Persistent Phishing Campaign Uses Surveymonkey and Cloudflare, Bypasses Gmail’s Spam Filter

I don’t know what I did in the past, but boy do attackers love to send me phishing messages.
This time, the story started with the following emails:
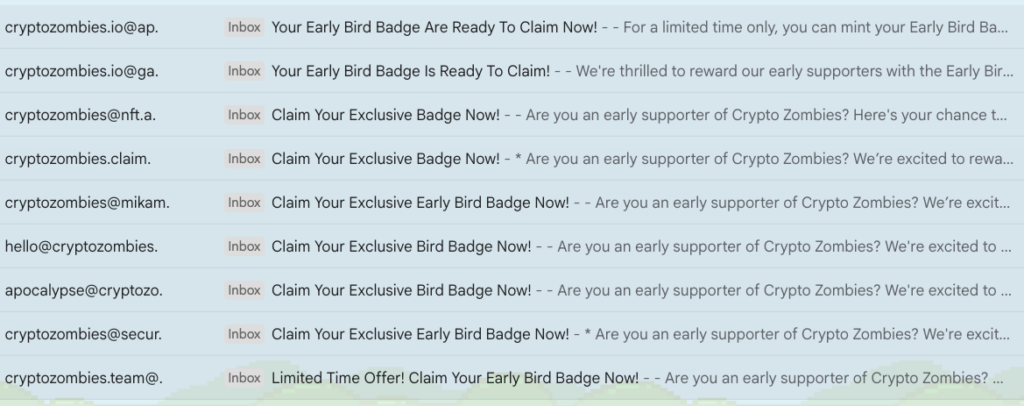
The emails share the same theme and message, and were all sent via research.net, which is part of the Surveymonkey service. This approach to making phishing attacks look more legitimate is not new, and has seen more public exposure recently, where attackers impersonated support personnel and used Google Forms or Apple support registrations during scam calls to send notifications from the legitimate source to their victims.
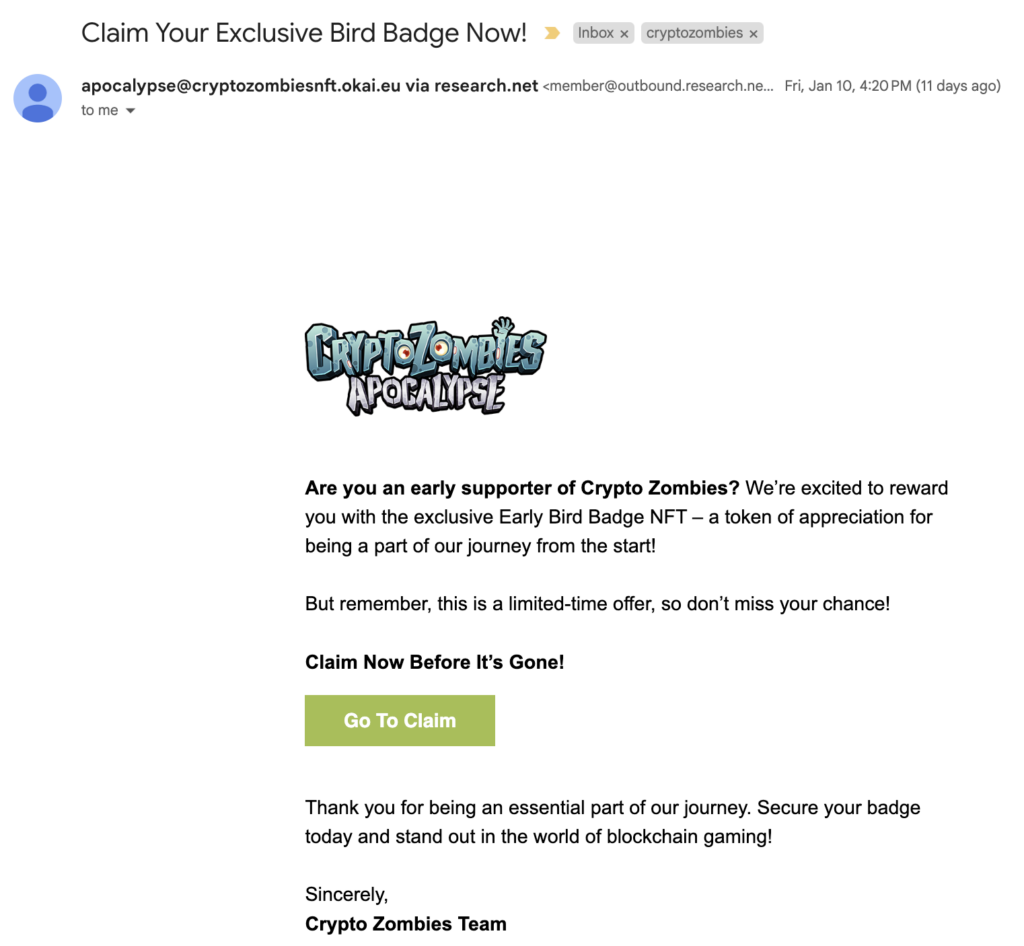
What makes this spam/phishing campaign interesting is that I, indeed, am an early “supporter” of Crypto Zombies. Crypto Zombies is an educational website where anyone can learn Solidity-based smart-contract development. I tried it in 2018 but did not use it since. I can only speculate how the attackers got this information.
The most probable explanation is that the contact list for the Crypto Zombies newsletter (delivered by loomx.io) had been leaked and landed in the hands of some scammers. The scam follows the regular NFT scam scenario. The victim visits the website and “claims the free NFT”, but instead of receiving new NFTs, the webpage tries to convince the user to transfer their NFTs to the scammer.


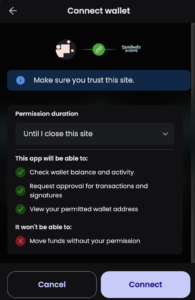
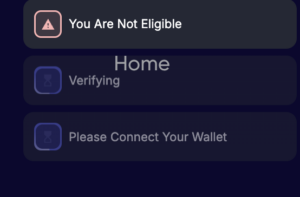
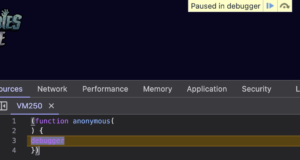
As often happens with these sites, it had some basic anti-debug features. The screenshot below shows what happens as soon as you open the developer console. The JavaScript code is also obfuscated.
But why is this phishing campaign interesting? Isn’t this the regular boilerplate NFT scam? Two aspects of this attack made it interesting to me. First, it bypassed the Gmail spam filter. This is because they use hacked Surveymonkey accounts to send out their scam emails.
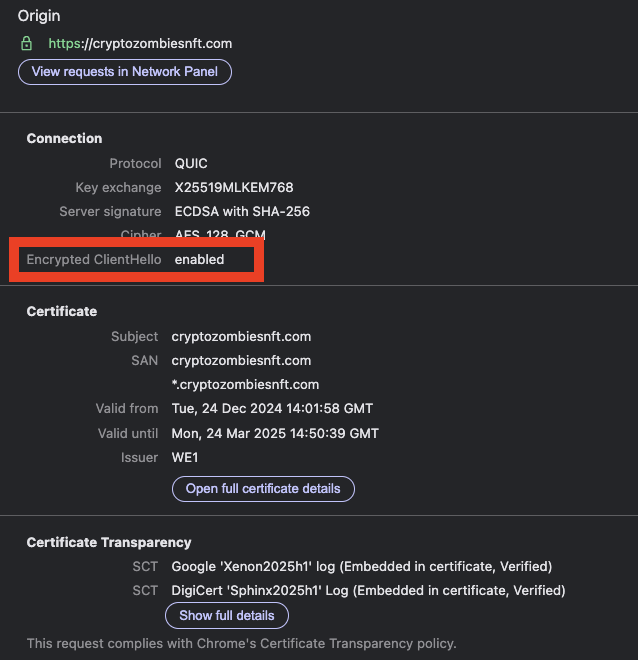
The second interesting part is the use of Encrypted Client Hello. If you are not familiar with ECH, you can find more information here. The tl;dr is that network security solutions have a hard time monitoring and blocking connections when ECH is used. In previous TLS versions, the website domains were still visible in HTTPS traffic, which is no longer the case, thanks to ECH, because it encrypts the domain, making network-level traffic inspection… challenging. This is good for privacy, bad for security.
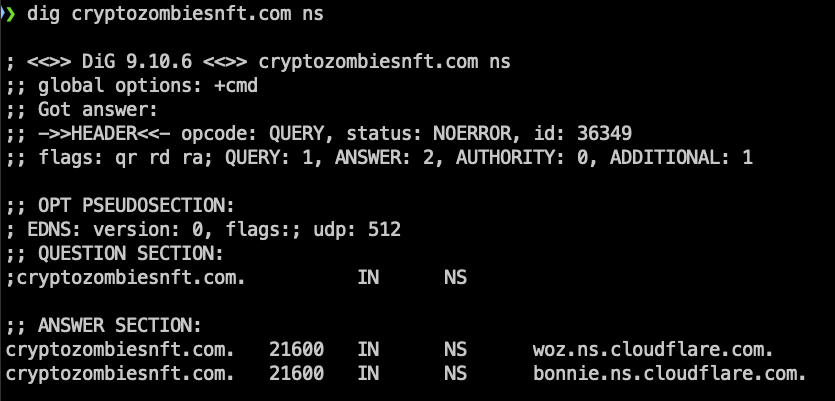
This scammer website was also using Cloudflare as its hosting provider, which is one of the biggest advocates for ECH. From the Cloudflare documentation: “ECH is enabled by default on Free zones. Other plans can turn it on or off”.
Even though NFT scams mostly target people at home rather than people working behind enterprise security hardware like Secure Web Gateways and Nextgen Firewalls, we believe malicious actors are using ECH to evade detection.
It is also likely that this instance is just a lucky coincidence for the attackers – they might not even know that they have ECH on their website. In any case, Cloudflare provides their site with some free protection.
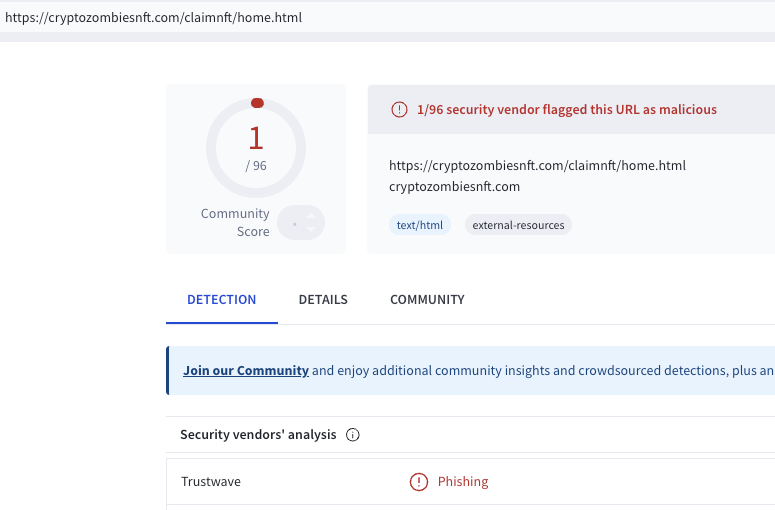
Lastly, I checked the URL reputation. Seems like security vendors have to up their game.
PS: Turns out there was indeed a real “free NFT for Crypto Zombies” campaign, but on a different, legit URL 🙂
PS2: While reading through the whole article, you were probably wondering, is it the year 2022 or what? Are NFTs still a thing? Actually, yes. Even though the market and the average NFT price are nowhere near as high as they were years ago, one ugly monkey NFT image, like the Bored Ape Yacht Club, still goes for 38K USD. And that is worth stealing.