Rapid Response: the Rise of Suspicious Websites at the Start of the Israel-Hamas War

Malicious actors often use events that draw the public’s attention to promote scams. We have previously reported on the malicious activities targeting consumers during the COVID-19 pandemic and Russia’s war against Ukraine. This year, we observed a similar spike in suspicious sites after the Hamas attack on Israel.
In the aftermath of the October 7th attack, the number of visits to websites related to Israel, Palestine, Gaza, and Hamas increased three-fold. In an environment that garners a lot of support and drives donations, both legitimate and fraudulent websites can be set up within hours.
After the initial attack, the number of unique websites that mention support and donations to either Palestine or Israel continued to grow. In October, almost a third of these websites had new domains and asked for support in a suspicious manner.
Spike in Visits to Israel-Palestine Related Websites
Our data shows a three-fold (290% to 370%) increase in visits to websites related to charities, activist and support organizations in the week after October 7th.
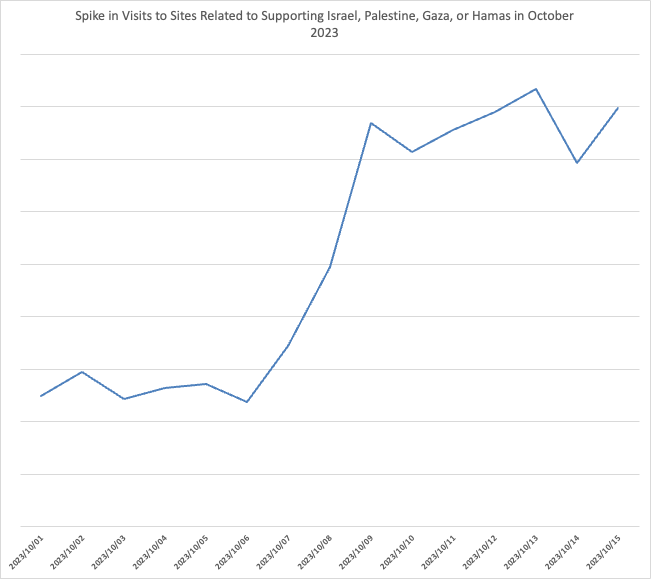
This data includes legitimate and suspicious websites and shows the scale of the interest that a shocking event can have. A highly engaged audience such as this is a convenient target for malicious actors: the urgency and willingness to get involved withhold is built in.
New Websites, Suspicious Websites
To have a better idea of how quickly the web reacts to such an event, we looked at when these websites had been registered. On October 22nd, almost a third (30.9%) of all websites that users were visiting had been created after October 7th.
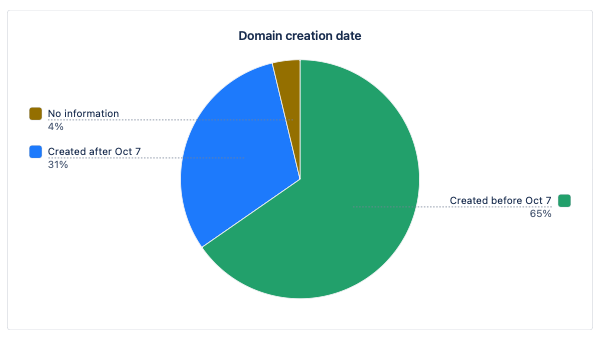
Most (54.8%) of these new websites were trying to attract donations. Our researchers reviewed a large sample of these sites and noted that many were poorly designed and looked suspicious. As a rule, the most trustworthy sites were directing visitors to legitimate charities or non-profit organizations.
16% of the websites asked for donations in cryptocurrency, 7% sold t-shirts or other accessories as a form of donation. Around 10% of the websites had been started with page builders and were left unfinished.
A significant number (around 23%) of the new websites no longer existed on October 22nd, when this analysis started. These websites were either parked, suspended, not loading, or were redirecting visitors to unrelated websites. Our assumption here is that a significant number of these websites were fraudulent.
Zooming Out
We repeated our analysis in December to compare our findings with data from the initial analysis to see how the traffic dynamics and those new websites changed over time.
Overall, traffic to similar websites fluctuated around the new baseline that is three times larger than before the October 7th attack. In November, users visited a much wider range of domains (we saw three times as many domains being accessed between October 7–December 1 than between 7-22 October), but the number of domains registered after October 7th stayed roughly the same.
As a result, in early December, domains that were registered after October 7th made up just 12.6%.
It is clear that the highest level of suspicious activity happened during the first week of the war, where the sense of urgency and ambiguousness was highest. Malicious actors jump to the opportunity to abuse painful experiences and scam good-willed people out of their money.
To protect people who do not evaluate the organizations they donate to, cybersecurity solutions have to rapidly detect and analyze new websites to alert users about suspicious sites almost instantly, since these sites may stay up.
This is another example of a crisis being used for malicious activities. Phishing sites appear within hours of a groundbreaking event and are gone within a few days. Before a website is flagged and added to threat intelligence databases, most of the damage is done.
Kimmo Kasslin, SVP of Research Laboratories at CUJO AI
We bridge this gap by using machine learning algorithms that analyze websites for suspicious activity and stop thousands of threats every minute. If there’s one thing our years of experience in protecting millions of home networks have taught us, it’s that without approaches like these, cybersecurity solutions have little to no chance to identify and stop modern threats in real-time.
Phishing Protection
CUJO AI Sentry is a multi-layer cybersecurity solution that offers Safe Browsing protection to protect every user on a network. Sentry works on the home network’s router to stop connections to known malicious websites and uses our AI models to analyze previously unseen websites to protect consumers from phishing and other malicious websites. Sentry is deployed by some of the largest network operators in the world, and protects tens of millions of home networks, stopping over 8.000 threats every minute.
CUJO AI extends Safe Browsing protection for mobile devices outside the protected home network. Our data shows that malicious websites make up over 96% of all threats affecting mobile devices.
