Using Artificial Intelligence in Telecom Security

Today, 75% of enterprises rely on AI-based platforms and solutions for network security. Large telecommunications networks are no exception, thanks to the tangible benefits AI-driven network security offers operators and end-users.
Security, along with telecom data analytics, is among the main issues that the telecommunications industry’s investments in AI are tackling right now. This article will give you a short overview of how this technology works and why network service providers use it.
Want to learn more about the technical aspects of AI network security and device protection for your end-users? Read the Sentry white paper.
How AI Works in Securing Telecommunications for End-Users
Artificial intelligence is a decision-making program that is more versatile than traditional solutions: it goes beyond rules-based approaches and can prevent some novel threats thanks to machine learning, pattern detection, and rapid response time. AI is particularly useful for preventing both traditional malware attacks and novel, rapidly changing threats.
Remote access attempts are a good example: hackers might not target protected devices, opting instead to attack vulnerable IoT devices and gain control of the whole network. If IoT devices are exposed to the internet directly, there is nothing that can reliably stop remote access hacks, as end users rarely have all devices up to date and patched for security flaws.
Protecting every IoT device separately is not feasible, as most are too primitive to use antivirus software, but a network-based AI security solution can detect patterns in remote access attempts and rapidly prevent the threat from escalating.
Applying AI to Telecom Security: Automation and Scale
Telecommunications networks are some of the most data-intense businesses in the world due to their scale. Tier 1 internet service providers have hundreds of millions of devices connecting to each other constantly. Our own solutions are deployed to protect more than 1 billion devices, and that number is growing every month.
The scale at which AI performs network security tasks is vast: our security measures have prevented billions of remote access attempts during the shift towards work from home in 2020.
The variability of these data sets is beyond the scope of humans or rule-based algorithms. The attack surface on such networks is simply too large. As protection can be deployed on the whole network at the firmware level, it is possible to fully utilize edge computing to bring a much safer digital life experience to users without any significant delay.
Challenges improve artificial intelligence
Any AI model becomes better with scale and iterations, making it a more robust solution for automated network security. The protections are varied: from wholesale home network endpoint protection to individual device protection through prevention of invasive technologies and individual attacks.
Enterprises are relying on AI as the foundation of their security automation frameworks, as the cybersecurity sector struggles to attract enough people for the job.
Privacy-Respecting Security
CUJO AI Sentry analyzes meta data to discover potential threats. The end-user’s data stays encrypted and packaged, while the AI recognizes how their device connects to the internet and allows network operators to identify and classify it. This is an exceptionally important element in network security that would not be possible without robust AI device intelligence solutions.
Once a device type is identified and classified, any suspicious activity can be stopped quickly. For example, if a home webcam suddenly starts talking to suspicious servers, the AI protection can terminate such connections. Likewise, when a smart phone starts connecting to thousands of servers a minute in the middle of the night, AI shuts down the connection pattern to prevent what is likely a botnet activity.
As distributed denial of service (DDoS) attacks become more sophisticated and themselves reliant on AI models, network managers need to rely on AI algorithms to stay ahead of the malicious actors without waiting for legacy anti-malware software to detect the attack once it’s already reached the target device.
Growing Investments in Artificial Intelligence for Cybersecurity
71% of organizations report spending more on AI and machine learning for cybersecurity than they did two years ago. As many experts know, malicious actors are using AI algorithms themselves, and it therefore becomes essential for large networks to use the very best machine learning and artificial intelligence solutions to protect their networks.
Again, the quality of those solutions depends greatly on scale, as the more devices and behavior patterns the AI solutions observe, the better they become at protecting networks. You can read more about what drives AI investments in the telecommunication industry in Ivar’s article.
AI Flexibility – a Core Feature for CyberSec
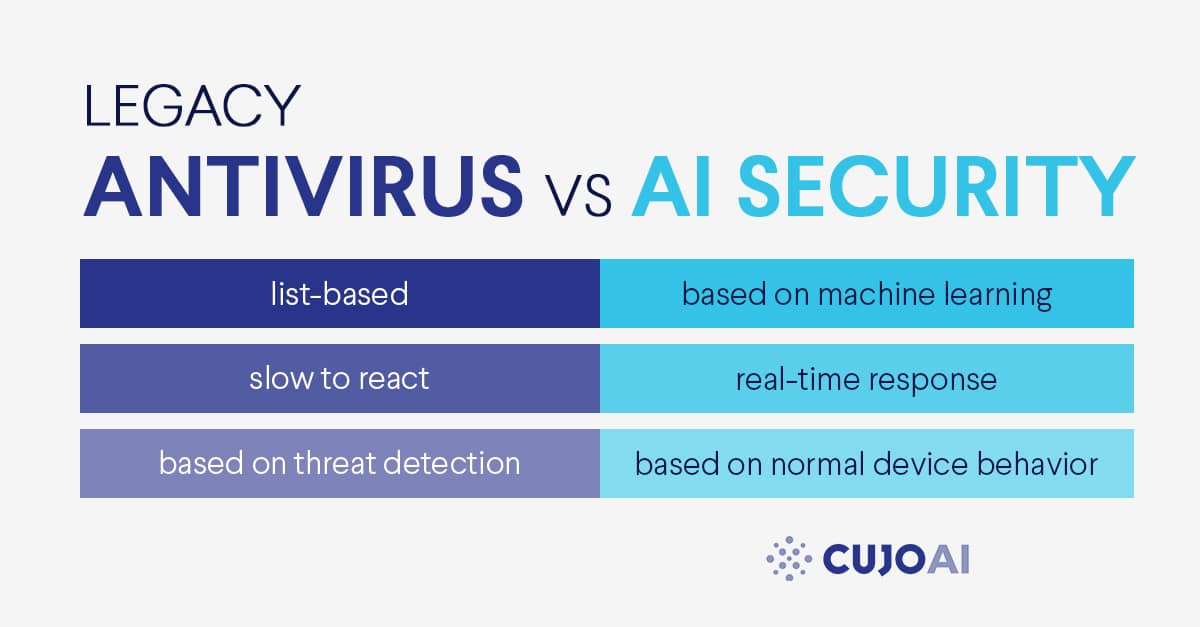
Legacy security measures were reactive. In essence, these we blacklists and signature lists in firewalls or antivirus software. There used to be a significant lag between when a novel threat emerged and when those solutions were updated. In that time frame (which could last anywhere from hours to months) the users and networks were extremely vulnerable to breaches. In the mean time, unprotected IoT device numbers grew to make up the majority of devices on provider networks.
There still are many valid and useful malware detection solutions using legacy approaches, but the discovery of new threats and attack vectors is always a reactive approach. AI, on the other hand, works proactively by knowing how a certain device should behave and detecting any uncharacteristic behavior. In that sense AI is not reactive, it is adaptable, flexible, and quick-acting, when faced with novel threats.
If you want to discuss customer-facing AI network security as a value-added service for your end-users, do not hesitate to contact us.
Want a more granular explanation of how AI-driven network security works in the real world? Access our in-depth network security white paper.
