Assessing Apple’s Update to Rotating MAC Addresses

This article was written in collaboration with Shimon Goulkarov, the SVP of Product R&D, and Karolis Povilavičius, the Senior Device Intelligence Lab Manager.
Apple’s latest updates feature new privacy enhancements for its operating systems, including iOS 18 and macOS 15. Since the updates impact how and when Apple’s devices randomize their MAC addresses, and will affect not only iPhones and iPads, but Apple Watches and MacBooks too, we have decided to publish this short article addressing the changes.
First of all, we want to note that Apple is pushing the market away from insecure, legacy protocols. CUJO AI supports this move towards better network security and end-user privacy. Furthermore, the updates and changes have little to no effect to the services that CUJO AI enables, including cybersecurity and content control solutions.
However, many network service providers (NSPs) use solutions that rely on MAC addresses as unique device identifiers. As we’d noted in the past, privacy enhancing technologies can cause customer experience issues for those network service providers who do not use modern device intelligence as a foundation for their services.
Updates to MAC Randomization on Apple Devices
Updated Private Wi-Fi Address settings:
- Off – the device sends its hardware MAC address.
- Fixed – the device sends a randomized MAC address.
- Rotating – the device sends randomized MAC addresses which change every 2 weeks.
New: Private Wi-Fi Address settings are introduced on MacBooks with this update.
Default behavior:
- Networks that are known to the device before the update will not get a new MAC address.
- New random MAC addresses will be issued to forgotten networks within 24 hours.
- There are now three “Private Wi-Fi Address” options for end-users to choose from: Rotating, Fixed, and Off.
- The default setting for networks with at least WPA2 security is Fixed, i.e., the device uses a randomized MAC address that does not rotate. No devices use Off as a default setting.
- Devices will randomize MAC addresses every 2 weeks on ‘vulnerable’ networks. The exact trigger(s) for the randomization are not disclosed. The default setting for these networks is Rotating.
- Changing the setting between Rotating and Fixed does not immediately change the MAC address.
Devices affected: Apple Watches, iPads, iPhones, MacBooks and other Apple computers.
Networks affected: public hotspots, open networks (OWE), WEP, WPA1, WPA1/WPA2 mixed mode, or TKIP.
Expect a Significant Number of Apple Devices to Issue New MAC Addresses
CUJO AI Labs continuously test beta versions of upcoming operating system updates. Their findings show that the upcoming privacy enhancements will affect some data points that are useful for home network device management, customer care, as well as merging duplicate device signatures whenever a device re-issues a new randomized (i.e., re-randomized) MAC address.
Initially, first iOS 18 beta versions did not have an Off option, emphasizing Apple’s is push towards more privacy enhancements. We expect this trend to continue.
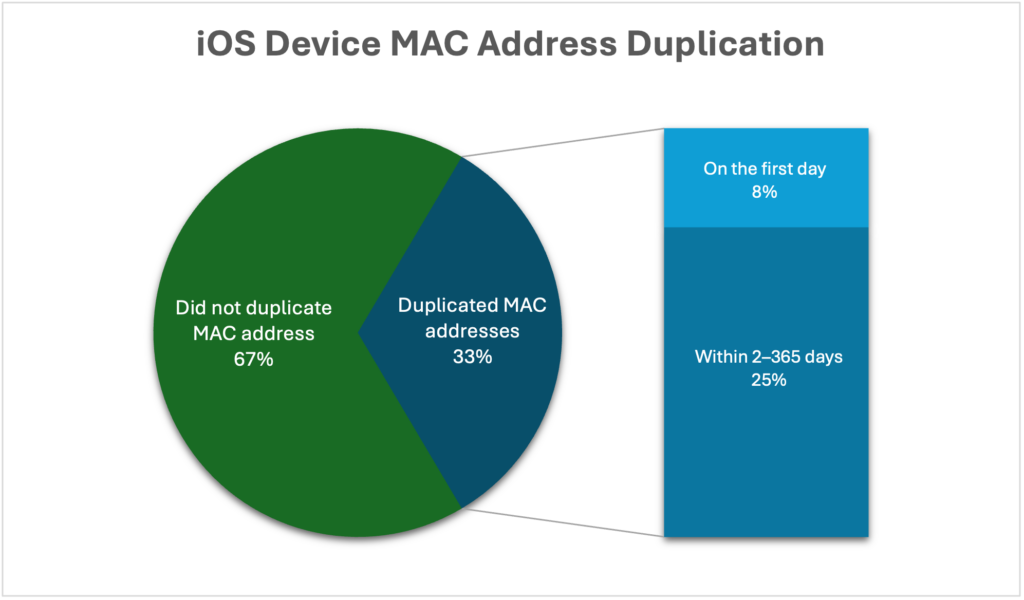
Data from millions of home networks running CUJO AI Explorer shows that almost a third of iOS had created duplicate MAC address signatures within 1 year. While around 8% of devices issued at least two MAC addresses on the first day (most had done this on networks with more than one SSID), around 25% did so within up to a year.
According to Apple’s documentation and our tests, devices that are away from a network for 6 weeks will also issue a new MAC address.
Again, our cybersecurity and content controls continued to function without disruption during the tests. Since there are no fundamental changes to how MAC address randomization works on sufficiently secured networks, the only significant change is that randomized MAC addresses will be used by a wider variety of Apple devices, especially MacBooks. Our device intelligence data shows that 26% of all consumer computers used in North America and Europe are made by Apple.
We expect more privacy enhancements to come from Apple and other vendors in the near future. CUJO AI continuously strives to enable the greatest customer experiences by staying on top of trends, which includes testing every major OS beta releases for relevant changes.
The Effect on ISP Systems
One of the most obvious ways Apple is breaking legacy NSP services is customer care. When the home network’s devices no longer show the vendor and device type information, customer care agents need more time to troubleshoot connectivity issues.
Some NSP value added services also rely on identifying a device and when a device is not identified certain policies or services cannot be applied.
Since networks that are known (i.e., the device has connected to them before the update) will not be impacted by the update, NSPs have some time before the issue snowballs with new users and devices onboarded to their networks.
Apple’s newest changes will break legacy systems that rely on stable MAC addresses. It’s extremely unlikely that network service providers will succeed in persuading over 50% of their customer base to disable MAC address rotation for their home networks. NSPs will therefore need another approach to solving device identification.
Device Intelligence Is a Foundational Technology
Device identification is becoming increasingly challenging for network service providers. To tackle advanced problems, operators need advanced solutions. Our device intelligence has a proven track record with leading telcos and over 60 million home networks under it’s belt.
The ISP Checklist
To scope the impact Apple’s updates might cause, we suggest NSPs look at:
- How many of their customers are running WPA1 or other legacy protocols on their networks.
- How many active legacy devices are on their networks and are incapable of connecting with WPA2. This segment includes retro tech enthusiasts which are a key customer demographic for NSPs.
- Customers who use legacy CPE.
- How many Apple devices are on their network, and
- How many new Apple devices join their networks every month.
The latter two points are hard to answer without a reliable device identification solution. Based on our aggregated device intelligence data, new devices from Apple connected to 78% of home networks in North America, while 23% of households used five or more different types of Apple devices, such as computers, smartphones, smartwatches, etc. in 2022-2023 (this number includes guest devices). Of course, the proportion of Apple devices in a given NSP’s user base can vary.
No Impact to CUJO AI Sentry and Compass
Upcoming changes have no effect on our solutions, as Sentry will continue to provide multi-layer protection for all devices on secured networks. Network-wide content controls that are applied to all devices will also function without impact.
We have discussed MAC address randomization back in 2020, when Apple released iOS 14. Since then, Android and Windows devices also increasingly randomize MAC addresses and use other privacy enhancing technologies. These changes are pushing network service providers to look into more advanced device identification solutions, such as CUJO AI Explorer.
Our device intelligence solution helps the leading network service providers in North America and Europe and improves the identification of tens of thousands of diverse connected devices. Explorer uses dozens of unique data points and device connectivity patterns to identify devices and has identified over 3 billion devices to date. As a cross-architecture solution, Explorer is unmatched in the industry.
