Top IoT Security Threats – IoT Chronicle, June

Earlier this year, CUJO AI announced that its coverage reached more than 1 billion connected devices. This scale gives us a unique insight into the IoT landscape. In May, we released a comprehensive report on the statistics of connected devices in North America, recent trends, areas of growth, and challenges, including the impact of the COVID-19 pandemic.
In this article, we provide a peek into the top IoT security threats. We will also tell you about the activities our research team has been involved in recently: sharing findings with the community at conferences, and expanding knowledge and skills in various competitions.
The last section will cover our threat research topics, where we detail our predictions of future cyber-attacks based on the data we see, followed by a short summary of our recent honeypot research. Finally, we will close this article with some insights into the scene of car hacking tools.
Top Security Threats in June 2021

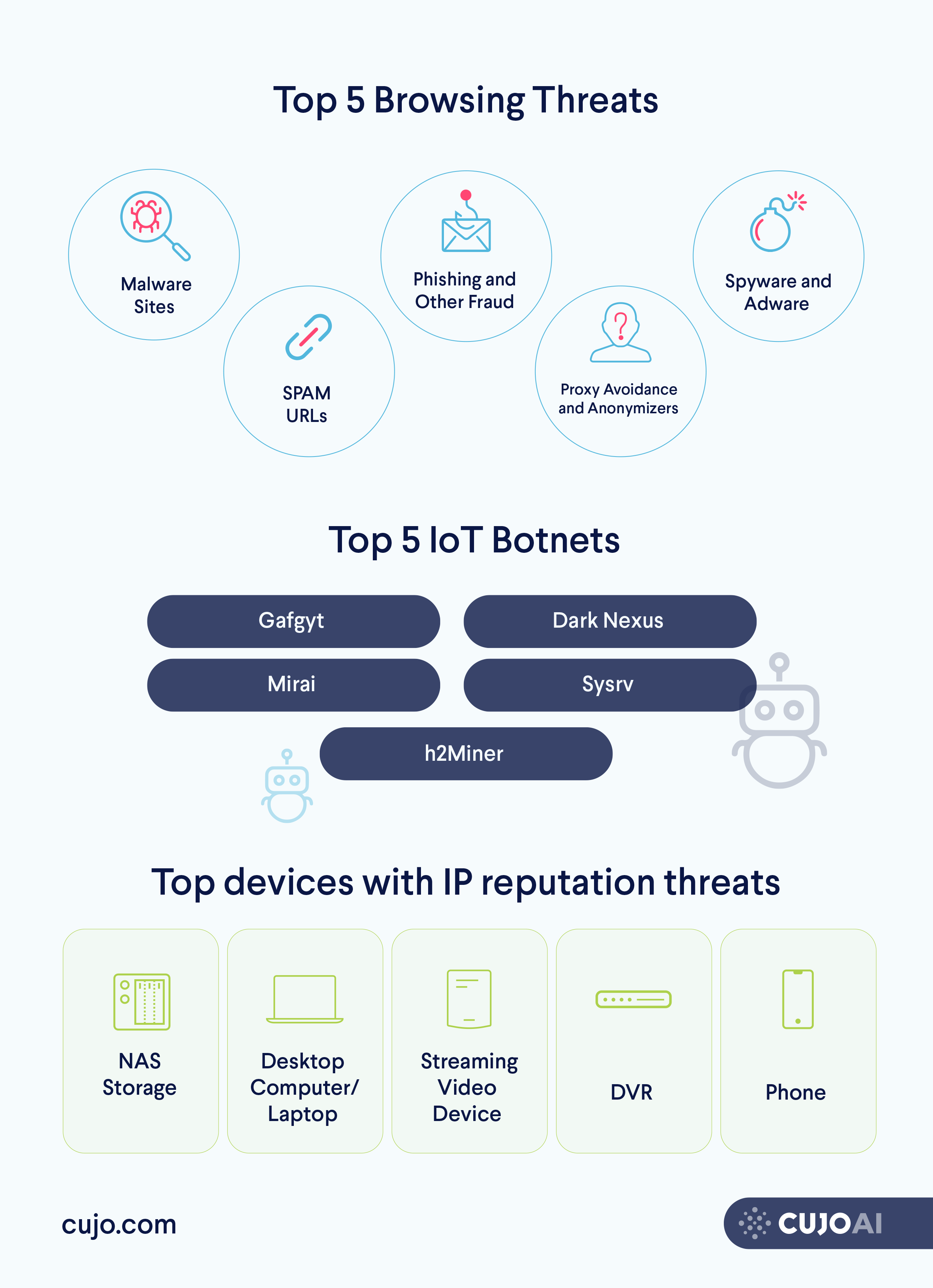
CUJO AI Labs Activities and Announcements
FIRST SecLounge Virtual CTF 2021 – 2nd place
Our team of 4 competed at the FIRST SecLounge 2021 Virtual CTF (Capture the Flag) event, which was organized throughout 7th – 9th of June. It is held annually by FIRST organization, which incorporates a network of computer security incident response and security teams. During the three-day-long competition, participants solved challenges in various categories such as network, cryptography, reverse engineering, programming, etc.
Our team – Albert Zsigovits (Threat Researcher), Dorka Palotay (Senior Threat Researcher), Filip Savin (Senior Security Engineer), and Zoltan Balazs (Head of Vulnerability Research Lab) – took second place at the CTF event, solving 45 different challenges in various categories.
We will soon publish a comprehensive write-up on how we solved the challenges: stay tuned!
DEFCON2021 CTF Competition – 46th place
For CUJO AI Labs, the May of 2021 started out with an exciting event. On the first weekend of the month, the CUJO AI Labs team of 9 participated in the DEF CON Quals CTF (Capture the Flag) competition, under the name of CyberpUnk Jiu-jitsu Otters, and reached 46th place out of 433 teams.
For first-time players with a relatively small team, it was a great achievement and, more importantly, we had a great time and learned a lot during the two-day-long event. If you are interested in the kind of challenges in such events or just enjoy reading about quantum computating, you can find our solution for one of the challenges here.
VirusBulletin 2021 Conference Speakers
This year’s VirusBulletin International Conference will be organized online. The two day conference will present the latest research about malware, malicious actors, and threat intelligence. It will take place in October 2021, and the selected presenters were announced last month. CUJO AI Labs will be represented in two sessions.
- Dorka Palotay and Albert Zsigovits will present Reversing Go binaries with Ghidra
- Zoltan Balazs will hold a workshop called Workshop: IoT hacking 101.
Machine Learning Security Evasion Competition 2021
The annual machine learning (ML) security evasion competition invites ML practitioners and security researchers to compete in two separate tracks: the Defender Challenge and the Attacker Challenge.
The Machine Learning Security Evasion Competition 2021 (MLSEC2021) is a collaboration between Hyrum Anderson, Principal Architect and Ram Shankar Siva Kumar, Data Cowboy in Azure Trustworthy Machine Learning at Microsoft, Zoltan Balazs, Head of Vulnerability Research Lab at CUJO AI, Carsten Willems, CEO at VMRay, and Chris Pickard, CEO at MRG Effitas to allow researchers to exercise their defender and attacker muscles against ML security models in a unique real-world setting.
The contest is designed to spotlight countermeasures to malicious behavior and raise awareness of the various ways in which threat actors can evade ML systems.
To participate in either of the challenges, individuals or teams may register at https://mlsec.io anytime during that challenge’s window. Prizes will be awarded for each of the challenges. To win, researchers must publish their detection or evasion strategies. The winners will be announced at the beginning of October.
IoT Security Threat Research: Cyber-attack predictions
Growing media reporting and general public attention to cyber incursions, data breaches, and malicious activities related to the ongoing pandemic will continue raising awareness of cybercrime in the post-pandemic world, along with financial and reputational losses that it causes.
Ransomware tactics are evolving
Current trends show that attacks will continue to grow in complexity and become more sophisticated, as opposed to using new attack vectors. We also expect ransomware to evolve. 2020 and 2021 are big years for ransomware, and it will continue to grow in sophistication. Attackers move towards a more complex operational approach: infiltrators leak sensitive business data before deploying ransomware on the target network, in order to raise public awareness and to damage the breached company’s reputation. We can expect ransomware gangs to find new ways of defrauding businesses in the near future.
Malware-as-a-Service and Ransomware-as-a-Service have grown significantly in the last couple of years. It is likely that the margin between malware developers and malware operators will widen in the upcoming 2-3 years. Separate groups will focus more on the development of malware and adopting new business models to rent or sell it to operators, who carry out the attacks.
Cyberattacks might target remote employees
Platforms like Discord and Slack open new, blind spots in home users’ networks, as they are being targeted by attacks more often. Threat actors will continue looking for new opportunities and vulnerabilities in emerging social media and communication platforms.
Issues with remote work security in home offices and hybrid work arrangements have already shifted and will continue to shift the attack surface from company and business networks to NSPs and individual home networks. We also see that IoT continues to grow in importance and popularity in connected homes. As a result, the attack surface on connected homes continues growing with IoT security threats, to the point where we will see significant new risks for individuals, their households, as well as their employers in the near future.
Key physical infrastructure might become a cyberattack vector?
Systemic physical vulnerabilities should not go overlooked either, as seen in the Brexit-related parcel fraud. Post and shipping has become critical infrastructure for everyday shopping habits, which makes it extremely likely that shipping and parcel companies and their infrastructure will be subject to increased attacks. An example of such attacks could be targeted parcel snatching operations, where legitimate devices are swapped with counterfeit or compromised ones.
Supply chain attacks
New supply chain attacks should become more frequent after the findings around the SolarWinds espionage campaign spark a proliferation in new, and likely more advanced, supply chain attacks. Cybercriminals will increasingly seek to exploit and defraud users with SMS phishing messages – smishing – that have seen a steep rise in abuse during the pandemic.
Last, but not least, once it matures 5G will open the attack surface for industrial IoT as well as home IoT.
IoT Honeypot research
Our team conducted a 3-week-long study analyzing attacks from honeypot logs, trying to understand the recent trends in credential-stuffing and brute-forcing attacks. We had also studied new attack schemes happening in our honeynet.
As we discussed in our previous article on the Genetics of a Modern IoT Attack, an IoT attack usually starts by either exploiting a vulnerability in the target devices or brute-forcing device credentials.
Back in 2016, the success of the Mirai botnet was due to only 61 hard-coded username-password pairs.
For our experiment, we used a few simple SSH honeypots to collect data. We use honeypots to attract threat actors and observe their actions in the controlled, monitored environment that they believe to be a production system. From a researcher’s perspective, the aim is to let the attackers spend a long time inside the honeypot, to have them reveal attacker toolsets and techniques, or even simple Indicators of Compromise. To truly work, the honeypot needs to run and emulate critical components of a production system to be attractive enough for the attacker to attack the system.
During our investigation, we saw 18,422 unique usernames and 63,955 passwords in the honeypots. Attackers have an easy job with credential attacks, as ready-made password lists are all over the internet. They can use leaked lists of passwords seen in malware attacks (e.g., Mirai), credentials from data breaches, dictionaries of the most common username-password pairs, or publicly known default passwords of various devices (e.g., default router credentials).
When it comes to attacking IoT devices, weak credentials are only half the story. Remote access to these devices is what enables adversaries to execute successful attacks. It was the key to Mirai’s success when internet-facing devices were “protected” with default credentials only.
We have investigated the most popular IoT devices among our users, focusing on IP cameras, routers, and NAS devices. Based on their public documentation, we found that the user usually chooses credentials during set up or when the default password change is enforced upon first login. For routers, remote access is restricted and only allowed using a password chosen by the user. However, it is still possible that some users set a weak password.
Read the full analysis of our honeypot research here.
Vehicle hacking
The smartification of things expands into more areas, and the automotive industry is no exception. Nowadays, full-fledged *nix-based systems are used for the infotainment systems as well as dashboards. Feature-rich OS drastically expand the attack surface and have platform-specific vulnerabilities.
On the other hand, some users try to exploit the existing systems to install additional functionality or customize the systems. This both voids the warranty and might make a specific vehicular system more vulnerable.
We have recently found traces of users downloading such toolsets and decided to look into the car-hacking scene. We introduce the three most prominent system hacks in the following section.
Honda Hack RAT
One of the most controversial cases is called HondaHack. HondaHack is a commercial project that maintains and sells software, which allows the owners of specific Honda models to install additional features to their car’s dashboard. Interestingly, the maintainers chose to use the term “hack” instead of a more neutral term (e.g. “unlock”). This fact, alongside many other suspicious traces (such as the ability to execute commands retrieved from the command server based in China), raised suspicion and discussions from the cybersecurity community.
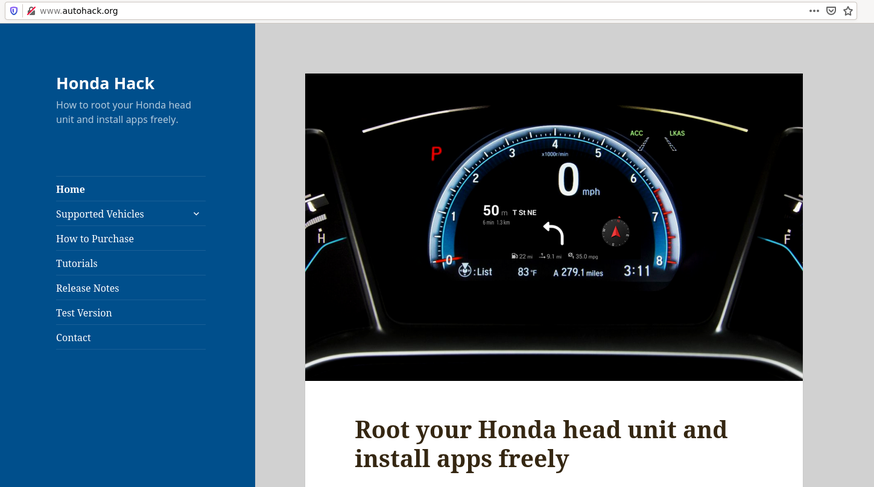 Landing page for autohack[.]org
Landing page for autohack[.]org
Cybersecurity researcher MalwareMustDie reverse engineered the project and evaluated the whole piece of software as being a Remote Access Trojan (RAT). This type of malware can retrieve commands from the remote Command and Control server and execute them. We cannot yet determine whether this is used for malicious purposes or not, but the possibility is there. More information on the analysis of the binary can be found here. Note that the developers of HondaHack responded and said the project is similar to jailbreaking an iPhone, and that there is no significant threat for its users.
Even though it is still unclear whether the project’s primary intention was to act as malware, we strongly suggest that users not modify their existing vehicular systems. Such activity poses a threat to both the data traveling through the vehicle (i.e., phone calls, contact lists, SMS messages) and the safe operation of the whole vehicle.
Nissan Bosch infotainment system hack
Recently, a security researcher named ea found a way to gain root shell access to all Nissan models produced from 2015 onwards, which used the lcn2kai infotainment system. They did it via an exposed Serial port, which let ea enable an SSH server. Since it did not have a root password, the user could easily log in to the infotainment system with root permissions.
However, as this vulnerability was found in late January 2021, there are no publicly disclosed modifications, apart from the PoC (Proof of Concept) released by ea, which allowed the vehicle to log GPS coordinates to the GPX file internally. Additional extensions will likely appear soon on various Nissan owner forums.
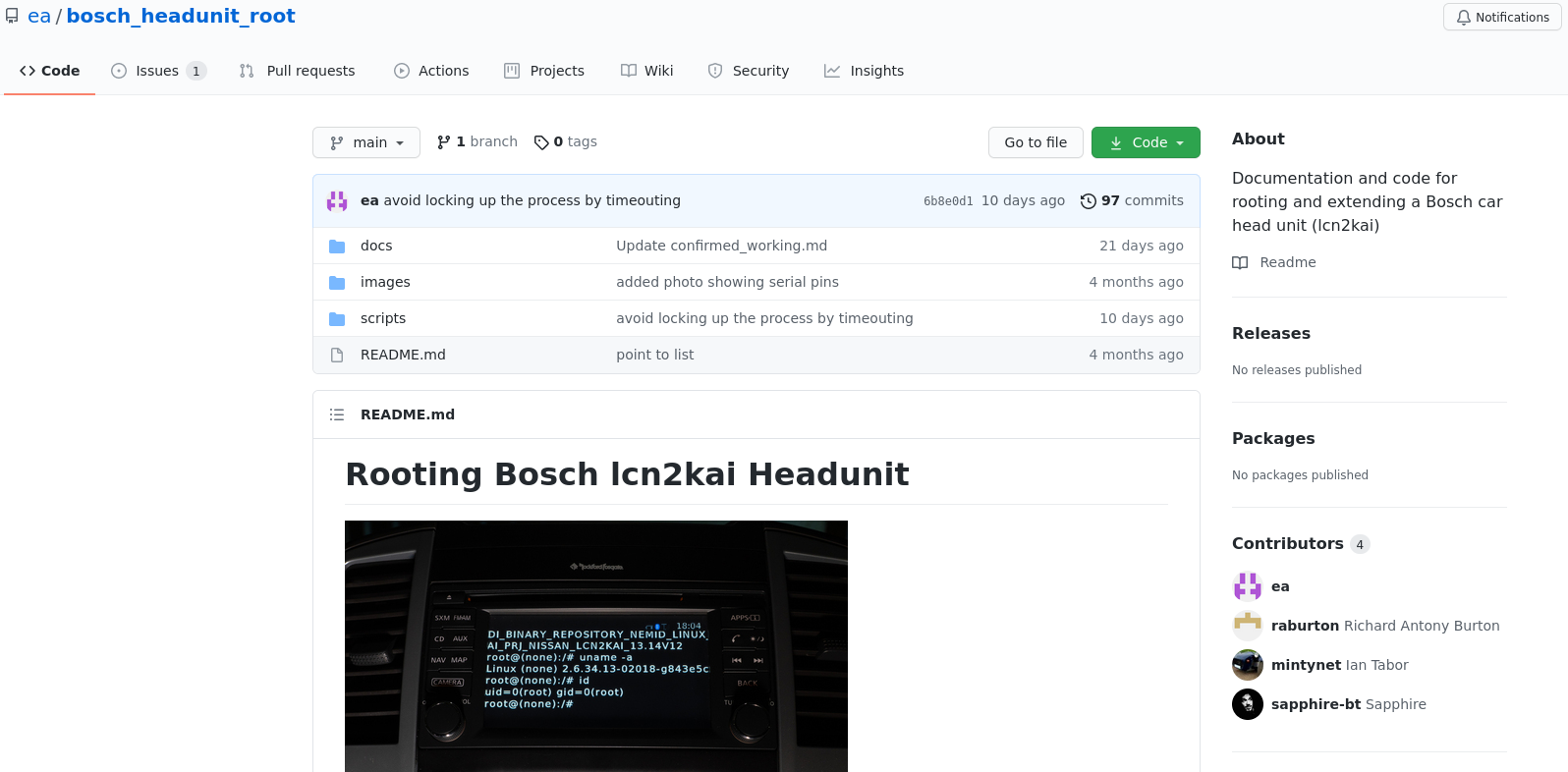 Github page for the Nissan Hack
Github page for the Nissan Hack
Mazda AIO Tweaks
Like HondaHack, there is an infotainment system upgrade for Mazda – Mazda AIO Tweaks. However, while the HondaHack is closed-sourced and commercially distributed, Mazda’s project is community-based, well documented, and free for everyone. No cybersecurity vendor has marked any of Mazda tweak binaries, nor the domains as being malicious. Therefore, this project could be treated as legitimate. However, while these tweaks are not malicious, using them will still void your warranty.
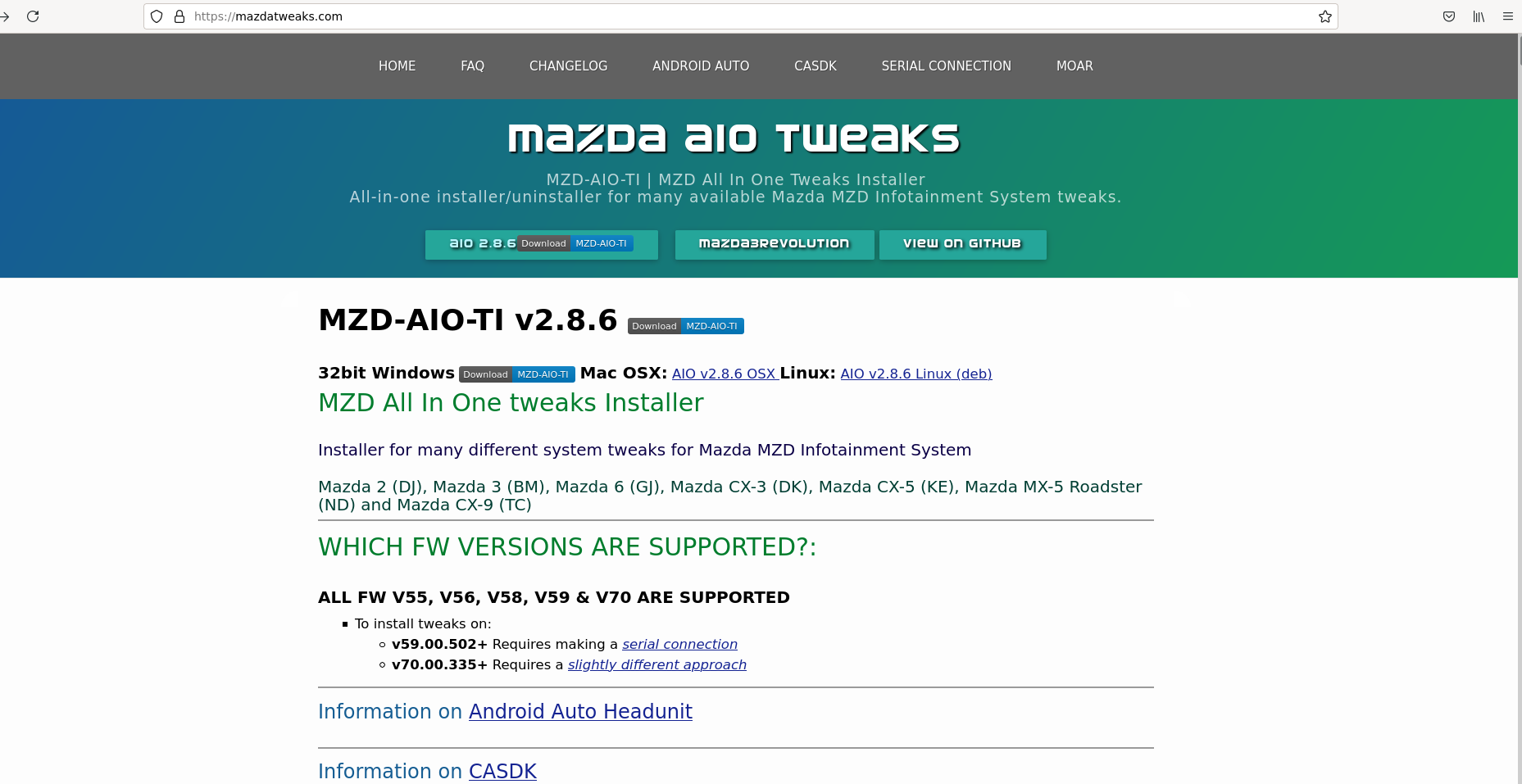
The landing page of the official Mazda AIO Tweaks hack website
The car “infotainment extension” market security review
Even though these are only 3 examples, the whole “infotainment extension” market could be differentiated into three categories:
- Suspicious binaries are redistributed via car owner forums. However, these usually do not have any documentation associated with it. HondaHack could be attributed to this group, as it comes as a binary, categorized as malicious/suspicious. These types of software are most dangerous since they could impact the CIA triage of the entire system and physically modify other vehicular subsystems. However, if such binaries perform a callback to the CnC server and the car is connected to the home network, the CUJO AI security system would thwart the possible risks by blocking such malicious connections.
- The well-maintained open-source project, such as Mazda AIO Tweaks. Such projects provide excellent documentation, installation guides on specific vehicle models, and even officially released source code. These extensions might void your warranty, but they are less likely to be malicious.
- Unfinished/unsupported projects, such as Nissan Bosch infotainment system hack. These kinds of projects provide a major part of the code, but the end-user needs to add/modify certain parts for the working product. Installation of such a piece of code might brick the infotainment system, therefore damaging the whole vehicle.
Enjoyed this IoT Chronicle? Follow CUJO AI Labs on Twitter @CUJOAILabs and subscribe to our newsletter below.
