FIRST SecLounge CTF 2020 – RE and Misc Challenges

FIRST CTF 2020 included a reversing track that consisted of 6+1 questions related to the field of reverse engineering.
Break the Snake
A small Python BreakMe – enjoy! Break it and retrieve the hidden flag inside.
The downloaded ZIP file contains multiple Python packages and a Mach-O 64-bit executable called pybreakme. The pybreakme binary was compiled using PyInstaller, which bundles a Python application and all its dependencies into a stand-alone executable, so no Python installation is needed in order to execute the program.
We used the pyi-archive_viewer tool of PyInstaller to inspect the content of the executable and extract the pybreakme.pyc file.
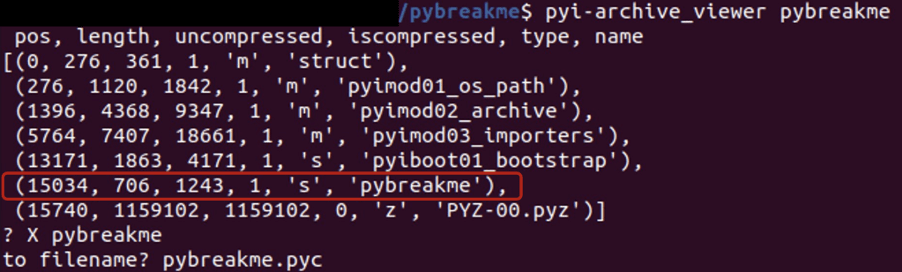
To decompile pybreakme.pyc we used the uncompyle6 tool. For the first try we got an error message: “ImportError: Unknown magic number 227 in pybreakme.pyc”.
In order to execute the tool properly, we need to fix the header of the file. The following bytes were added at the beginning of the file: x42x0dx0dx0ax00x00x00x00x00x00x00x00x00x00x00x00.
Now uncompyle6 could successfully decompile the Python code.
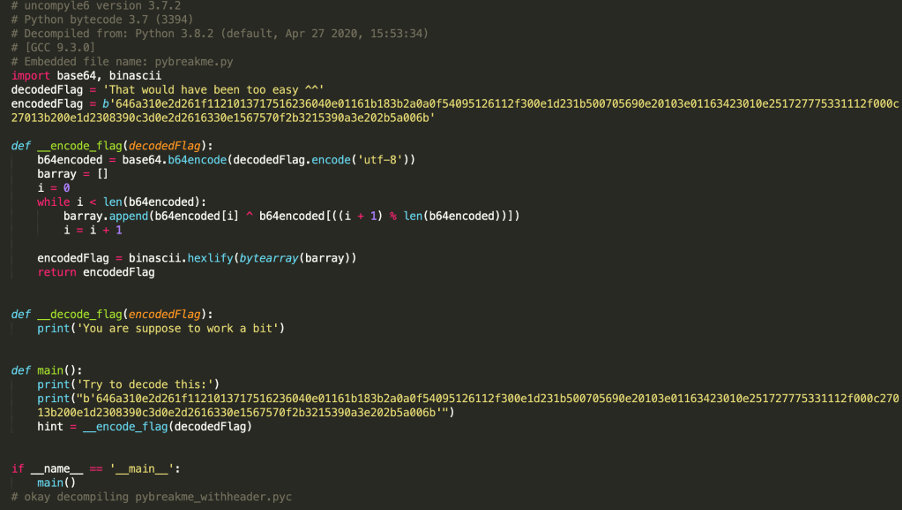
The only step left is to understand this simple Python code. To get the encoded flag the original flag was base64 encoded; then every character was XORed with the next one and the last character with the first.
To start the XOR decoding we guessed that the base64 string will end with “=” and then XORed every character with the next one from the end of the string. Finally, by simple base64 decoding we got the flag.
Flag: We’ll not risk another frontal assault. That rabbit’s dynamite.
My Secret – Part 1
What is the sha256 for the proper file?
The file is an ELF binary, where the bytes are in reverse order.
Use the following command to change the order:
< mysecret xxd –p –c1 | tac | xxd –p –r > mysecret.reverse
And calculate the hash:
sha256sum mysecret.reverse
Flag: 095bf40d794b0259556648e114366f46108ab32b324ac9d30399e8e270d47ef5
My Secret – Part 2
What is the flag in plain text?
This flag can be guessed by looking through the strings in the file or by reverse engineering the code (see next part).
Flag: I forgot my very old key
My Secret – Part 3
What is the encryption key?
The main function is very simple. It takes the plaintext flag and encrypts it with RC4.
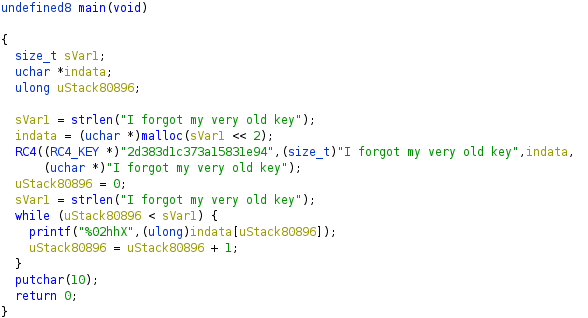
Flag: 2d383d1c373a15831e94
My Secret – Part 4
What is the algorithm used to encrypt?
See previous part.
Flag: RC4
My Secret – Part 5
How many possible keys did you find?
There are several 16-byte-long alphanumeric strings (possible keys) within the code. They can be counted by the memory addresses or using the following command:
strings mysecret.reverse | grep –w –E ‘[[:alnum:]]{20}’ | wc -l
Flag: 10107
Misc Challenge
We were given a simple .zip file for this challenge, but upon further investigation it turned out to be an encrypted archive. It is always a good idea to try a blank password or even the name “spourious” but neither of them opened the archive.
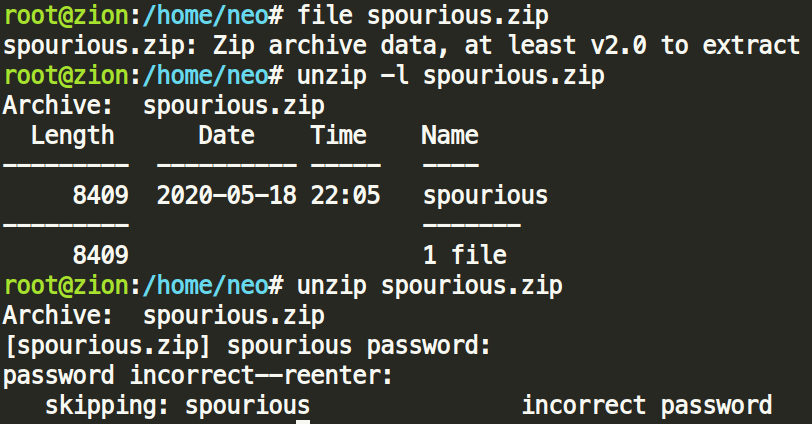
File spourious.zip
unzip –l spourious.zip
So, we decided to crack it using fcrackzip:
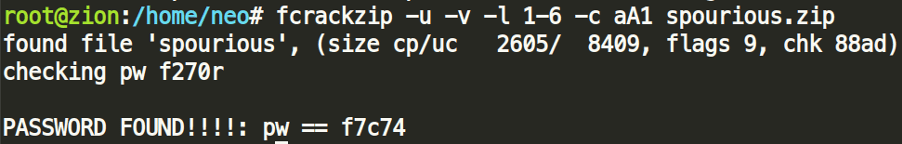
Fcrackzip –u –v –l 1-6 –c aA1 spourious.zip
-u – use unzip to avoid errors
-v – verbose
-l – character limit between 1 and 6
-c – lower, upper case and numbers too (aA1)
We can now unpack the archive. However, the file does not make sense at first. It looks like the magic headers have been manipulated, and it does look like an original ELF header. We might need to just fix the ELF header, so let’s try it:
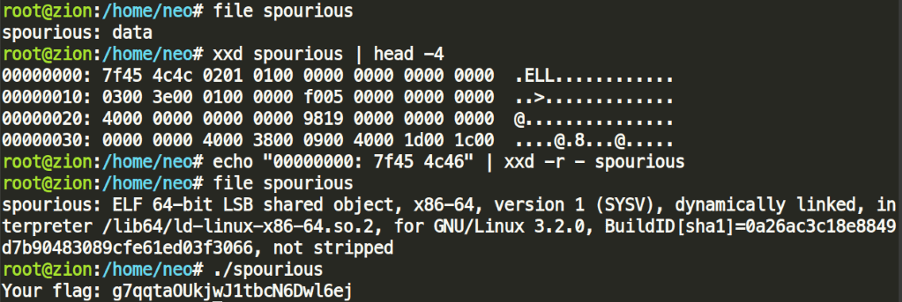
Xxd spourious | head –4
echo “00000000: 7f45 4c46” | xxd –r – spourious
file spourious
./spourious
Hint: Never run code from a CTF on a machine that has important information for you. Always use VMs and snapshots.
Solution: g7qqtaOUkjwJ1tbcN6Dwl6ej



