false positive, as the site is unlikely to be a clone for phishing, we would recommend not having staging websites publicly available.
Conclusions
Due to how US elections are funded, phishing attempts might slip under the radar of both cybersecurity vendors and end-users, as noted by other cybersecurity researchers, and as we’ve experienced over the years: some legitimate funding organizations use spam and phishing tactics that are sometimes very hard to distinguish.

Third party anti-malware vendors provided limited security against the sample of suspicious sites related to the upcoming US election that we analyzed. However, it should be noted that scams are also very actively conducted through social media networks, SMS messages, and other direct means.
CUJO AI Labs continue to monitor threat data and improve Sentry, as well as other Digital Life Protection solutions offered by our company. To find more of our reports, visit the Resources page and our blog.
