FIRST SecLounge CTF 2020 – Crypto Challenges

The FIRST CTF 2020 included a crypto track that consisted of 7 questions related to different cryptography challenges.
Decode This
WW91ciBmbGFnOiBjYjk0ZTQyMzQ4YjQ1NTBjOTdmMmVlMTY5N2M0ZjFmNQ==
Simple base64 encoding.
Flag: cb94e42348b4550c97f2ee1697c4f1f5
Decode This Other
<~<+ohc@UX=l@j#Z#ARloqDfQt/+C]&&@<-WFFDiaQAU&;>ASu!rA8,po+Cf>,ATJu+Ec5e;@3BH!ARlp*D]iP.D/FE5Bk(RnAKYE%@VKq)@<-W9@VK^gEd8d<@<>p#Dg#]4+E2@4AU%p1FD5W*+Cf>,D09`1@psInDf0V=E,ol=De!^%F!,R<@<<W9ATD?)A7]grB5V9k+EVNE@psCuGp%$CCj@-lDJ*d"F(c4@;]_#@:s-oBQ�#DCom?@:WeUCh4`2AU&;L+B3#mF(HJ(Df'?6DJ<ThFD5Z2+E2@>FDkZ-Ci^_9@<iu6DJXS@@V$Z@/RiF9+ELt'AKWC0DIal6Bln$&DBO%7@<<W#G&M)*+Ceu'FCAm$+@/pn8P(%7Df0Z;DepP+De*F#.4cTMDIal,@<iu9AT;j,Eb-A0Bl7K)@WH$gCNCV,F<G()Ecb`(DBNe)GM#;D'3P1FCfK9@;L!9+CT.u+DkP4+Du+>+DkP$DKK<$DBO.:Blmp-E+*6f/g+,,F`T)VDf0B:+EV:.+?;;%E,oZ1FCAWpAKX9;6V0il@q]:k@:OCjEcW@3Eb-@;F(&Zl+s:uG+E_a:[email protected],D/@<>p1+B3#c+D,FuB-:o0+>@54Ai;PXAR[MU2.SO"ARf=`1h&<t0JtRB2e4d%3+b$)AN)P[0Jt[G@[email protected];t!3AkD&@P/c1~>
This is ASCII85 encoded text. We can guess this by analyzing the frequency of the characters, looking at the distribution, etc.
The decoded text is:
The basic need for a binary-to-text encoding comes from a need to communicate arbitrary binary data over preexisting communications protocols that were designed to carry only English language human-readable text. Those communication protocols may only be 7-bit safe (and within that avoid certain ASCII control codes), and may require line breaks at certain maximum intervals, and may not maintain whitespace. Thus, only the 95 printable ASCII characters are “safe” to use to convey data. The flag is 0aaf66deb575d43ecfe4b5205157d538f54e77f0547a3b7e5125fea2a3995f0b.
Flag: 0aaf66deb575d43ecfe4b5205157d538f54e77f0547a3b7e5125fea2a3995f0b
Breaking the Code
Can you find the flag?
We found the secret text hidden in the HTML source line 1004:
segsa ptvey xmjve kerkt xqjtx gmvtt urksy bzuzo
And the following in the HTTP header: x-options: M3 – B – I,IV,V – J,T,V – 1,1,1
These are Enigma encryption settings:
- M3 – model3
- B – reflector type
- I,IV,V – rotor types and order
- J,T,V – rotors initial value
- 1,1,1 – rotors ring setting
We used CyberChef to decode the flag.
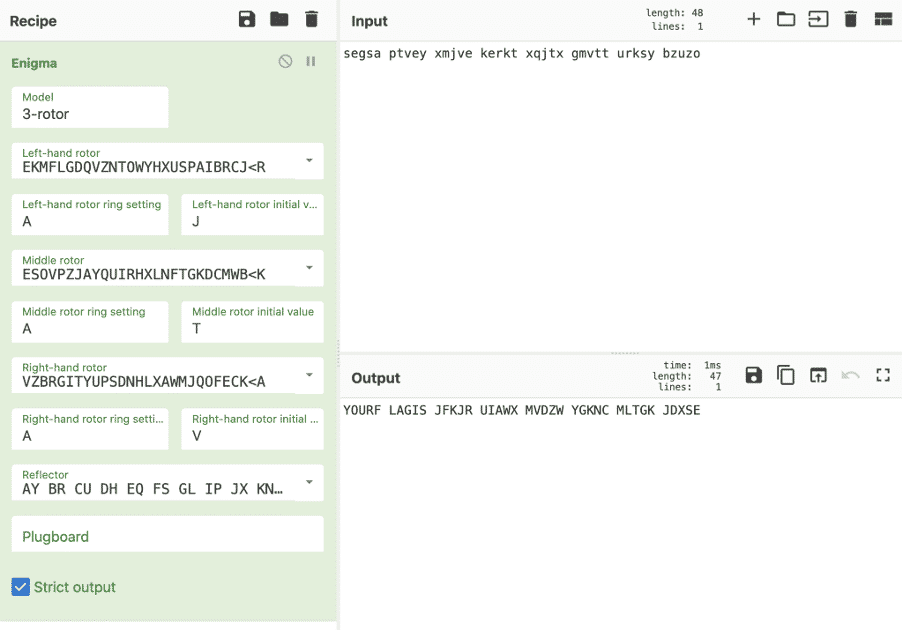
Flag: JFKJR UIAWX MVDZW YGKNC MLTGK JDXSE
Breaking the Code – Bonus
Can you find the flag?
Encrypted string: jjlpe oniqy lkwht griha bhesq zyiqz btikt idj
We found a base64 encoded image in the HTML source.
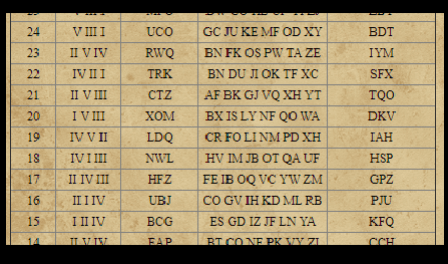
These are also Enigma settings. With a Google search we found the original image, which helped identify the columns.
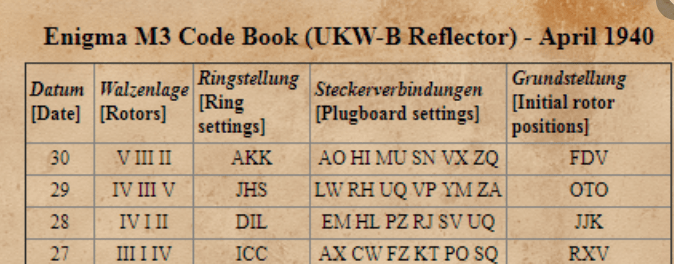
We tried all the variations, and the one for the day 18th day worked.
We used CyberChef to decode the flag.
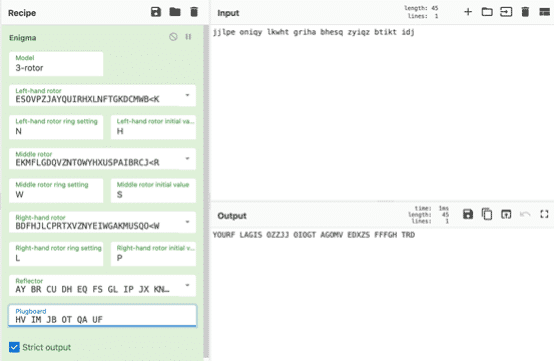
Flag: OZZJJ OIOGT AGOMV EDXZS FFFGH TRD
x/2 Salad
%96 p$rxx 4@56 567:?6D hc AC:?E23=6 492C24E6CD[ D@ 2 C@E2E:@? @7 92=7 Whc^a l cfX >2<6D :E A@DD:3=6 E@ @3E2:? 2 DJ>>6EC:42= 4:A96C[ D:>:=2C E@ #~%b W7@C E96 ae =6EE6CD @7 E96 2=A9236EX] %96 7=28 : D baf5decdg7eeg37fcbh243g_67c55c_cg6ea642ec53adb2haa66372f2b6`_3f
The text is encoded with ROT47. Either we guess it, or we try to break it as a substitution cipher, one by one.
Some of the most basic ciphers are substitution ciphers. If we look at the ciphertext and the spaces between the characters look natural, it is usually a good guess that this is a substitution cipher where space is not replaced.
Also, checking the index of coincidence of the text can help us to identify. (This is English text – https://en.wikipedia.org/wiki/Index_of_coincidence.) Unfortunately, it doesn’t this time, as the index of coincidence is usually calculated on lowercase letters only and without any special characters or numbers.
Once we know this is English text with substitution cipher, we can try to guess the characters. As we see both lower and uppercase letters, it is a good guess that the characters at the beginning of the ciphertext “%96” translate to “The”. We can work from there and guess almost all of the characters easily.
Once we are done and left with characters still unknown, the right way forward is to calculate the distance between the cipher and clear text characters. Once we realize it is a constant 47, we know this was ROT47 all along.
Hint1: When calculating the index of coincidence or using an automated substitution cipher breaker for the text, it is good practice to remove the last part of the ciphertext, which usually contains random characters (a.k.a the flag).
Hint2: The challenge name was a big hint, which we only realized afterward. Salad referred to Caesar, and “x/2” referred to half. Half Caesar is exactly ROT47.
Hint3: We have no idea why some characters were red. Probably, this was a false flag.
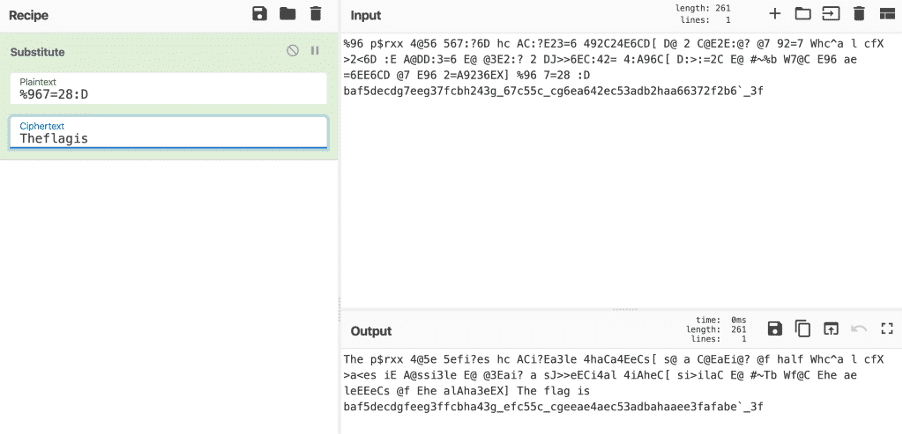
Flag: 327d56458f668bf7439acb80ef4dd4048e62eca64db253a922eebfa7a3e10b7 (The original flag was the same string with a space at the end, but the organizers later changed it.)
Challenge of the Challenges – Bonus
As a reward for reading the instructions, please note that if you ever find a flag with value, you must submit the string encoded with ROT13 to earn credit.
There were hexadecimal values hidden within the instruction page.
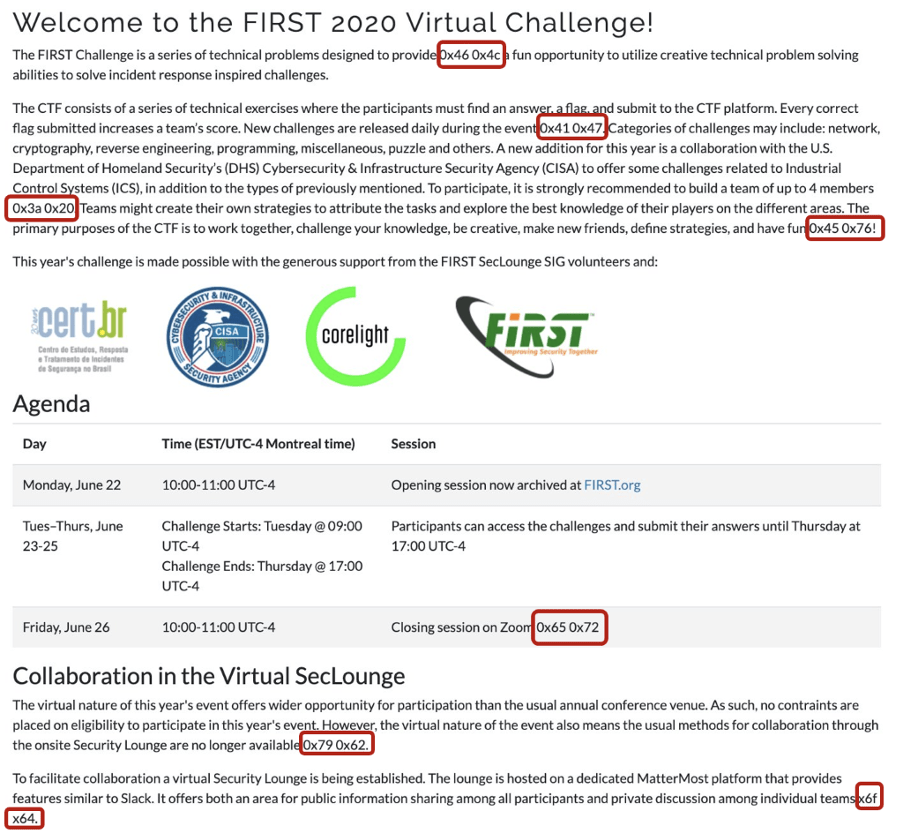
Collecting these we got the following: FLAG: Everybody should read the instructions before start!
The ROT13 encoded version of “Everybody should read the instructions before start!” was the flag.
Flag: Rirelobql fubhyq ernq gur vafgehpgvbaf orsber fgneg!
The Museum
This Museum hides a very important secret for you.

Since it is a crypto challenge with an image, we suspected that steganography was used to hide the flag. We just had to find the right algorithm and the key.
As a first step, we looked for the building on Google Maps. Comparing the original building with the image, we found our first clue.
The first picture is from the image in the challenge; the second one is the original.


We suspected that the value 1903 had something to do with the key that we were looking for.
The next step was to find the right algorithm.
We spent quite some time and tried several tools to find the right direction.
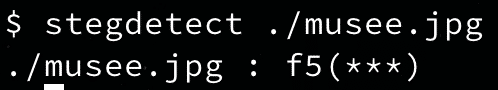
Stegdetect was one of the most useful tools, it suggested that the algorithm we are looking for is F5.
We used an F5 steganography decoder found on GitHub. We spent most of the time guessing the right password. Since 1903 didn’t work, we tried several other passwords until we finally found the right one. The password was 219036, since the ornament around the year 1903 was interpreted as numbers.
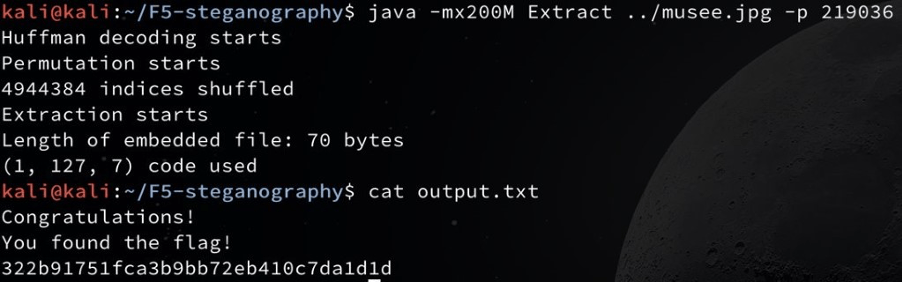
Flag: 322b91751fca3b9bb72eb410c7da1d1d



